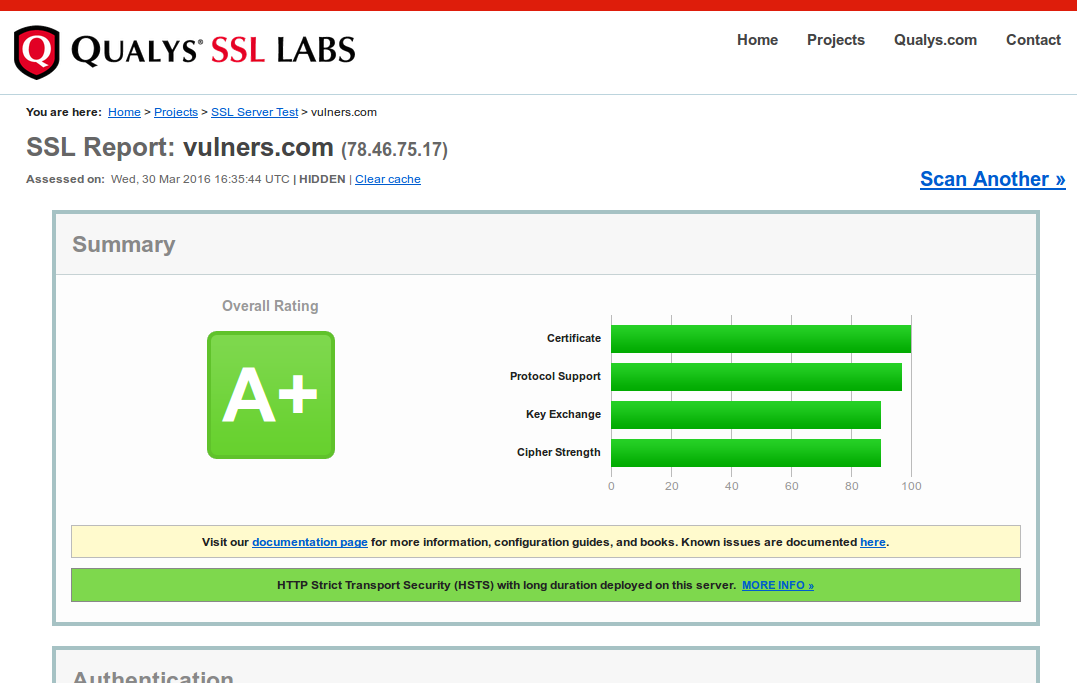
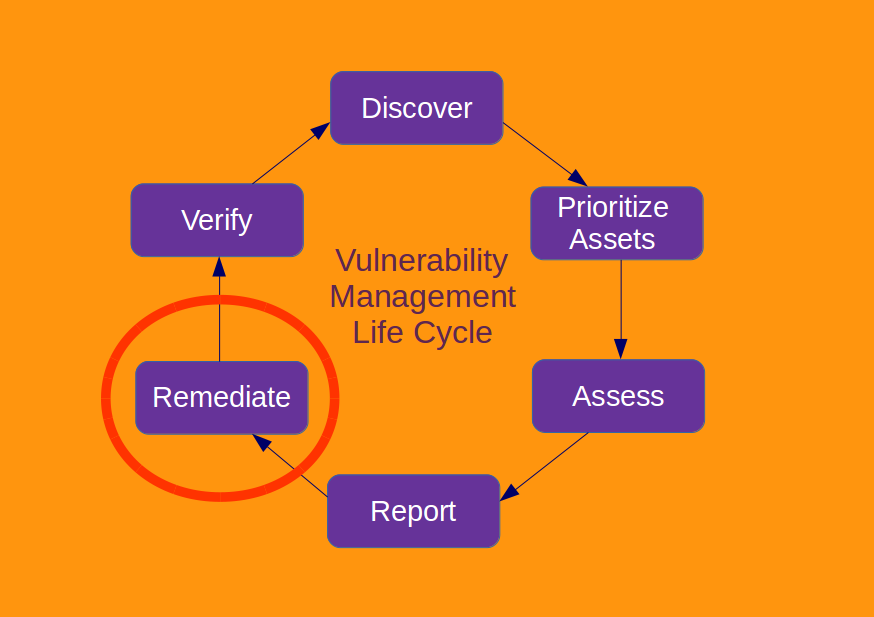
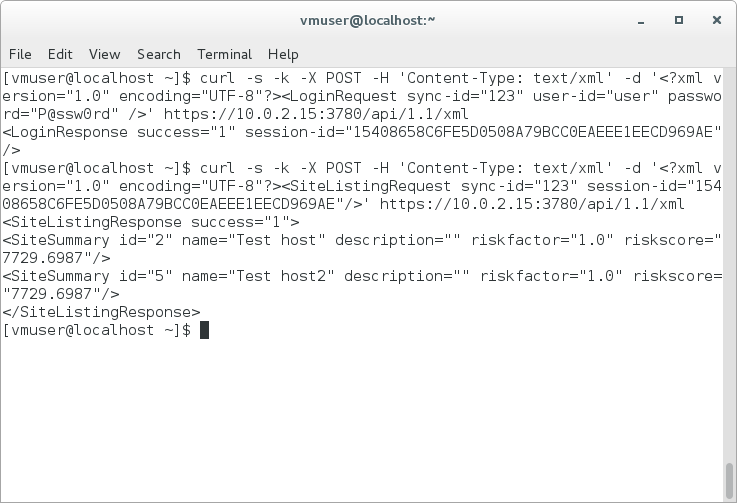
VM Remediation using external task tracking systems. In previous post I have briefly reviewed built-in remediation capabilities of vulnerability management systems. Continuing the theme, today I want to share some basic concepts how vulnerability remediation can be managed using external task tracking systems (Jira, TFS, Testrack, etc).
Pros: it makes possible to implement any logic of remediation/patch management process.
Cons: you should make it by yourself; scripting skills and API knowledge required.
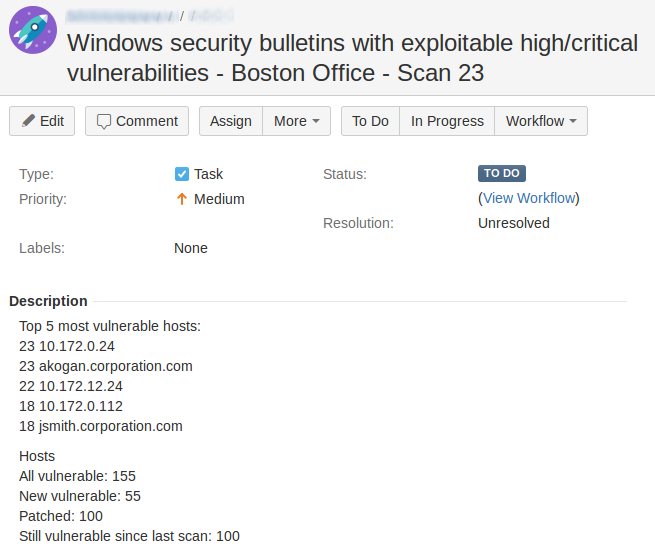
Tickets in buit-in remediation systems are usually assigned per host or per vulnerability. However, for large size networks making “one vulnerability on one host – one ticket” quickly become impractical. With universal task trackers we can do it in a different ways. I find it most convenient to make tickets on principle “one category of vulnerabilities, one ip range, one scanning iteration – one ticket”.
Continue reading