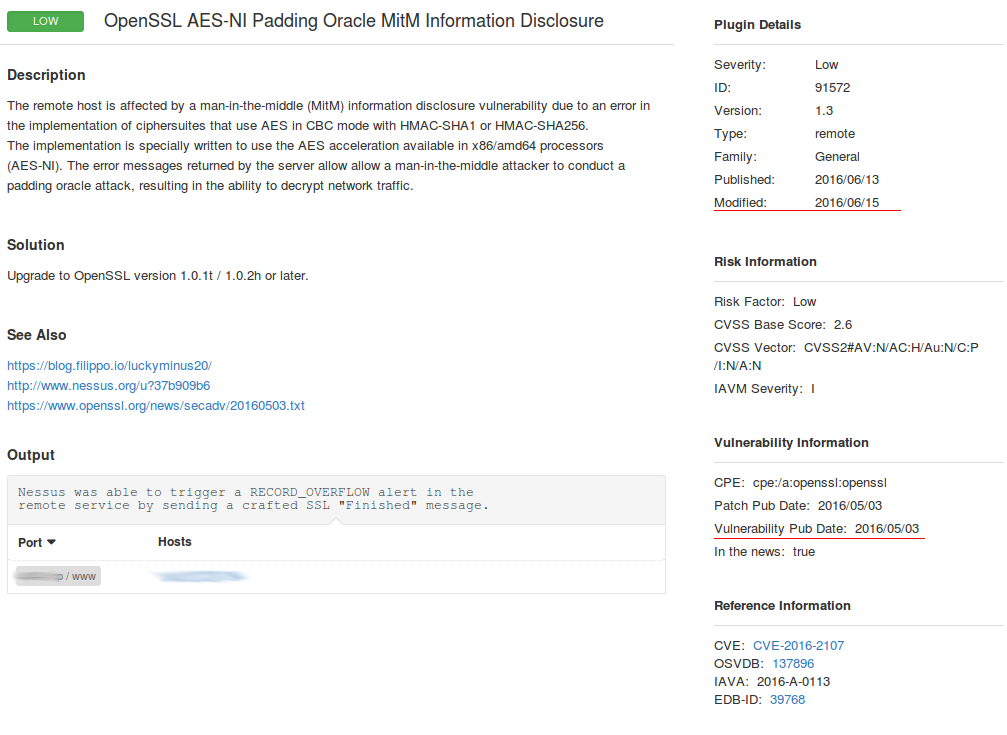
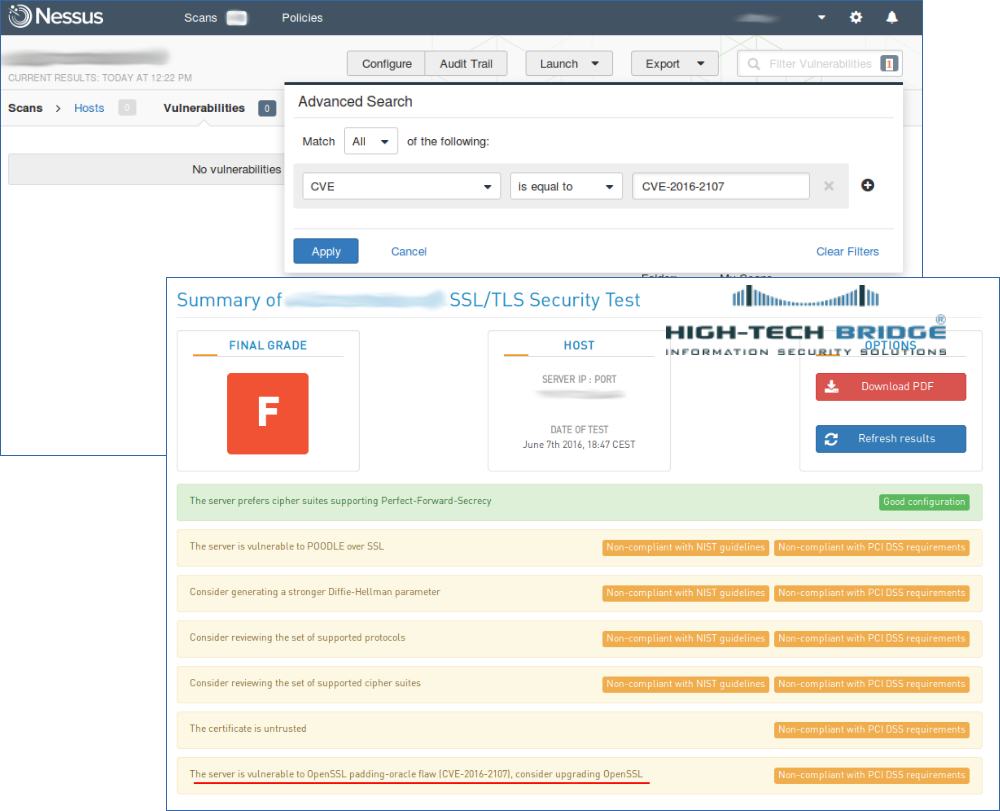
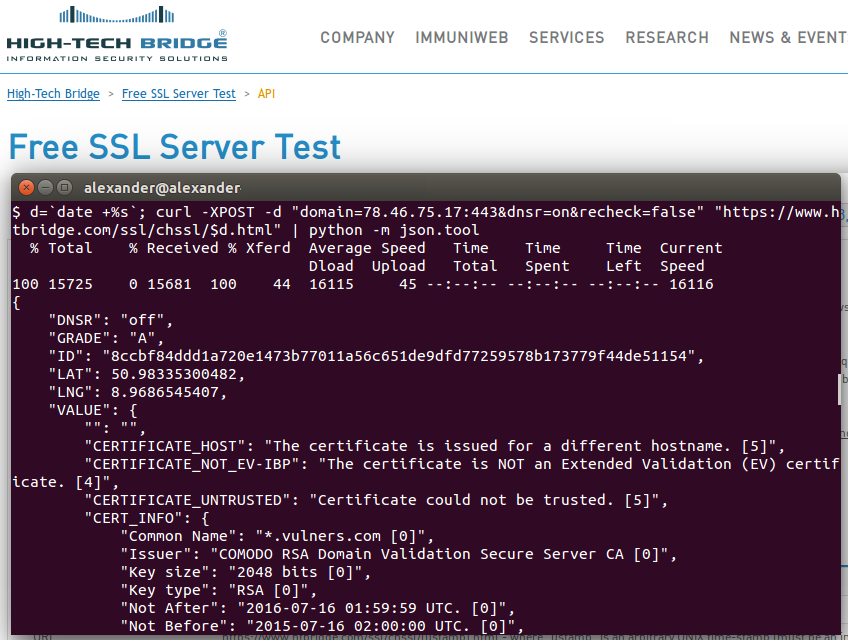
It won’t be a secret to say that phishing remains one of the most effective attack vectors.
For example, your colleague receives by email a malicious web link that looks like a link to your corporate portal and opens it. If your Vulnerability and Patch Management programs are not good enough (see “WannaCry about Vulnerability Management“) and the software on his desktop has some critical and exploitable vulnerabilities in web browser, PDF reader, Microsoft Office, etc., you will probably get compromised host in your network.
This is also a pain for your customers. If someone will be sending messages on behalf of your organization, this can easily lead to fraud and costs in public image. And it will be even harder to detect. You will know about it only if they tell you. And if the attack was not massive, the probability of this is not very high.
What can we do about this?
- We should definitely raise the awareness among co-workers and clients. They should know that such attacks may occur and carefully check the domain before any click. Especially if the letter seems suspicious.
- On the other hand, we can also act proactively. Find which domains are similar enough to company brand and can be potentially used for phishing or other types of fraud. Then work with owners or registrars of such domains directly.
However, tracking down potentially malicious domains is not an easy task. Where should we take the lists of all registered domains? What does “similar enough” really mean? Fortunately, there are services that greatly facilitate this task.
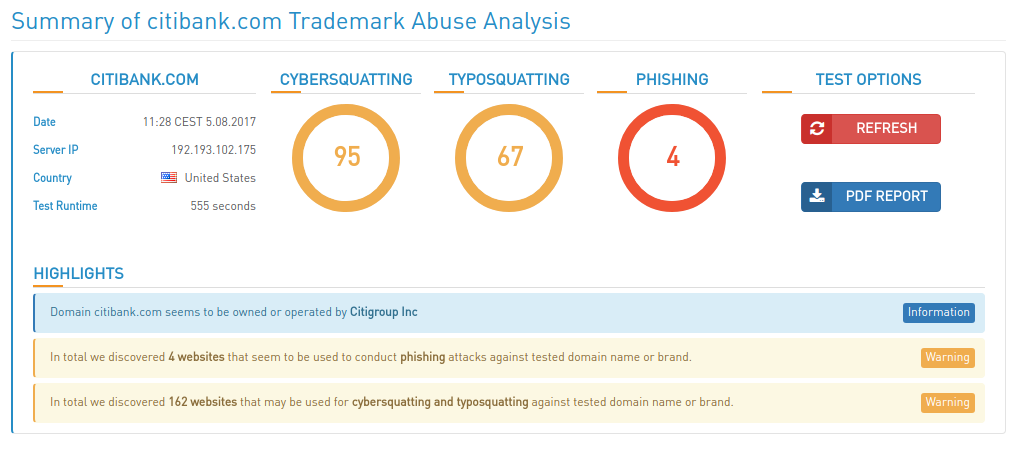
And today I would like to write you about a new free service by High-Tech Bridge – Trademark Abuse Radar. BTW, I already wrote earlier about their cool free service and API for SSL/TLS server testing, you can also check this out 😉
Everything is simple. Just enter the domain name you are interested in and in a few minutes you will receive a full report. No authorization for analysis is required, because the report is built on external and open data.

I chose the Citibank (citibank.com) as one of the most famous banking brand in the world. Let’s see what Trademark Abuse Radar will find.
Continue reading →