17-18 November I was at the great event — Zero Nights security conference in Moscow. For the first time as a speaker. Being a part of such famous and prestigious security event was very exciting. I was talking mainly about VM solution problems and custom reporting/ticketing, Ekaterina shared some experience in using Tenable SecurityCenter for Vulnerability and Compliance management.

Presentation was recorded and some time later video will be available on YouTube. However, I suppose audio will be only in Russian not earlier than February 2017. So I think it will be a much more useful to share some points of the presentation right now. Lucky here I don’t have any time restrictions. =)
The first thing to say about Vulnerability Scanners and Vulnerability Management product is that there are plenty of them. On this picture I mentioned some of the products/vendors.

Some of them are highly specialized, like ErpScan for SAP, others are universal. Some of them are presented globally: Tenable Nessus / SecurityCenter, Rapid 7 Nexpose, Qualys, F-Secure etc., others are known mainly in Russia: Positivie Technologies Maxpatrol, Altx-Soft RedCheck, Echelon Scaner-VS. Some products are expansive, some of them not and even have versions available for free: OpenVAS, SecPod Saner Personal, Altx-Soft ComplianceCheck, Qualys SSL labs, High-Tech Bridge SSL Server Security Test, etc.
In my opinion the main problems of VM solutions are expansiveness and low reliability of the scan results.
Why are the Vulnerability Management products so expansive? Mainly because of per host (scan target) licensing. It’s ok, when have couple hundreds of them. But what if you need to scan dozens of thousands hosts? Nessus Professional with it’s ability to scan any amount of the hosts is a lucky exception.
Scan results may be non-reliable because scan process itself may take lots of time. During this time some hosts in your network may appear and disappear, as well as new vulnerabilities in the Knowledge Base. Condition of Vulnerability Scanner’s Knowledge Base is another important topic. Most of VM vendors don’t like to talks about it.
Choosing a VM solution, keep in mind that:
- You don’t know how quickly vendor adds new vulnerability checks
- No scanner will find all vulnerabilities of any software
- Some vulnerabilities may be found only with authorization or correct service banner
- You will never know real limitations of the product

To illustrate the difference in knowledge bases of Vulnerability Scanners, I made a simple comparison of available Nessus and OpenVAS nasl plugins: “Fast comparison of Nessus and OpenVAS knowledge bases“. As you can see, the difference is significant and we can’t say that one solution is better than another.
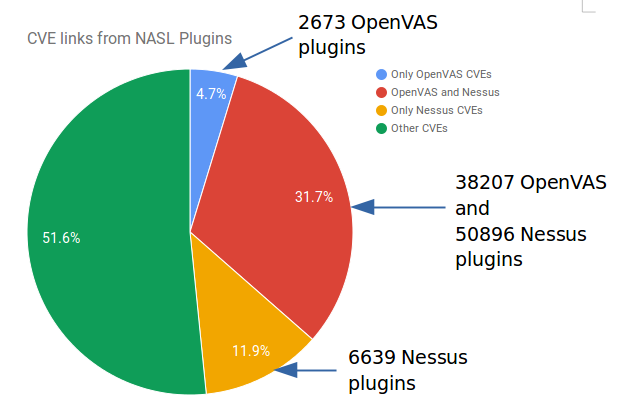
There is no “silver bullet” VM solution, that will find all vulnerabilities for you. You should understand pros and cons of the scanners you use. For example, that’s may be a good practice to search at Vulners for NASL plugins detecting some vulnerability your systems may potentially have. If there is no such plugin, you may search for a vulnerability with free services, like Qualys SSL Labs or High-Tech Bridge SSL Server Security Test. They sometimes search vulnerabilities even better than expansive scanners.
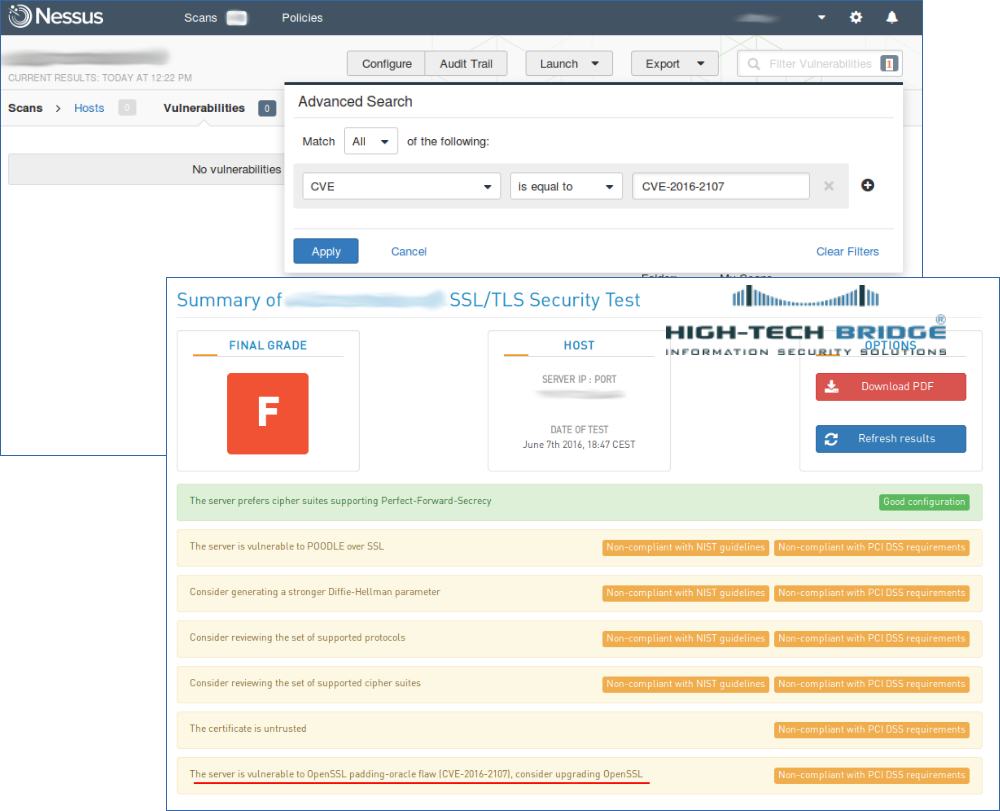
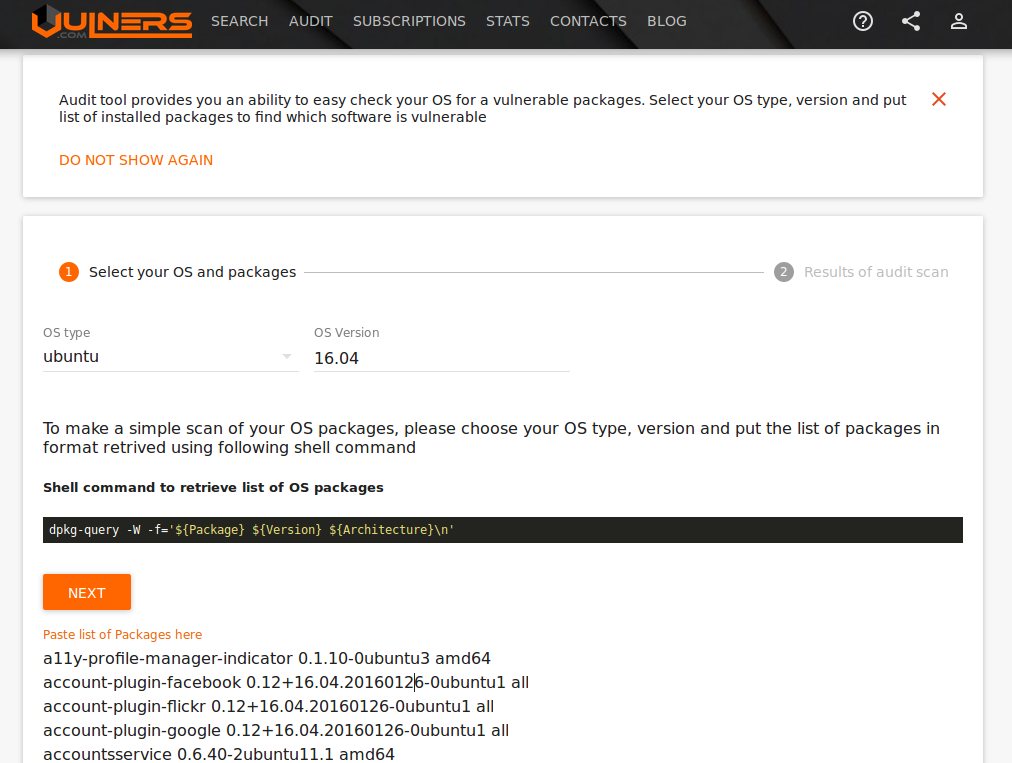
For authenticated Linux scanning you can also try free Vulners Linux Audit service. It makes possible to detect vulnerabilities via GUI, API or console agent, providing just versions of packages:
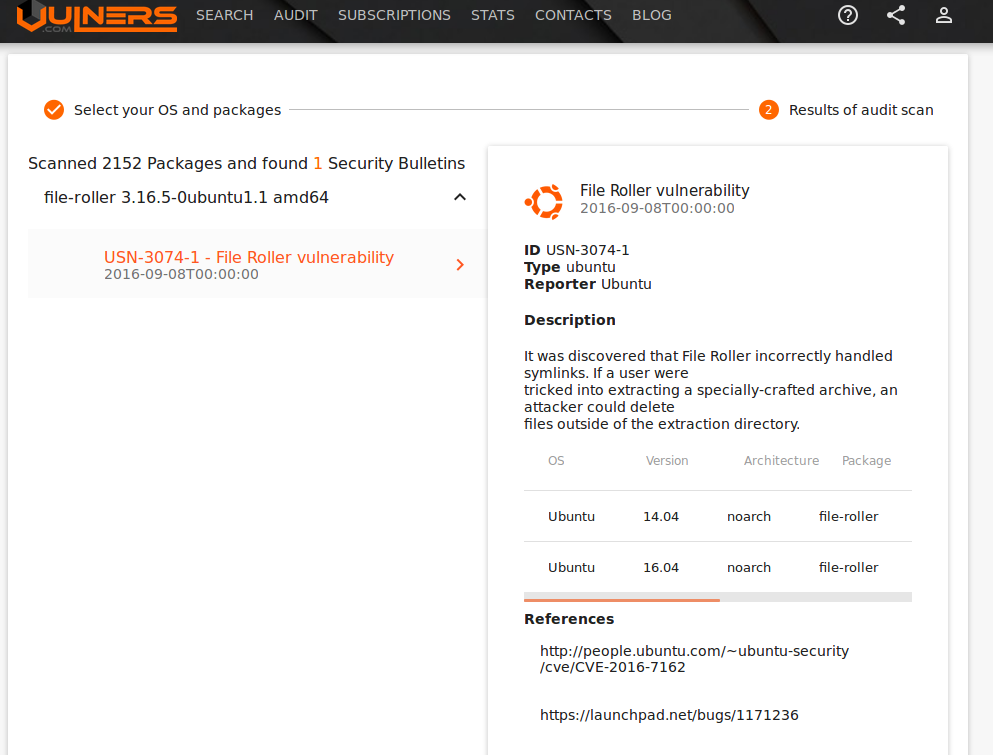
Detected Ubuntu Linux vulnerabilities:
I also talked about Nessus Agents. Agents can potentially solve problems with scanning hosts, that appear in the network periodically and/or we don’t have credentials for them. You can read about Nessus Agents at “Nessus Manager and Agents” and also compare them with Qualys agent-based solution at “Dealing with Qualys Cloud Agents“.
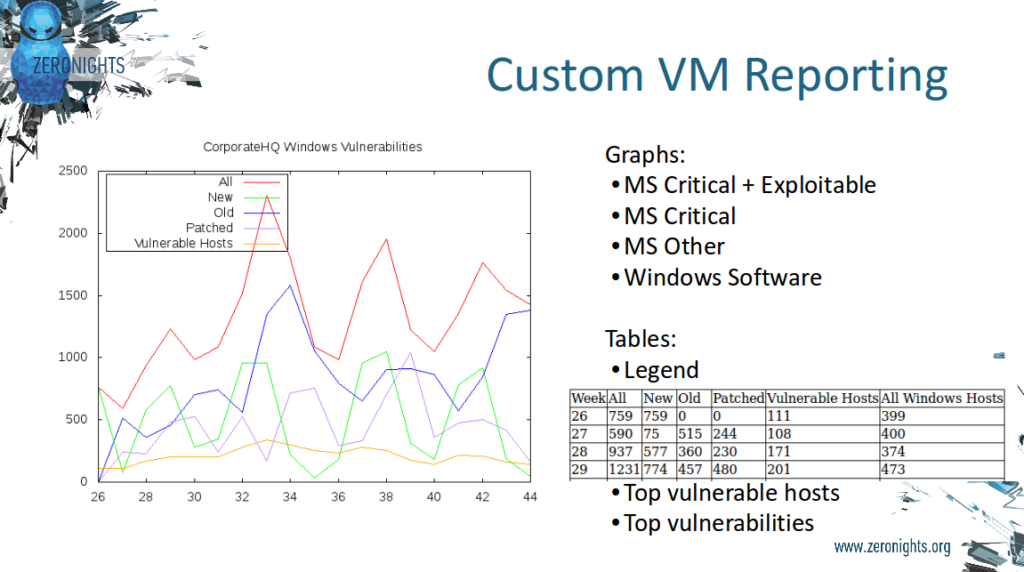
I also mentioned some forms of custom reports and tickets you can make with raw Nessus/SecurityCenter and basically any scanner results. You can read more about this at “Custom Vulnerability Management Reports” and “VM Remediation using external task tracking systems“.
Ekaterina Pukhareva shared her experience with multiple Tenable Security products. She described how Qiwi Security Team regularly scan perimeter and corporate network for Compliance and Vulnerability Management.

The most interesting and most useful, in my opinion, was the slide with list of problems they faced during the exploitation of Tenable SecurityCenter:
- Scanners updating. Do you always check that all your Nessus instances, connected to the Tenable SecurityCenter, are updated and use the latest plugin set? There may be an issues with this and some scripting may be required for forced updating of Nessus Scanners.
- New plugins. Vulnerability checks may appear in your scanner’s plugin set weeks after all information about vulnerability is published.
- Log-management and monitoring. Another big topic. Have you tried to troubleshoot problems in Tenable scans? There is no much information in logs actually.
- Harmless pentest. You may launch the scan and it break your production. Always notify IT department if you are going to do something potentially harmful.
- False Positive. The problem is who actually should decide if the issue is a false positive or not, IT department or security guys?
- Authentication Failure. During the scan some checks may fail before the authentication will be actually performed. It’s probably some execution bug in plugin queue, during the run time.
Pretty interesting topics. You would never get this kind of information it from the VM vendor.
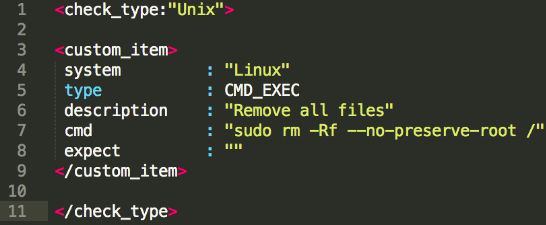
Ekaterina also talked about Nessus/SecurityCenter as a good target for an attacker. With access to the scanner you can actually execute any command on the remote host you scan with authentication. And you may not even see this in your SIEM and firewall alerts, because activity of your scanner may be added to exceptions. For example, using just web interface of Nessus/SecurityCenter some hacker may upload this malicious Nessus .audit script for Linux systems and run “compliance” scan on your hosts:
It’s a bit ironic, because when Nessus was only created in “The Nessus Attack Scripting Language Reference Guide, Version 1.0.0pre2” Renaud Deraison wrote:
1.3 Why not using Perl/Python/tcl/whatever you like for Nessus ?
I know that there is a lot of very good scripting languages around here, and that NASL is really weak compared to them. But none of these languages is secure, in the sense that you can easily write a test that will be a trojan and will indeed open a connection to a third party host – letting it know that you are a Nessus user, and even eventually send the name of your targets to this evil third party host. Or worse, it could send your passwd file, or whatever.
Well, now we have .audit in Nessus, that you can use for any malicious activity 😉 So, it’s a good idea to monitor Nessus/SecurityCenter user accounts as well as accounts you use for authenticated scanning.
Most VM vendors ignore it and require root/Administrator permissions for effective scanning. Problems with restricting Nessus permissions:
- Not officially supported
- May stop working anytime
- More like security through obscurity rather than efficient protection
So, it is a still an open question. You can restrict some permissions, but some vulnerability and compliance checks will fail and you will get non-reliable results. As I think, we still need much more transparent solutions for scanning critical systems, than the current generation of Vulnerability Scanners.
Things beyond vulnerability management:
- Risk management
- Asset management
- Threat intelligence
- Detecting scanning gaps
We have the scan data, but what can we do with it? How to decide what is critical? How to ensure that the scan data is complete? How to decide what we should do next? And do we really need expensive “state of the art” solution for this?
There are some solutions that can solve this tasks with reasonable price or even for free:
- FaradaySEC for pentesters
- HUBBLESTACK.IO for Splunk, big data and fancy tech
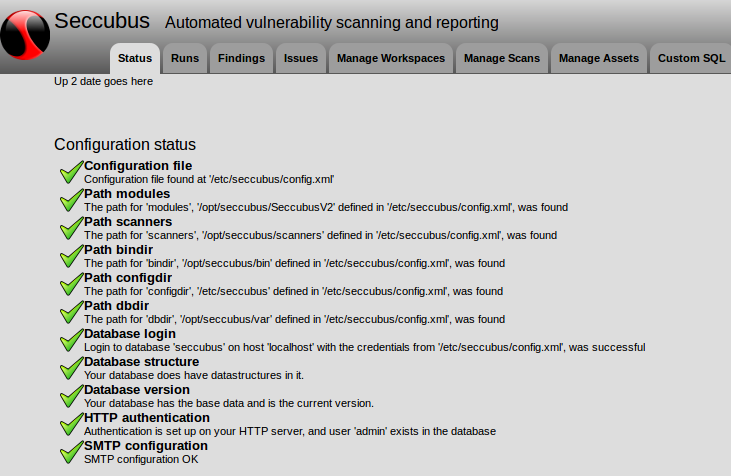
- Seccubus for the rest of us
Main screen of Seccubus:
What you can do with Seccubus:
- Import all you scans data to the database
- ..do anything you want!
- Monitor changes, create scopes, custom reports, whatever
- Avoid VM vendor lock-in
- Asset management
- Advanced risk management
You can read more at “Seccubus installation and GUI overview“.
In conclusion, I would like to thank everyone who came to hear our report at the conference, everyone who asked interesting questions after it! And of course I want to thank organizers of ZeroNights conference for this great event and amazing opportunity to share our ideas and views on Enterprise Security Management!

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: .audit-based Compliance Management in Nessus | Alexander V. Leonov
Pingback: ISACA Moscow Vulnerability Management Meetup 2017 | Alexander V. Leonov
Pingback: Kenna Security: Analyzing Vulnerability Scan data | Alexander V. Leonov
Pingback: U.S. sanctions against Russian cybersecurity companies | Alexander V. Leonov