Outpost24 Appsec Scale for Web Application Scanning. Today I would like to write about yet another Outpost24 product – cloud Web Application Scanner Appsec Scale.
It is available in the same interface as Outpost24 Outscan, that I reviewed earlier. Select APPSEC SCALE in the start menu and you can scan web applications:
New application
If you don’t have web application targets yet, press on the plus icon:
Add a new application/site:
You will see a new target:
If you select the target, context menu will appear above. You can create a report, start a scan or delete a target there.
If you click on the pencil icon, you can configure the scan.
Scan Settings
In the Scan Settings, you can specify Name, Time limit for the scan, Seed URLs (one or multiple), Allow subdomains (yes/no), Schedule (From time and To time), Recurrence (Once, Weekly, Monthly, Bimonthly, Quartely, Fortnightly, Daily), Scan intensity (Normal or Low – sequential requests), Vulnerability testing/fuzzing mode and User agent (Desktop or Mobile)
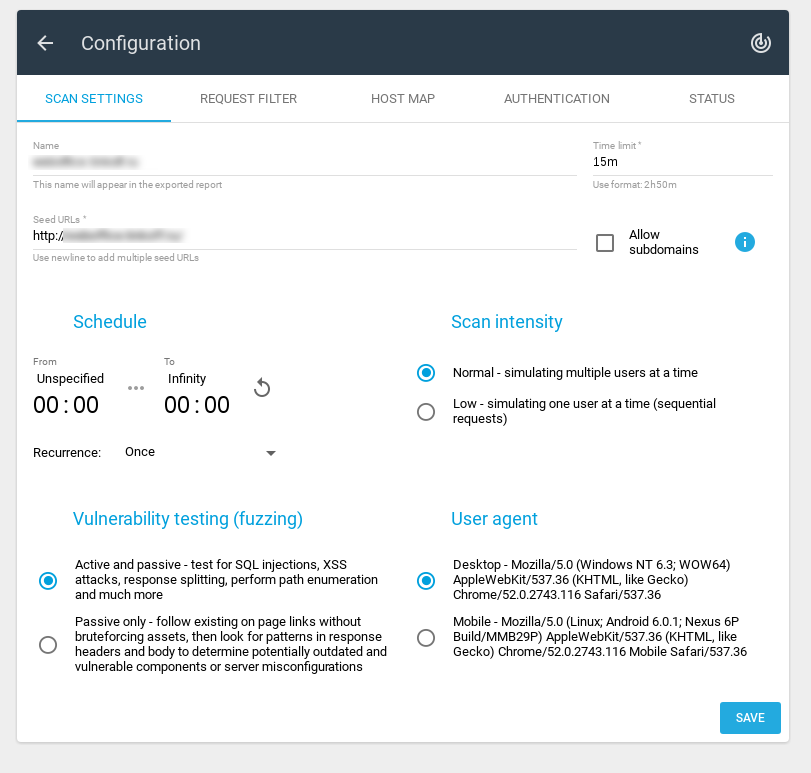
There are two modes of Vulnerability testing (fuzzing) available:
- Active and passive – test for SQL injections, XSS attacks, response splitting, perform path enumeration and much more
- Passive only – follow existing on page links without bruteforcing assets, then look for patterns in response headers and body to determine potentially outdated and vulnerable components or server misconfigurations
Request Filter
You can create some filters to forbid some scan activities for some urls or on pages with specific body.
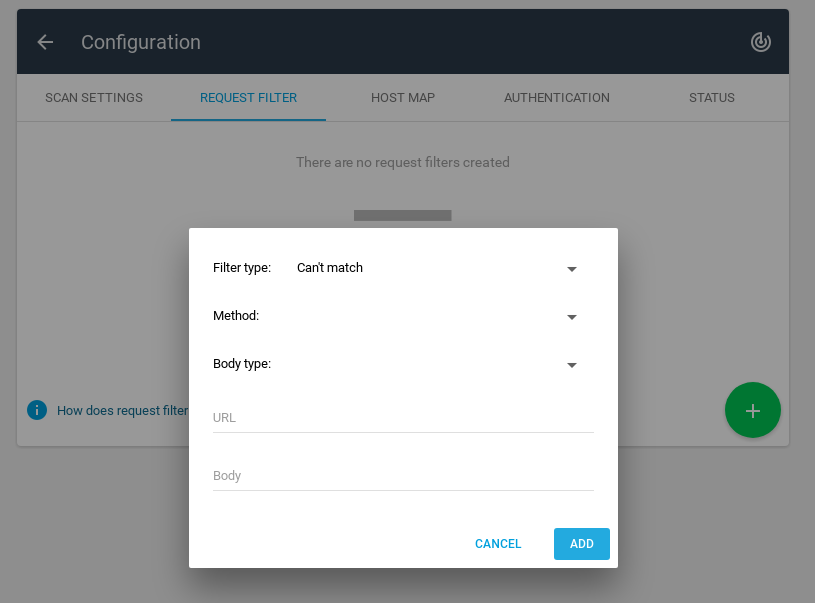
Filter type:
- Can’t match
- Must match
Method:
- GET
- POST
- DELETE
- PATCH
- PUT
Body type:
- application/json
- application/x-www-form-urlencoded
- multipart/form-data
- multipart/mixed
- text/plain
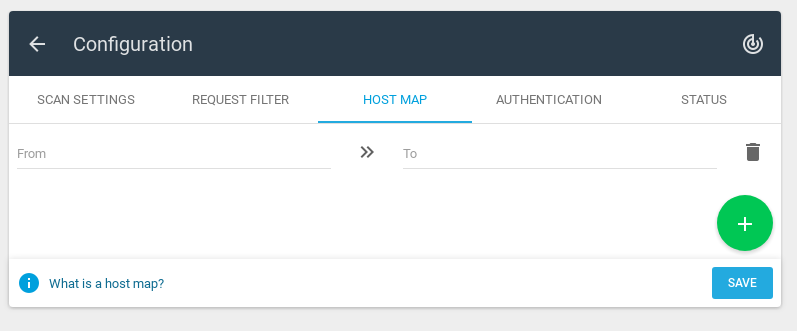
Host Map
Using host map you can force DNS resolutions.
For example: corporation.com -> 203.23.113.15
Authentication
I think this is the most interesting feature of Appsec Scale – custom authorization via Lua scripts.
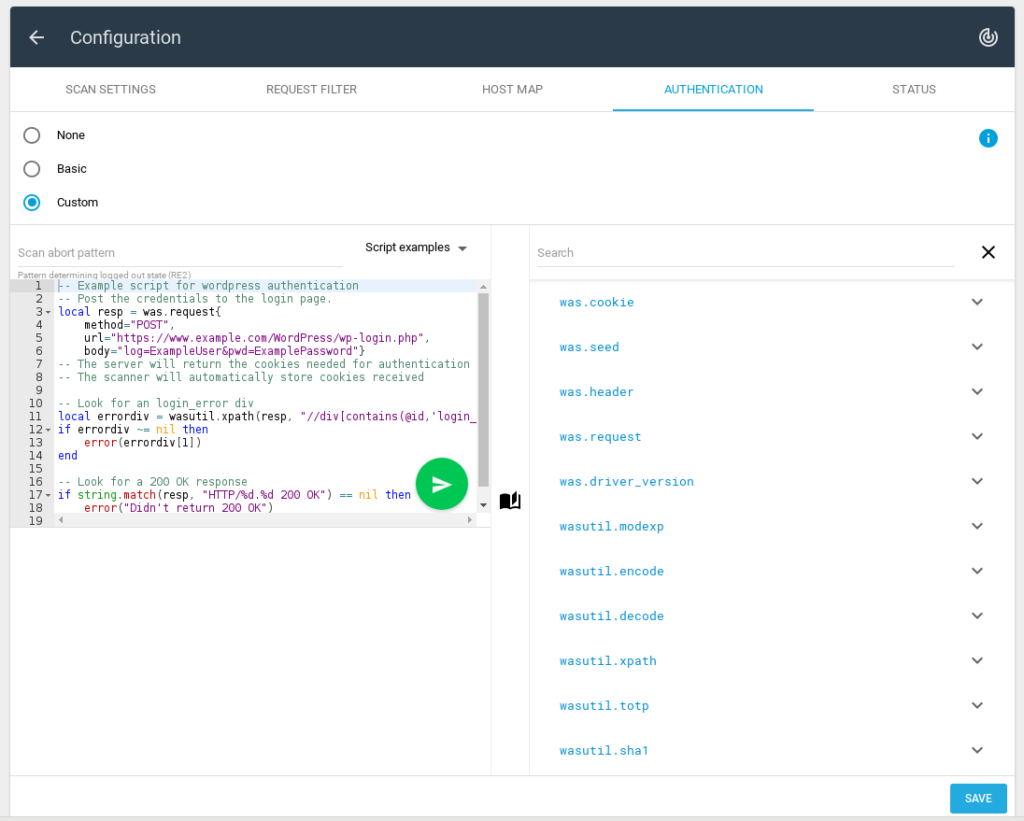
On the right side you can see some information about supported functions.
Available script examples:
- Cookie based
- XPath
- WordPress
Here you can debug your scripts by clicking on the button with a paper airplane:
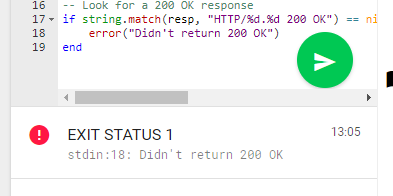
Scan abort pattern is a regular expression. If any responce matches this expression, it means that we are not logged on the site.
But of course it’s possible to use basic authentication settings:
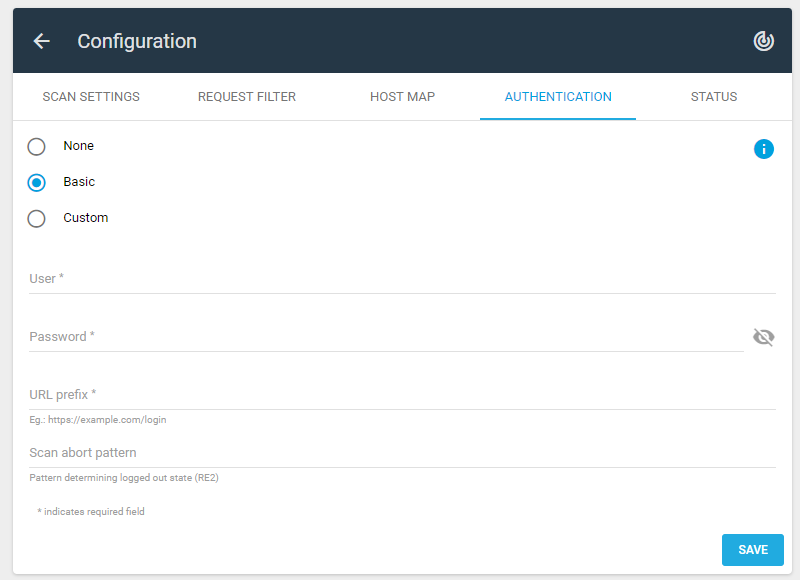
In this case, you must specify the User name, Password, URL prefix and Scan abort pattern.
Status
Until you started the scan, the status tab looks like this:
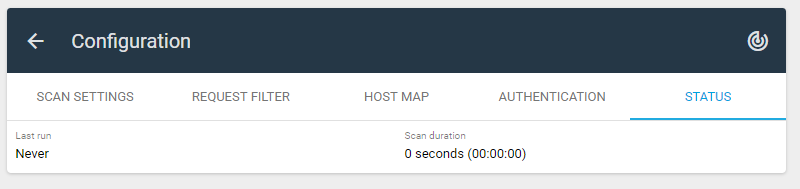
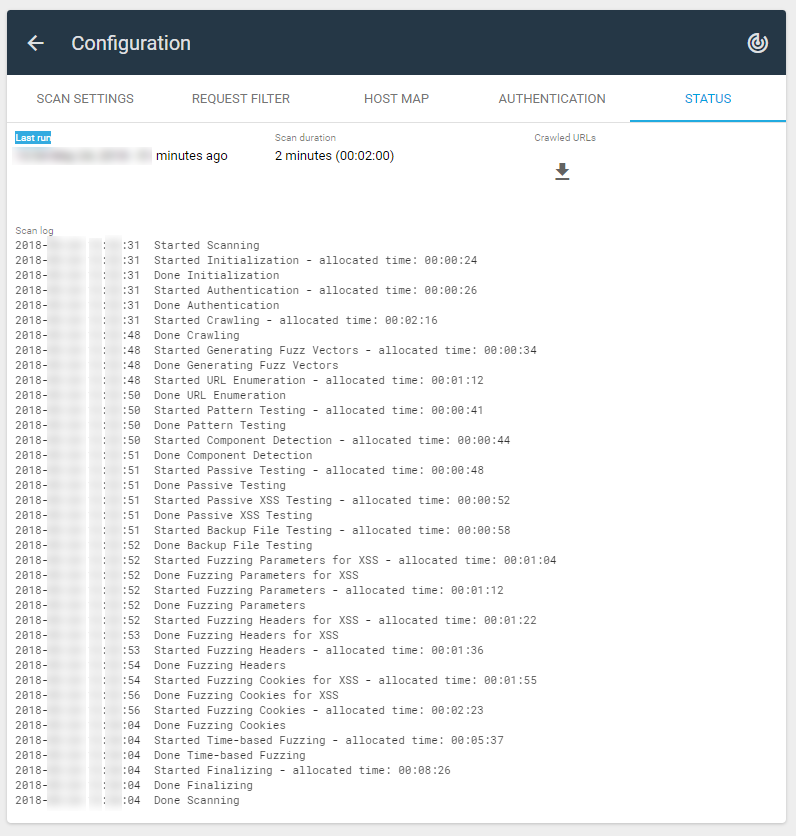
After performing the scan, you will be able to see here when was the Last run, Scan duration, Crawled URLs and Scan log:
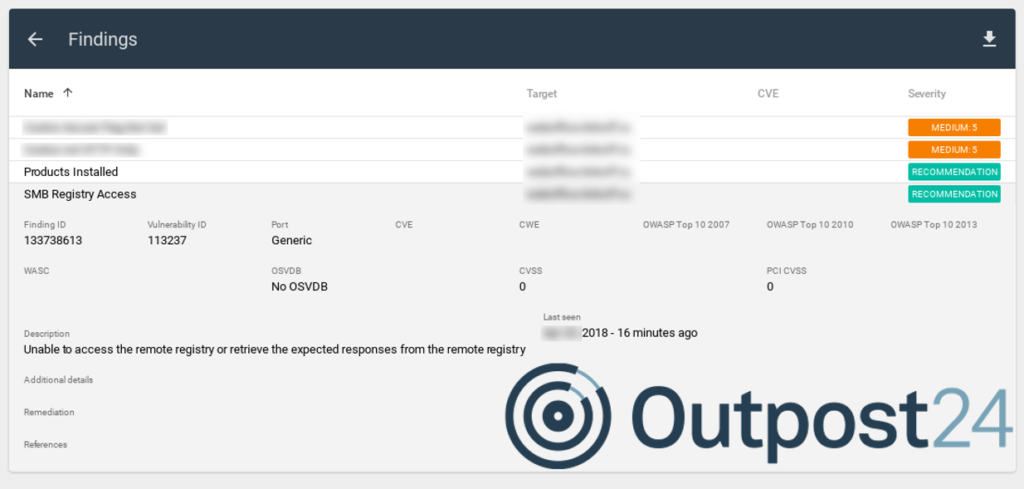
Findings
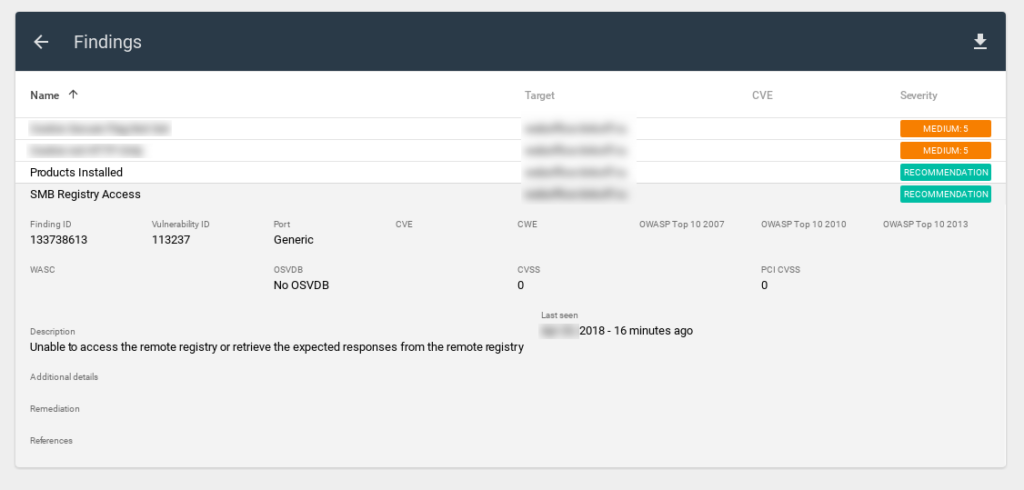
- Finding ID
- Vulnerability ID
- Port
- CVE
- CWE
- OWASP Top 10 2007
- OWASP Top 10 2010
- OWASP Top 10 2013
- WASC
- OSVDB
- CVSS
- PCI CVSS
- Method (GET/POST/etc.)
- URL
- Name
- Description
- Additional details
- Remediation
- References
- Last seen
Note that the report also contains information about vulnerabilities that were NOT found. For example, for SMB Registry Access, we can see “Unable ot access” in Additional details.
Reports
Appsec Scale can export scan results as a report.
Available formats:
- EXCEL
- XML
Here is how the PDF report looks like:

The Executive Summary part looks quite interesting. I took an illustration from the official manual:
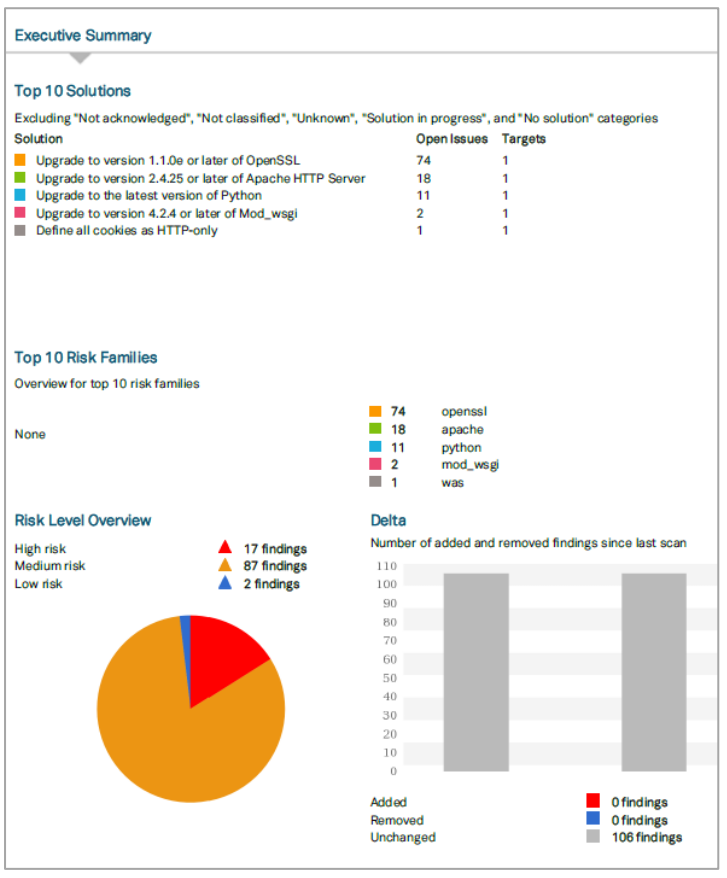
You can see here:
- Top 10 Solutions
- Top 10 Risk Families
- Risk Level Overview (High, Medium, Low)
- Delta – тumber of added and removed findings since last scan
They also provide Trend. It’s a chart with numbers of findings for each risk level between first and latest scan.
In conclusion
The solution seems rather interesting.
I deliberately will not write anything about scanning quality. In the case of WAS, this thing is rather subjective. If you are testing this or another WAS solution, I recommend you to take some application with confirmed vulnerabilities (but NOT some standard one, like DVWA) and try to scan it using several WAS solutions. The results will surprise you most likely.
I really liked Appsec Scale IDE for authentication scripts. I think it can be potentially a very powerful feature if Outpost24 will add the ability to create custom vulnerability checks in such way as well.
I was a little bit disappointed that the powerful interface for filtering vulnerabilities from Outscan is not used in Scale. Of course, the WAS and VM have different workflows, but it seems that such an interface would be very convenient for understanding the situation with web vulnerabilities in the organization.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.