Last week, March 14, Forrester presented new report about Vulnerability Risk Management (VRM) market. You can purchase it on official site for $2495 USD or get a free reprint on Rapid7 site. Thanks, Rapid7! I’ve read it and what to share my impressions.
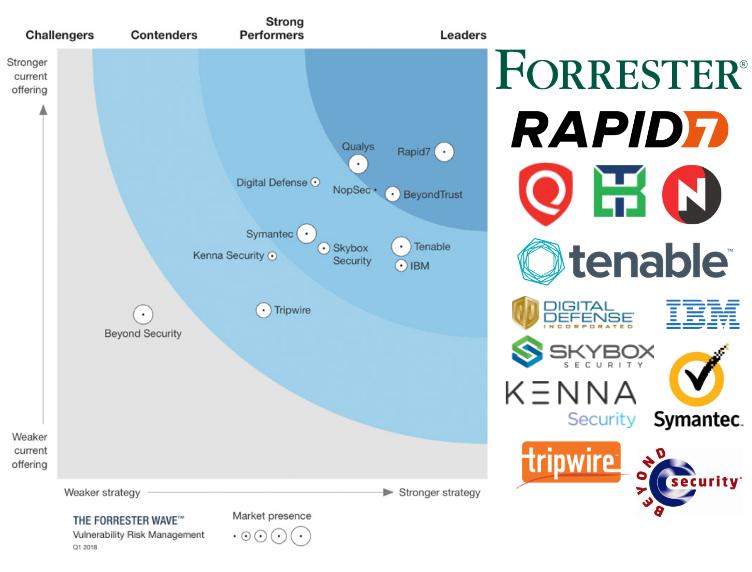
I was most surprised by the leaders of the “wave”. Ok, Rapid7 and Qualys, but BeyondTrust and NopSec? That’s unusual. As well as seeing Tenable out of the leaders. 🙂
The second thing is the set of products. We can see there traditional Vulnerability Management/Scanners vendors, vendors that make offline analysis of configuration files and vendors who analyse imported raw vulnerability scan data. I’m other words, it’s barely comparable products and vendors.
The main point of the report is that modern VRM solutions should not only detect vulnerabilities, but also have capabilities in
- Asset Management
- Patch Prioritization
- Threat Intelligence
- Reporting and SLA tracking
Well, for me it’s awesome if the product has all these advanced features. But still the most important for me is how the product detects vulnerabilities. Because without detected vulnerabilities other functionality will be just useless. And if you set the existence of such features as evaluation criteria, solution with the best knowledge base, the most effective vulnerability checks, but without additional functionality will be an outsider. I also didn’t like that “Vulnerability Enumeration” criteria has such a low weight.
So, Forrester used 22 criteria to evaluate 12 products of 12 vendors:
- Beyond Security (AVDS)
- BeyondTrust (Retina CS)
- Digital Defense (Frontline VM)
- IBM (QRadar VM)
- Kenna Security (Kenna Security)
- NopSec (Unified VRM)
- Qualys (Threat Protection)
- Rapid7 (Insight VM)
- Skybox Security (Skybox Security Suite)
- Symantec (Symantec CCS)
- Tenable (Tenable.io)
- Tripwire (Tripwire IP360).
Why only these vendors? Vendors needed to have more than 300 enterprise customers, to be well-known among the Forrester clients and to have integrations with different Threat Intelligence sources (well, the last one is, imho, controversial). Forrester used vendor surveys, product demos and customer reference calls as information sources.
The result you can see on a picture above. In the upper left corner located vendors with the strongest current offering and strategy. Vendor with bigger market presence has bigger circle marker.
To my taste, product descriptions are high-level and chaotic, They sometimes look like vendor’s marketing material, sometimes like a personal opinion. After reading this report, I need to say that I prefer the style of Gartner more with all the pros and cons.
In conclusion
It’s great that Forrester makes reports on this topic. But the set of products, criteria, weight, marks and product descriptions are pretty controversial. This report can be used as a list of relevant products, but I would not recommend to make final decisions based on this comparison.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Hi Alexander,
Do you ever test new scanners to see the latest in VA?
If so, I would love to have you test Warden and get your unbiased opinion.
You can scan your machines and your websites with it.
Thank you,
Tony
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov
I was surprised they didn’t include Tenable.SC in their evaluation.
Pingback: Vulnerability Management Product Comparisons (October 2019) | Alexander V. Leonov
Pingback: Также были предложения сделать полноценную карту отечественных Vulnerability Management вендоров, чтобы уж там-то точно всех упомянуть | Александр В.