Seccubus installation and GUI overview. Seccubus can be roughly described as an open source analogue of Tenable SecurityCenter. Look, it can launch scans via APIs of Nessus, OpenVAS, and some other scanning tools, retrieve scan results, parse them and put in MySQL database. Then you can make SQL queries and work with scans in asset-based way (as you know, it is trending now).
Well, Seccubus is not yet a fancy-looking security product. You will need to spend some time to install and configure it, but still it is a very interesting project with a great potential.
Seccubus also may serve as open project that will accumulate expertise in API usage for various Vulnerability Scanners. Another project of such kind is OpenVAS, it’s OSPd scripts and connectors.
In this post I will describe installation process an show elements of GUI web-interface.
I installed Seccubus in CentOS 6 x86_64. I also tried CentOS 6 i386 and it worked fine. However, I can’t recommend you to install official Seccubus packages in CentOS 7 and the latest Debian-based systems. I had some issues with dependencies and Apache configuration. It seems like these systems are not fully supported yet. Security patches for CentOS 6.8 will be available until 30 Nov 2020, so anyway we have time.
CentOS
CentOS 6 x86_64 was deployed as a virtual machine in VirtualBox. The only non-standard change in configuration of virtual machine I made was “host-only network”. You can see how to configure it in my post about OpenVAS installation after “Couple of words about VirtualBox testing stand I used”.
After basic CentOS installation you may need to create configuration files for eth0 and eth1 interfaces:
# cat /etc/sysconfig/network-scripts/ifcfg-eth0
DEVICE="eth0"
ONBOOT="yes"
BOOTPROTO="dhcp"
And than (here and below, all of the commands I executed as root):
service network restart
With `ip addr` I have detected my server IP-address is 192.168.56.103.
Installation of the OpenSSH server and disabling firewall (doing this for testing purposes only):
yum install openssh-server
service sshd start
service iptables stop
Than I can connect to my further Seccubus server:
ssh vmuser@192.168.56.103
Seccubus installation and configuration
“Download” button at https://www.seccubus.com/ leads to the project’s GitHub page.
Here you can find Seccubus packages for the main Linux distributions:
Installation of the package:
wget https://github.com/schubergphilis/Seccubus_v2/releases/download/2.26/Seccubus-2.26.1-42.1.noarch.rpm
yum install Seccubus-2.26.1-42.1.noarch.rpm
Configuration of the database. The Idea is to create database, user and password named “seccubus” and import database structure and content (latest version now is 8) from the files at /opt/seccubus/var/. You can redefine database name, user name and password in /etc/seccubus/config.xml.
service mysqld start
mysql << EOF
create database seccubus;
create user seccubus;
SET PASSWORD FOR 'seccubus'@'localhost' = PASSWORD('seccubus');
grant all privileges on seccubus.* to seccubus;
EOF
mysql -u seccubus -pseccubus seccubus < structure_v8.mysql
mysql -u seccubus -pseccubus seccubus < /opt/seccubus/var/data_v8.mysql
service httpd restart
service iptables stop
Apache
Now you may try to open http://192.168.56.103/seccubus. But you will probably get 403 error. Why? Because Seccubus don’t have authorization form, works only in single user mode and by default you can use it only on the host, where it is installed. You can modify this in /etc/httpd/conf.d/Seccubus.conf. It’s not a good idea to open public access to the Seccubus web GUI in your network, but in the case of virtual machine and host-only network, it’s safe.
# cat /etc/httpd/conf.d/Seccubus.conf
#
# This configuration file maps the Seccubus logs
# into the URL space. By default these results are
# only accessible from the local host.
#
Alias /seccubus /opt/seccubus/www
<Location /seccubus>
Order deny,allow
Deny from all
Allow from 127.0.0.1
Allow from ::1
# Allow from .example.com
AddHandler cgi-script .pl
Options ExecCGI
</Location>
I changed “Deny from all” to “Allow from all” and launched once again:
service httpd restart
Web GUI
Well, I won’t write here how to use Seccubus. I will just share my first impressions on empty web interface, so you could see how it looks. I purposely did not read the manual, to check how intuitive interface is.
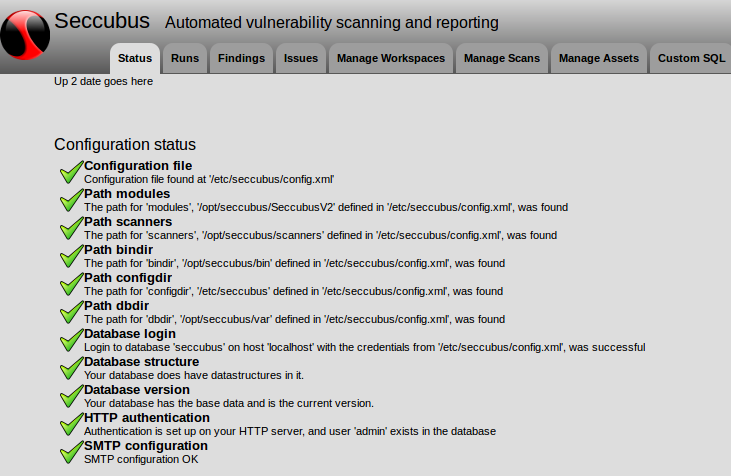
The first tab is Status and you can see here, that both installation and configuration process was successful.
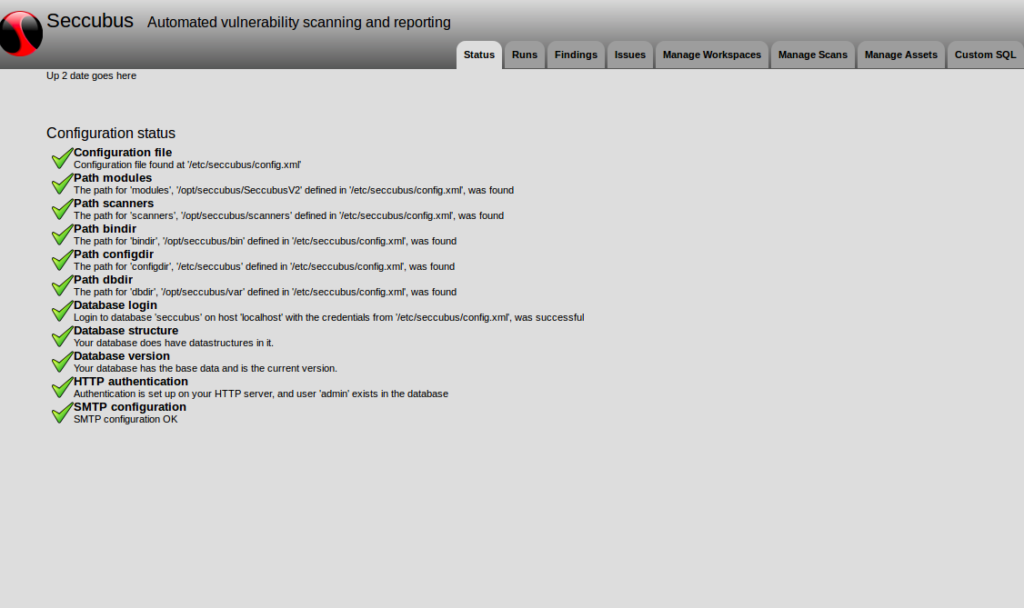
As far as I understand, “workspace” entity is needed in Seccubus to manage several different not related Vulnerability Assessment projects. I created new workspace named “test”.
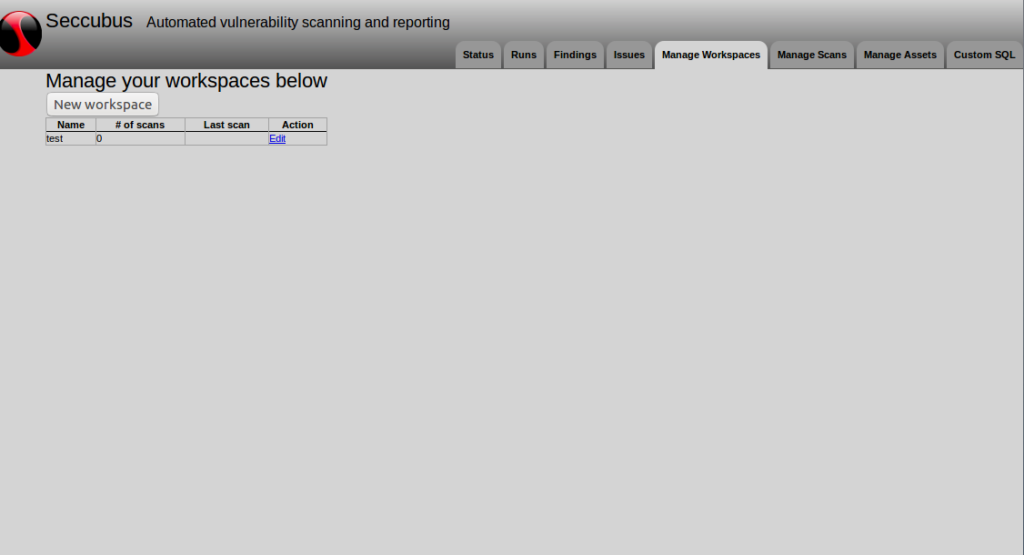
You can add vulnerability scans in a specific Workspace.
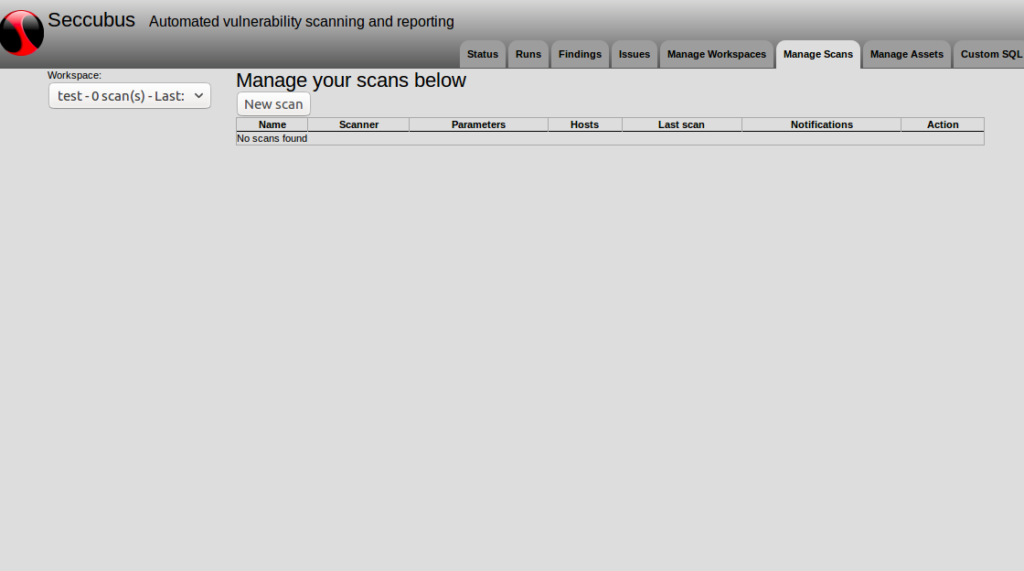
In this form you can add a new scan:
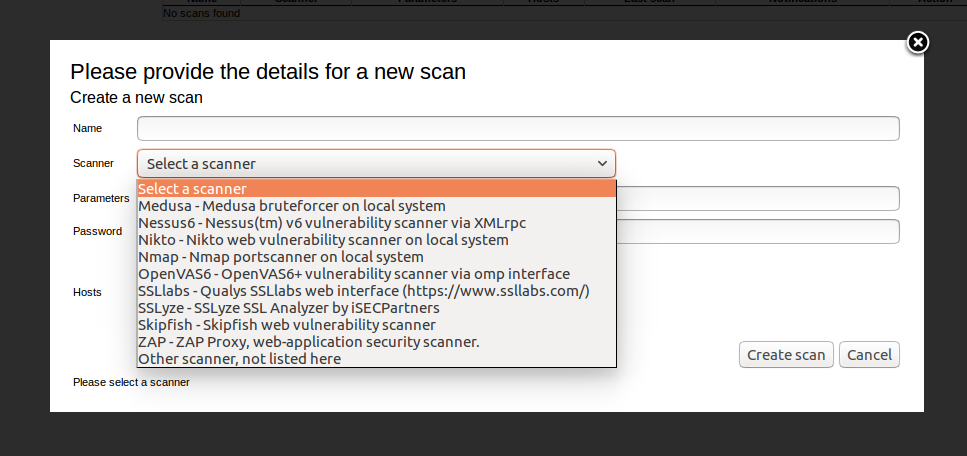
Here is a list of supported scanners. The most interesting for me are Nessus and OpenVAS.
This tab looks like the list of scan results.
This is an interface in which you can set filtering rules and find interesting vulnerabilities. The same way you can do in SecurityCenter or Splunk SIEM. You can search within some scans, as well as within the group of assets.
“Issues” are the items for remediation activity:
Managing groups of assets (host lists):
Finally, the tab where you execute arbitrary SQL-queries to the database. As I understand it, it is necessary mainly for debugging.
It looks pretty clear and functional. Later I will try to connect Seccubus with some vulnerability scanner to see how all this works in practice.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Have you tried SSLlabs scan? I want to know how to use it but I get no result. Thanks.
Hello BRian, I used it, but not in Seccubus. I was making my own scripts using Qualys SSL Labs console client.
So did I. I wrote a script that runs scanning every week and now my supervisor found this and want me to try. Thanks for reply.
How to download reports from Seccubus, I dont find any option to download the report.