Qualys Vulnerability Management GUI and API. It has been a long time since I wrote something about Qualys, but today I will write not just about their free product or service, like SSL Labs, but about the main Cloud Platform.

Qualys pioneered cloud Vulnerability Management. How the cloud VM works? In simple terms, there is a web portal https://qualysguard.qualys.com (or .eu for Europe). You can login there, specify a list of IP addresses you want to check and Qualys server(-s) will scan this hosts and show you a vulnerability report.

Ok, it’s clear with perimeter, but what if some hosts are only accessible from your internal network? In this case, you need to purchase Qualys network appliance, which will communicate Qualys server (read more at “Using Qualys Virtual Appliance“). You create a scan task on Qualys web portal to scan hosts in your internal network, Qualys server gives an order to appliance to gather information about these hosts and to send it back to the server for analysis. Most of the security analysis is done “in the cloud” by remote Qualys servers. End-user manage VM service either through Qualys web-portal GUI, or API.
Here is a fundamental problem of cloud services. Is it safe to store scanning data and credentials somewhere outside of your network? Tough question. It comes down to how much you trust your vendor. In fact, the boundary between the cloud and classical VM vendors becomes thinner. Qualys offers a hosted private cloud and private cloud appliance, and Tenable, for example, offers Nessus Cloud.
Qualys VM GUI
In my opinion, Qualys is a very user-friendly VM. When I use it, I feel that the developers have tried to minimize the entry threshold. Everywhere you can see the handy tips for a quick start and a lot of detailed practical documentation and video tutorials available.

You also can even study at free In-Person or Online Courses, take the Qualys VM exam and get a certificate.
In fact Qualys Cloud Platform is not just a Vulnerability/Compliance Management service anymore, it has many other modules that you can purchase separately and they will share information with each other. But today I would like to talk about vulnerability management.
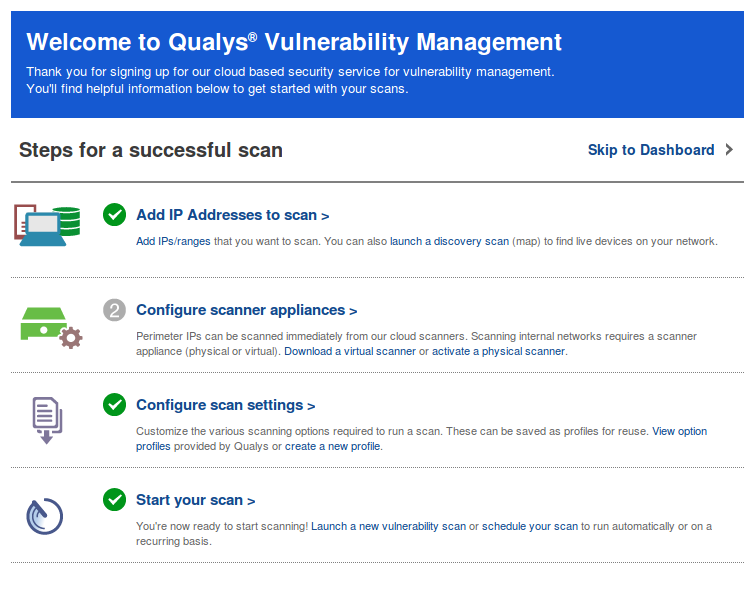
You can make your first scan easily with a special wizard. You should just add addresses to scan, configure network appliance (I scanned only external servers, so I didn’t use it), configure scan settings and start the scan.
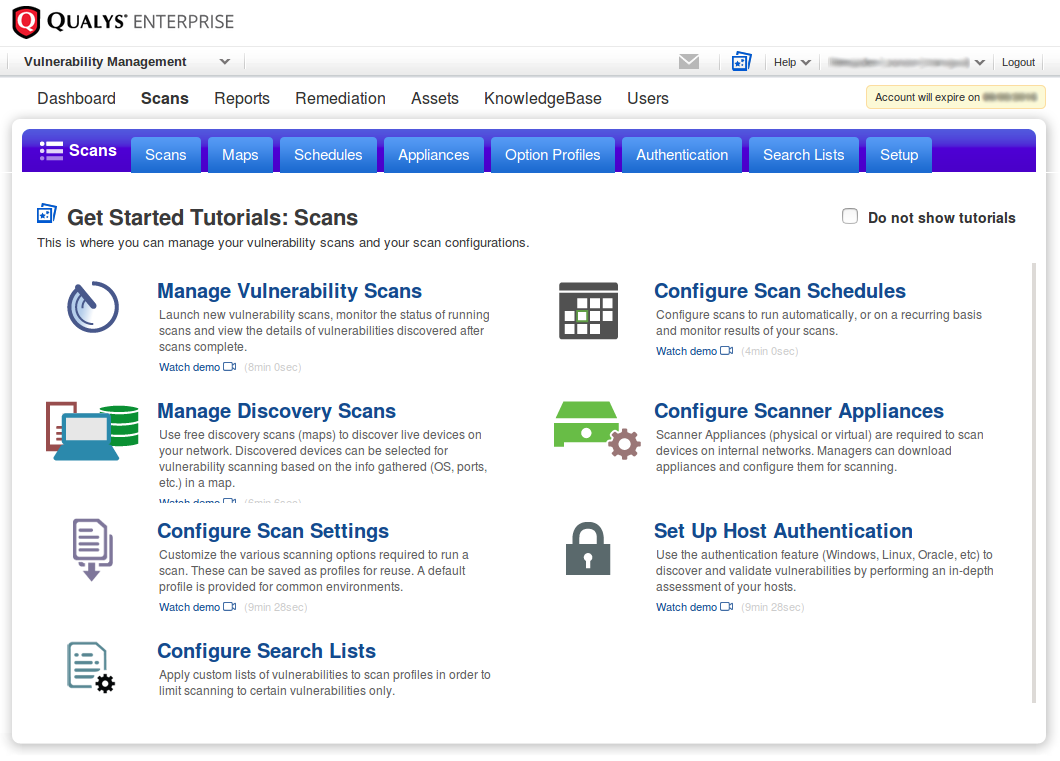
Common Qualys interface for vulnerability scanning looks like this:
Let’s create a new scan task.
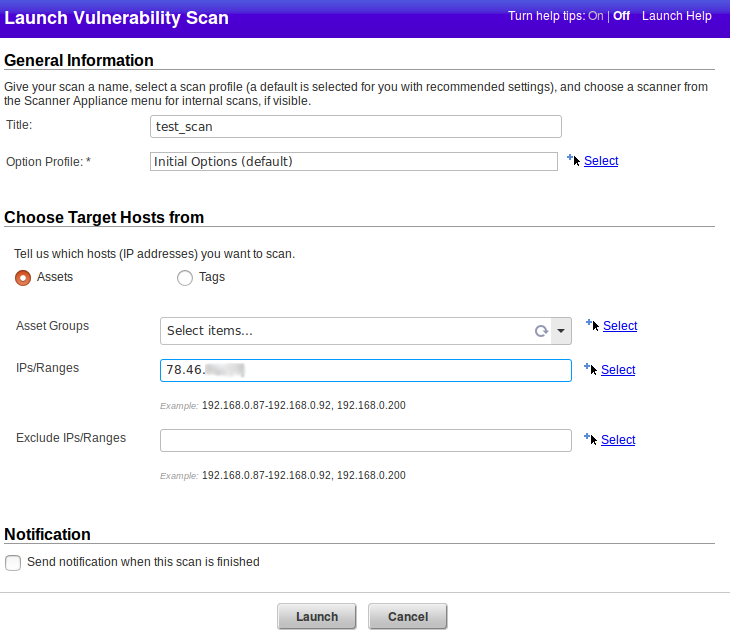
I set title of the scan and the target host ip.
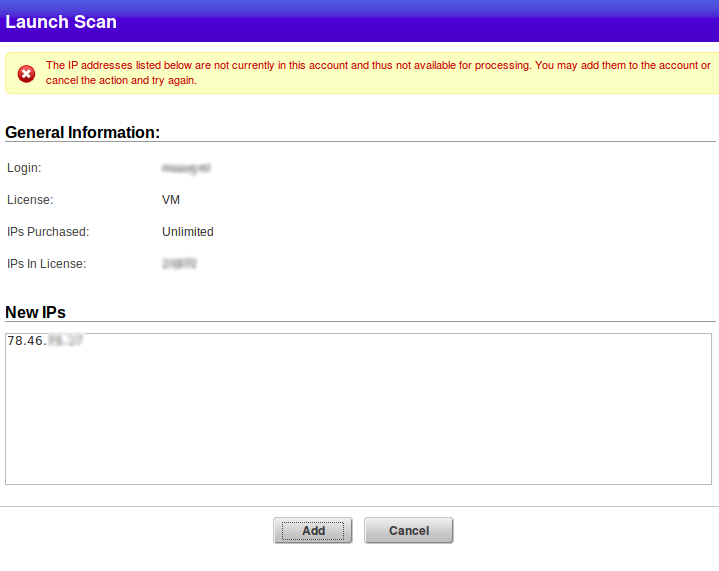
IP-address that I want to scan is not associated with my account. But I can add it. Qualys is licensed for a certain amount of IPs for scanning, and if it were a common license, not a trial one, I could not have the number of IPs in License more than IPs Purchased.
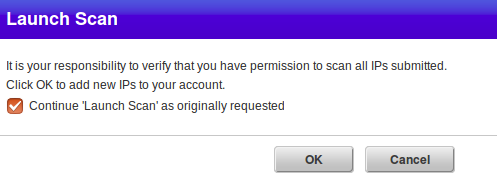
Qualys does not want to be responsible if I decide to scan address, which I don’t have right to scan. In some countries it is even may an illegal action. Therefore, there is a disclaimer:
Vulnerability scan in progress:
When the status is “finished”, press on the scan and choose “View”. Here are the diagrams for the found vulnerabilities: “Vulnerabilities by Severity”, “Operating Systems Detected”, “Services Detected”.
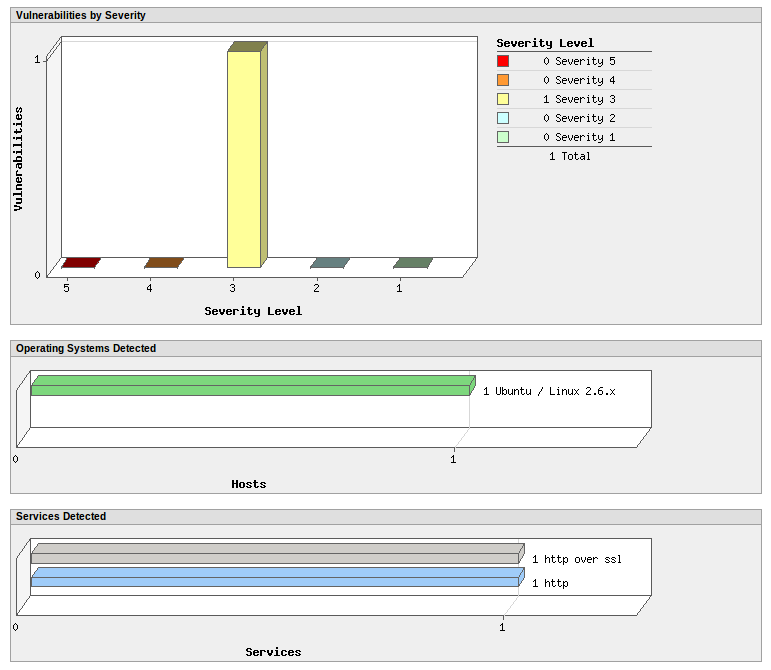
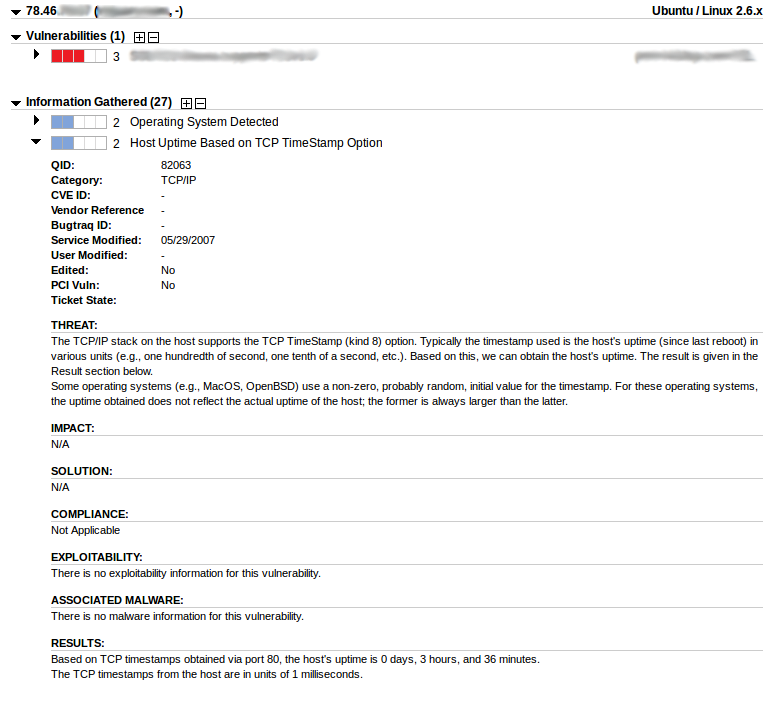
Vulnerability description. Available fields: QID (Qualys ID), Category, CVE ID, Vendor Reference, Bugtraq ID, Service Modified, User Modified, Edited, PCI Vuln, Ticket State, THREAT, IMPACT, SOLUTION, COMPLIANCE, EXPLOITABILITY, ASSOCIATED MALWARE, RESULTS.
To download scan results just press on the scan and choose “Download”.
The file name will be something like this: Scan_Results_<Qualys_User>_20160825_scan_1472036573_32140.xml
Qualys VM API
No matter how convenient GUI is, it is always good to have an API to automate daily VM operations.
Unlike the Tenable SC and Rapid7 Nexpose, to get access to Qualys API you need to purchase a separate license. However, in my opinion, Qualys API is documented much better, for example Qualys API manuals contain examples of curl-requests that you can immediately use. There is a library of tools based on Qualys API at github. Most of them are in Perl. There was a time, when Qualys very actively encourage the development of third-party tools, even was publishing series of interviews with developers at official blog, for example Interview: James Nelson, author of “QualysGuard Open Vulnerability Data Download”.
Let’s see how to view and retrieve vulnerability scans using the API.
Official manual: Qualys API v2 User Guide.
Fist of all, we need a session id for authentication:
curl -v -H "X-Requested-With: Curl Sample" -D headers -d "action=login&username=qualys_user&password=qualys_password" "https://qualysapi.qualys.eu/api/2.0/fo/session/"
* Trying 64.39.100.34...
* Connected to qualysapi.qualys.eu (64.39.100.34) port 443 (#0)
...
< X-Frame-Options: SAMEORIGIN
< Set-Cookie: QualysSession=3ddca03f7906860e283d75c3d362c745; path=/api; secure
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
< Pragma: no-cache
< Transfer-Encoding: chunked
< Content-Type: text/xml
<
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE SIMPLE_RETURN SYSTEM "https://qualysapi.qualys.eu/api/2.0/simple_return.dtd">
<SIMPLE_RETURN>
<RESPONSE>
<DATETIME>2016-08-24T13:59:13Z</DATETIME>
<TEXT>Logged in</TEXT>
</RESPONSE>
</SIMPLE_RETURN>
* Connection #0 to host qualysapi.qualys.eu left intact
Now we let’s see available vulnerability scans:
curl -H "X-Requested-With: Curl Sample" -b "QualysSession=3ddca03f7906860e283d75c3d362c745;path=/api;secure" -d "action=list" "https://qualysapi.qualys.eu/api/2.0/fo/scan/"
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE SCAN_LIST_OUTPUT SYSTEM "https://qualysapi.qualys.eu/api/2.0/fo/scan/scan_list_output.dtd">
<!-- This report was generated with an evaluation version of Qualys //-->
<SCAN_LIST_OUTPUT>
<RESPONSE>
<DATETIME>2016-08-24T14:11:19Z</DATETIME>
<SCAN_LIST>
<SCAN>
<REF>scan/1472036573.32140</REF>
<TYPE>On-Demand</TYPE>
<TITLE><![CDATA[test_scan]]></TITLE>
<USER_LOGIN>qualys_user</USER_LOGIN>
<LAUNCH_DATETIME>2016-08-24T11:02:53Z</LAUNCH_DATETIME>
<DURATION>00:06:40</DURATION>
<PROCESSED>1</PROCESSED>
<STATUS>
<STATE>Finished</STATE>
</STATUS>
<TARGET><![CDATA[78.46.XX.XX]]></TARGET>
</SCAN>
</SCAN_LIST>
</RESPONSE>
</SCAN_LIST_OUTPUT>
<!-- This report was generated with an evaluation version of Qualys //-->
<!-- CONFIDENTIAL AND PROPRIETARY INFORMATION. Qualys provides the QualysGuard Service "As Is," without any warranty of any kind. Qualys makes no warranty that the information contained in this report is complete or error-free. Copyright 2016, Qualys, Inc. //-->
scan/1472036573.32140 is the scan I created earlier in GUI.
Before we get scan/1472036573.32140 results, I would like to take a break and recommend useful utility- Qualys API Explorer. It is something like an interactive handbook in a form of Chrome extension.
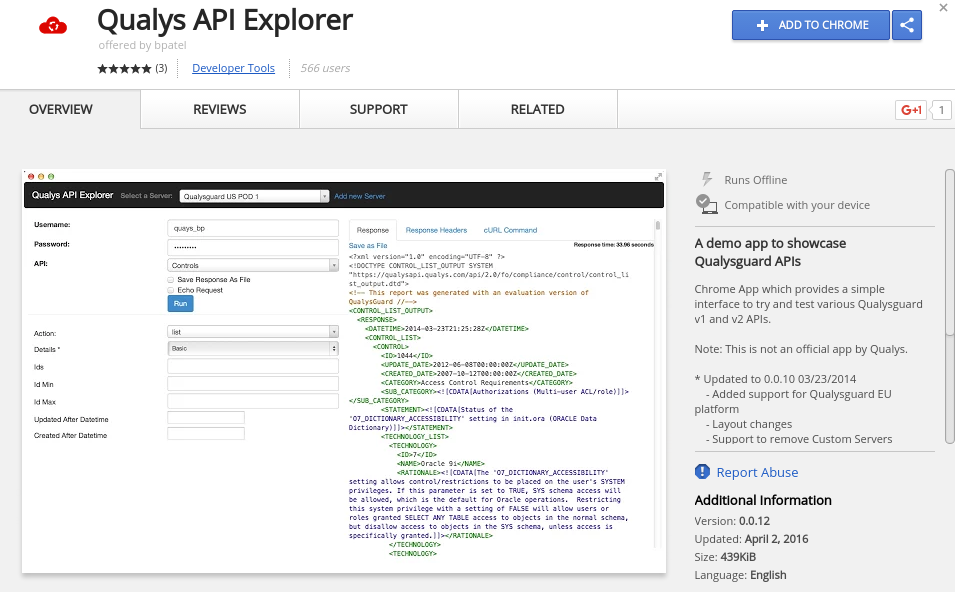
Instead of searching a request description in the manual, I can select the type of API and request in menu, set all parameters and actually run a request with authentication on a real Qualys server. I will get response and an example of curl command.
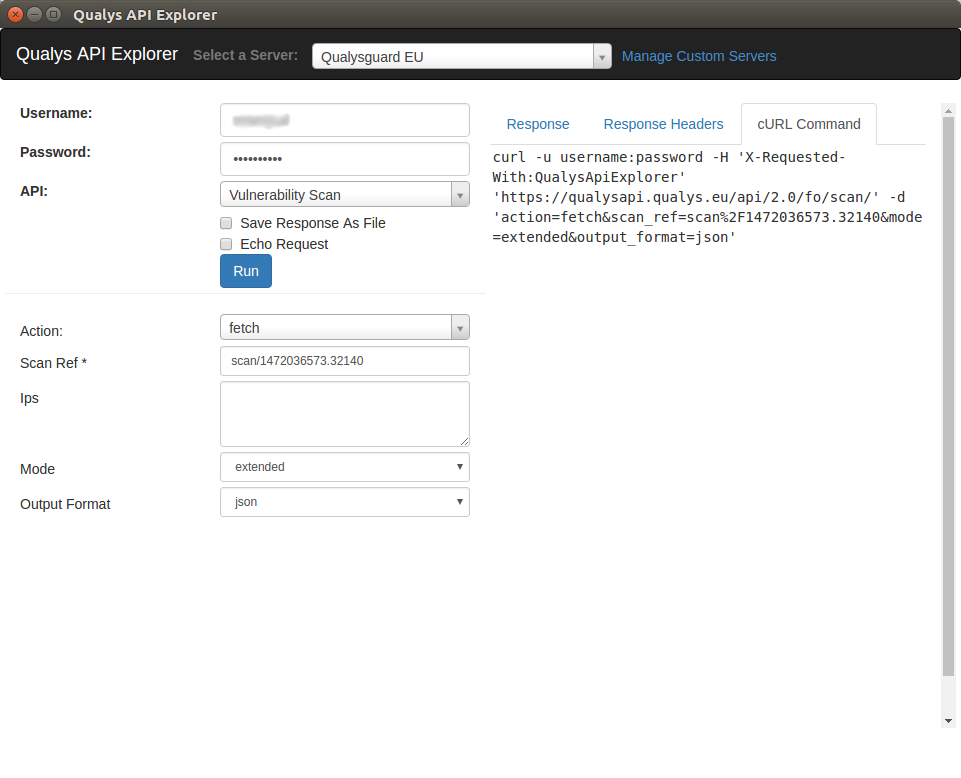
Let’s use the curl command (but use the session authentication and json_extended format):
curl -H "X-Requested-With: Curl Sample" -b "QualysSession=3ddca03f7906860e283d75c3d362c745;path=/api;secure" 'https://qualysapi.qualys.eu/api/2.0/fo/scan/' -d 'action=fetch&scan_ref=scan%2F1472036573.32140&mode=extended&output_format=json_extended‘
[{"scan_report_template_title":"Scan Results","result_date":"08\/25\/2016 17:35:54","company":"Company","add1":"Address","add2":null,"city":"City","state":"None","country":"Country","zip":"123456","name":"Alexander Leonov","username":"qualys_user","role":"Manager"},
...
{"ip":"78.46.XX.XX","dns":"xxxx","netbios":null,"os":"Ubuntu \/ Linux 2.6.x","ip_status":"host scanned, found vuln","qid":86565,"title":"Web Server Supports HTTP Request Pipelining","type":"Ig","severity":"1","port":"80","protocol":"tcp","fqdn":"","ssl":"no","cve_id":null,"vendor_reference":null,"bugtraq_id":null,"threat":"Version 1.1 of the HTTP protocol supports URL-Request Pipelining. This means that instead of using the \"Keep-Alive\" method to keep the TCP connection alive over multiple requests, the protocol allows multiple HTTP URL requests to be made in the same TCP packet. Any Web server which is HTTP 1.1 compliant should then process all the URLs requested in the single TCP packet and respond as usual.\n \nThe target Web server was found to support this functionality of the HTTP 1.1 protocol.","impact":"Support for URL-Request Pipelining has interesting consequences. For example, as explained in this paper by Daniel Roelker (http:\/\/www.defcon.org\/images\/defcon-11\/dc-11-presentations\/dc-11-Roelker\/dc-11-roelker-paper.pdf), it can be used for evading detection by Intrusion Detection Systems. Also, it can be used in HTTP Response-Spliting style attacks.","solution":"N\/A","exploitability":null,"associated_malware":null,"results":"GET \/ HTTP\/1.1\nHost:78.46.XX.XX:80\n\nGET \/Q_Evasive\/ HTTP\/1.1\nHost:78.46.XX.XX:80\n\n\n\nHTTP\/1.1 403 Forbidden\nDate: Wed, 24 Aug 2016 11:05:28 GMT\nContent-Type: text\/html\nContent-Length: 162\nConnection: keep-alive\nServer: nginx-wallarm\n\n<html>\n<head><title>403 Forbidden<\/title><\/head>\n<body bgcolor="white">\n<center><h1>403 Forbidden<\/h1><\/center>\n<hr><center>XXXX<\/center>\n<\/body>\n<\/html>\nHTTP\/1.1 403 Forbidden\nDate: Wed, 24 Aug 2016 11:05:28 GMT\nContent-Type: text\/html\nContent-Length: 162\nConnection: keep-alive\nServer: XXXX\n\n<html>\n<head><title>403 Forbidden<\/title><\/head>\n<body bgcolor="white">\n<center><h1>403 Forbidden<\/h1><\/center>\n<hr><center>nginx<\/center>\n<\/body>\n<\/html>","pci_vuln":"no","instance":null,"category":"Web server"},
...
{"target_distribution_across_scanner_appliances":"External : 78.46.XX.XX"}]
Yes, it’s a flat JSON organized by vulnerability (qid) and host (ip,dns). Qualys for whatever reason, does not allow to get a scan in a XML-format. But in fact it is informative as xml, that you can get in GUI. Compare for QID 86565:
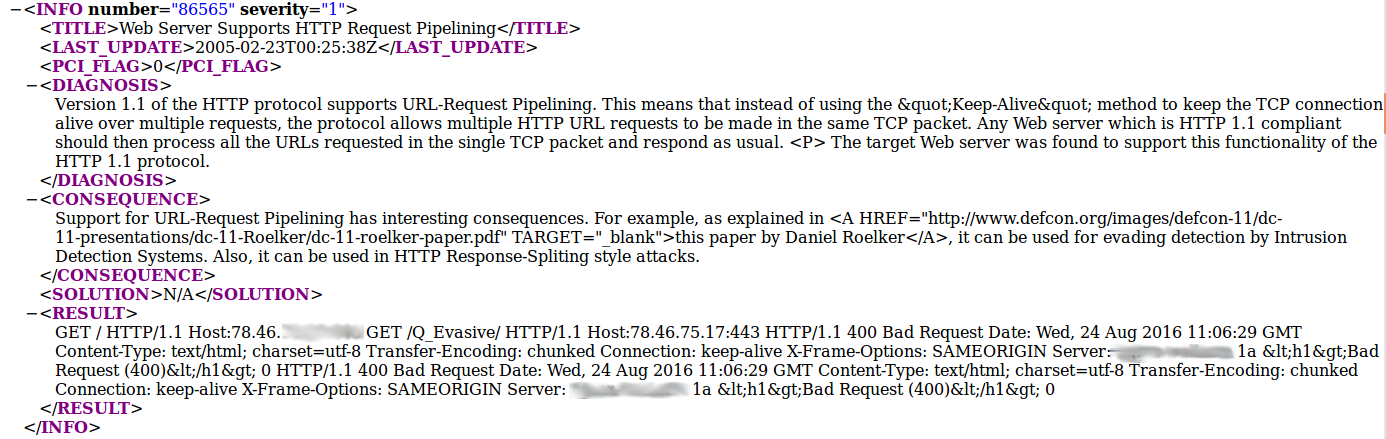
Pretty the same with a small difference in tag naming:
- threat -> diagnosis
- impact -> consequence
It would be more familiar for me to get the output in XML form, but it is also good. And it will be easier to put this JSON in Splunk 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Using Qualys Virtual Scanner Appliance | Alexander V. Leonov
Pingback: Dealing with Qualys Cloud Agents | Alexander V. Leonov
Pingback: New Vulners.com services for Linux Security Audit and Vulnerability Alerting | Alexander V. Leonov
Pingback: Qualys Option Profiles for Vulnerability Scanning | Alexander V. Leonov
Pingback: QSC16: from Vulnerability Management to IT Visibility | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Rapid7 Nexpose in 2017 | Alexander V. Leonov
Pingback: Asset Inventory for Internal Network: problems with Active Scanning and advantages of Splunk | Alexander V. Leonov