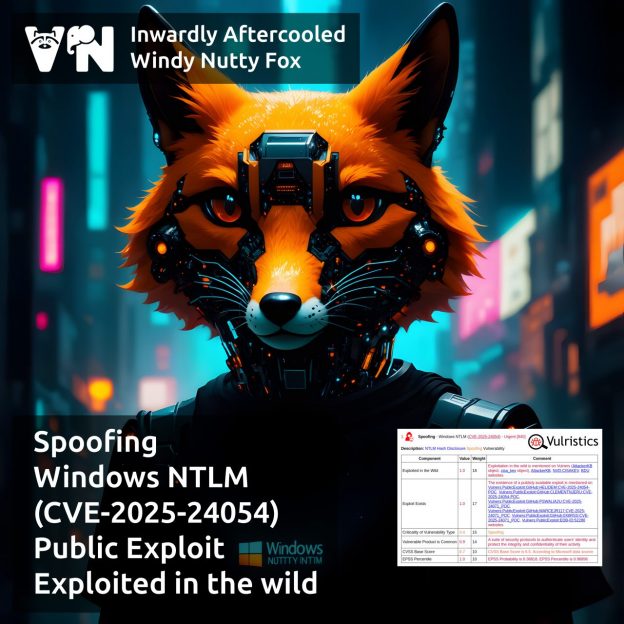
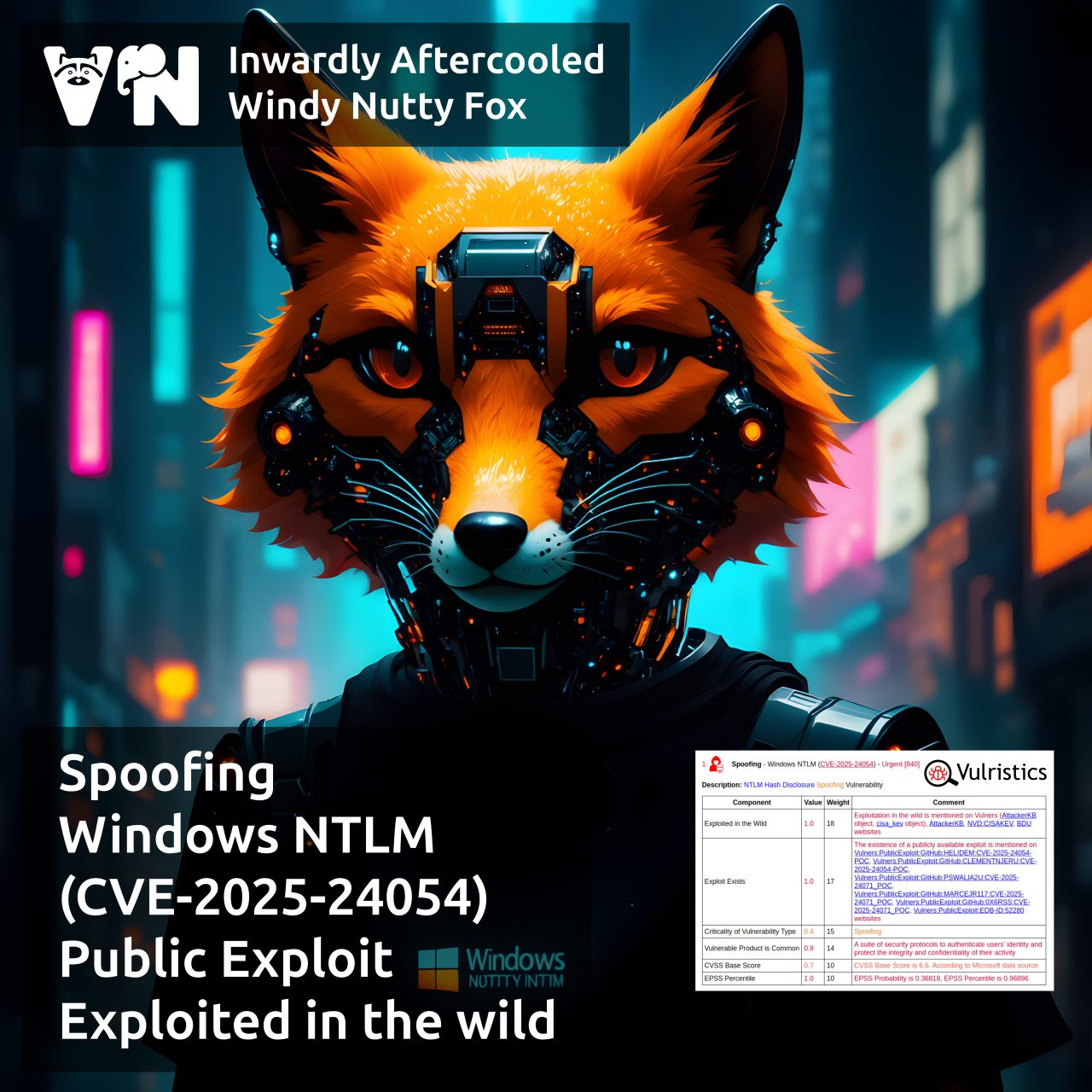
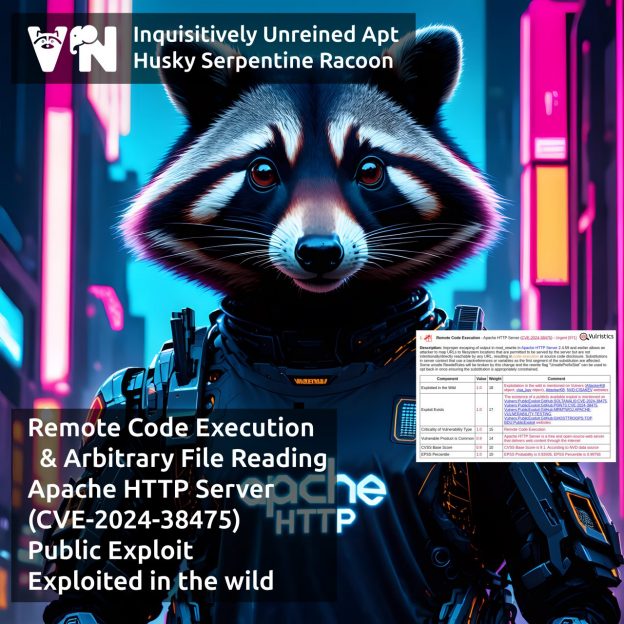
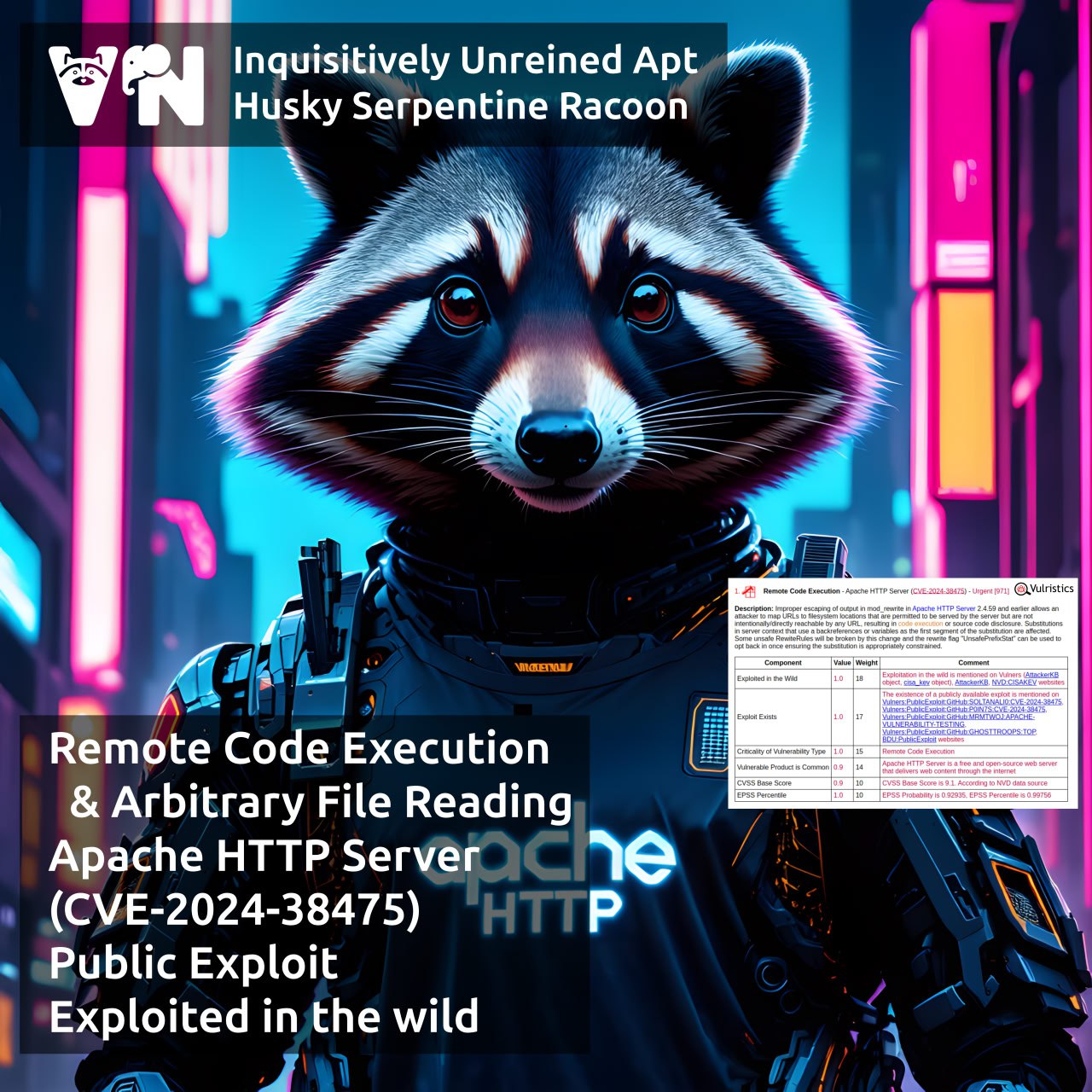
I’m done preparing the slides for my talk about Vulristics at PHDays. 😇 I’ll be speaking on the last day of the festival – Saturday, May 24, at 16:00 in Popov Hall 25. If you’re there at that time, I’d be glad to see you. If not – join online! 😉
I’ll have an hour to dive into Vulristics, vulnerability analysis & prioritization. 🤩 I’ll walk through the Vulristics report structure, typical tasks (like analyzing Microsoft Patch Tuesday, Linux Patch Wednesday, individual trending CVEs, and vulnerability sets), how the work with data sources is organized, the challenges of accurately detecting vulnerability types and vulnerable products. Finally, I’ll discuss Vulristics integration into pipelines. Feel free to use the code – Vulristics is MIT-licensed. 🆓
➡️ Talk on the PHDays website – you can download the .ics calendar file there 😉
⏰ May 24, 2025, 16:00 (MSK)
📍 Luzhniki, Popov Hall 25