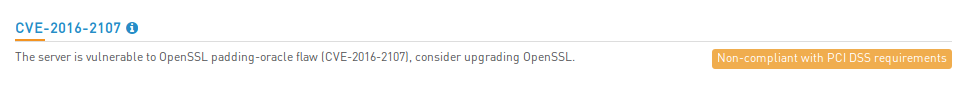
About a month ago I wrote a post “When a free scanning service detects vulnerabilities better”. This post was about OpenSSL CVE-2016-2107 vulnerability. A free High-Tech Bridge scanning service was detecting this vulnerability, but commercial Tenable Nessus/SecurityCenter not.
We communicated with a Tenable customer support and it brought some results. Now you can find a new plugin #91572 “OpenSSL AES-NI Padding Oracle MitM Information Disclosure” in Nessus plugin search (by CVE id CVE-2016-2107).
I have tested a vulnerable server with High-Tech Bridge service:
Then scanned it with Nessus. Note, that you can select only one plugin “General -> 91572” in your Nessus scan policy to speed up the scanning. This plugin does not have any dependencies.
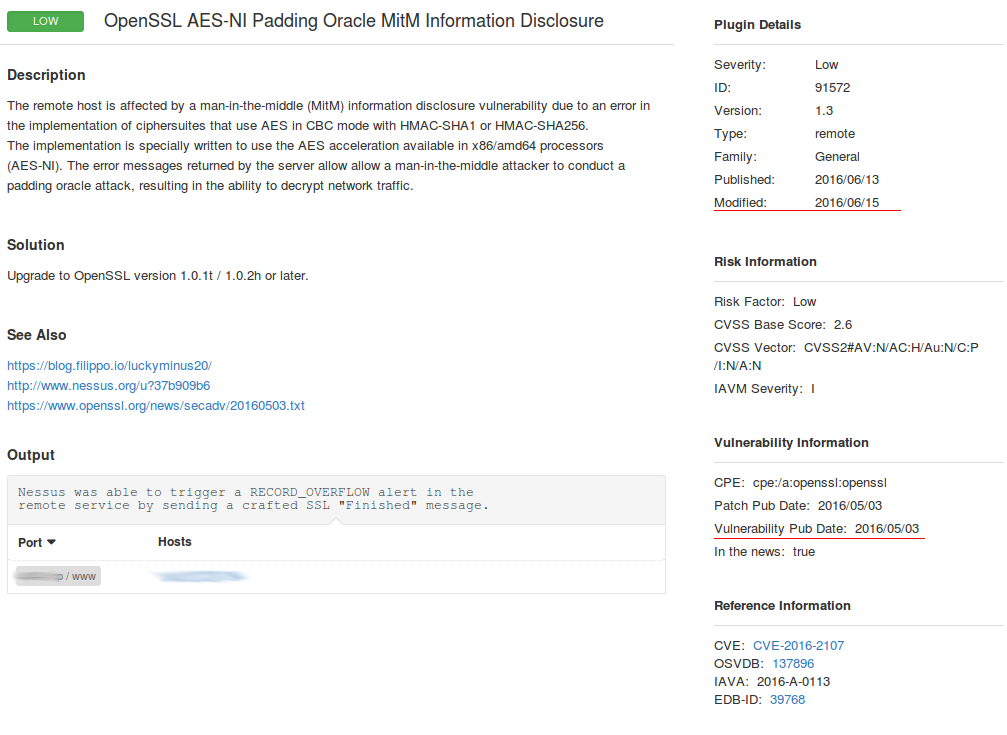
As you can see, now the Nessus detects this vulnerability correctly.
The screenshot shows that it took more than a month, but after all this detection plugin was realized. And I hope my support tickets also played some role.
Therefore, I recommend, if it is possible, to validate your vulnerability scan results with additional scanners/services and REPORT your vendor the differences. It will help to achieve a better security level for your infrastructure and will make the your vendor’s products better.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: When a free scanning service detects vulnerabilities better | Alexander V. Leonov
Pingback: Exporting Nessus scan results to Splunk | Alexander V. Leonov