A week ago I was at PHDays (Positive Hack Days) 2016 conference. For those who don’t know, there are two main events for security practitioners in Russia: PHDays in May and ZeroNights in November. Day-Night. Like this play on words. =)

So, it was my 6th PHDays. I visited them all. But on this one for a first time I was as an ordinary visitor and not from organizers side. To be honest, I have never participated in organizing of PHDays, and just seen the final result. So, nothing changed much for me. As usual, organization was at very high level. And it’s not just my opinion, but the opinion of many participants.
Sad things first. And they are likely sad only for me. You know my passion to vulnerability assessment/management systems and scanners. So, despite the fact that Positive Technologies are the organizers of this event and Maxpatrol is still their’s flagman product, it was hard to hear anything related to vulnerability assessment/risk assessment/threat intelligence on PHDays. Isn’t it strange? Could you imagine this at Qualys QSC or Tenable event? Nothing much about critical controls and IT compliance in general.
It’s clear that vulnerability assessment is not already in trends in Russia. All are crazy about SIEM and slightly less about Anti-APT and SCADA security. Sad, but true.
Anyway, I have seen many interesting presentations about honeypots, computer forensics, machine learning and security startups. I also visited a SIEM roundtable with representatives of Positive Technologies, First Russian SIEM (RuSIEM), ArcSight, IBM Qradar, Splunk, and Cisco Systems. More details under the cut.
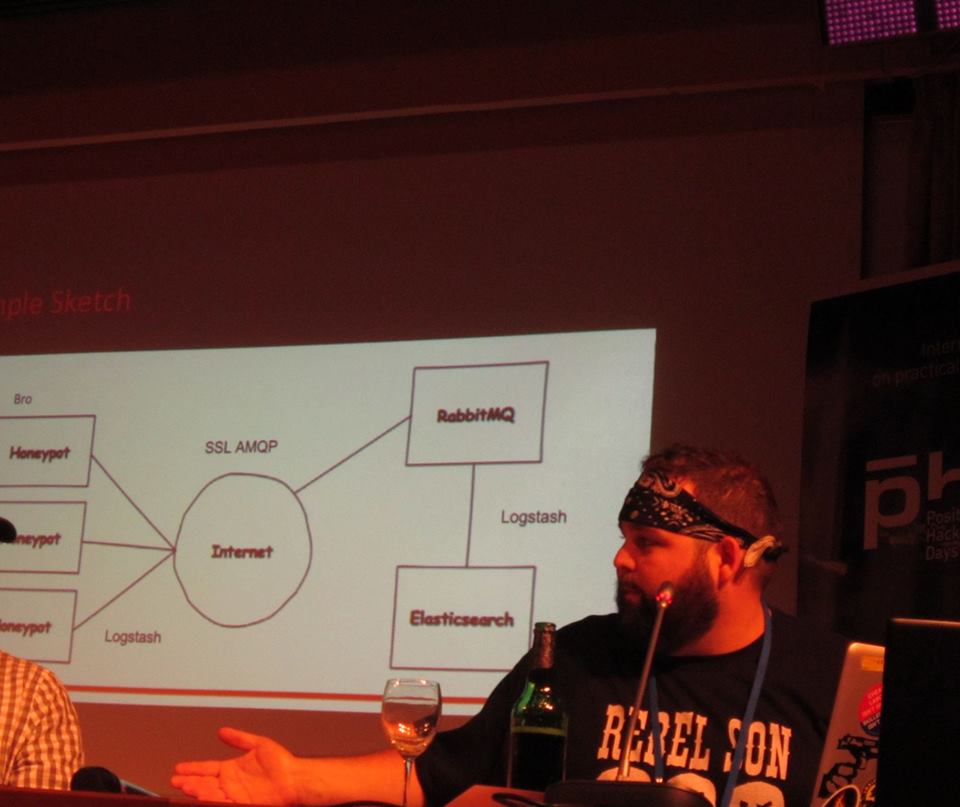
Very positive report by Terrence Gareau “Building Honeypots to Monitor DDoS”
At pictures you can see software components that were used, schematic diagram. Url of the project: github.com/kingtuna/Hybrid-Darknet-Concept

Mona Arkhipova “Enterprise Forensics 101: investigate incidents in corporate systems”. There wasn’t free seats in the room. And even a free space. Literally. Good thing I came early.

I paid attention to this slides:
- Where to begin (it was good to hear about gathering non-technical details)
- What to do after data collection (no universal recipe exist)
- Where to look if you are suspecting an insider
- What is special for blood enterprise forensics (check all related systems)
- Forensics tools used in QIWI
- Reporting requirements
A lot of good words was told at PHDays about Qiwi Security Team (and Kirill Ermakov personally) in the various reports: about their practice of internal pentests with competing blue and red teams, about their practice of SIEM using. They’re great.
The second day of PHDays VI began with the report “Realization of Self-Learning Techniques in WAF” by Vladimir Lepikhin. It was about the math used in Positive Technologies Application Firewall. Hidden Markov models. I liked the examples with google search queries. Very clear. There was a question: what if the attacker will retrain WAF feeding it with a a large number of invalid requests? It seems possible. Isn’t it funny? =)



Cool presentation “How to Start an Information Security Business” by Alexander Bondarenko.
He is a founder of Russian GRC vendor R-Vision. It is a 5 year old startup, with 15 people in the team. They work in Russia and CIS countries.

Key takeaways:
- Don’t be afraid of taxes too much. Sales tax in the Russian Federation is 6-3%. With the salaries tax about 50%, but there are options: registration as an IT-companies, Skolkovo, pay dividends not a salary.
- Should you open business in Russia or abroad? If you know the market and the subject area, leave.
- It is better to start a business before you got family and children, it’s more difficult after.
- It’s great to make products for geeks, but it’s not a business. The product is not only a technology, it should be beautifully presented.
- You need to sale your product by yourself. No body need it more than you.
- You will need different people. They can be hired, but you need money, or you can loKirill Ermakovok for partners (as carefully, as you looking for a wife).
- Always look for opportunities, for example, compliance.
- Business plans, numbers, papers. Someone from your team should be engaged in it, or is not a business.
- There are a lot of rumors about Skolkovo, but it can be useful. For example it can provide free exposition at InfoSecurity London.
- Foreign investors need a story abroad. As soon as possible try to enter foreign markets.
- Entrepreneurship has some risks, but they are not as big as the risk of living after 60 on a pension, that does not even exist.
SIEM roundtable was also very nice. There were representatives of Russian competing SIEM vendors: Positive Technologies and First Russian SIEM (RuSIEM). I’ve got a lot of fun on their swordplay. It was also very interesting to hear about ArcSight, IBM Qradar, Splunk, and, of course, Cisco Systems.

The main tricky questions of Alexey Lukatsky (CISCO) and participants from the audience (answers are also available, but it is better to look recorded video, if you are interested):
- According to the survey 74% of participants implemented SIEM in their organizations have not noticed any changes in incidents statistics. What is the reason? Vendors in fact admitted that statistics in Russia is even worse.
- Question about the definition of SIEM. It’s interesting, that in the rest the world SIEM is mainly about compliance, but in Russian it is a platform for information security management, and often a “silver bullet”, which, according to consumers, must be able to collect, correlate, and show any event from any IT security source.
- Question about the process of creating SIEM rules. If you do not have hackers in your organizations, how will you develop correlations that works well? All vendors except PT recognize that most of out of the box rules can’t be used in practice and customer / integrator should write rules by themselves. PT expressed a thesis that SIEM needs to know everything and, in fact there should be one platform that includes Vulnerability Management, Asset Management, etc.
- Question from the audience: is SIEM a box or a process. Interesting, but controversial thesis of PT, that SIEM may be a box, as IDS / IPS and antivirus may be.
- Question about Russian SIEMs. Domestic vendors have told their stories and views on import substitution.
- Question about Elasticsearch use and import substitution.
- Question about time synchronization and GPS / GLONASS.
- Question about SIEM protection against unauthorized access.
- Question about performance.
The final wishes (for customers): do not expect a silver bullet, set realistic goals and do not believe marketing, make reference visits and pilots.
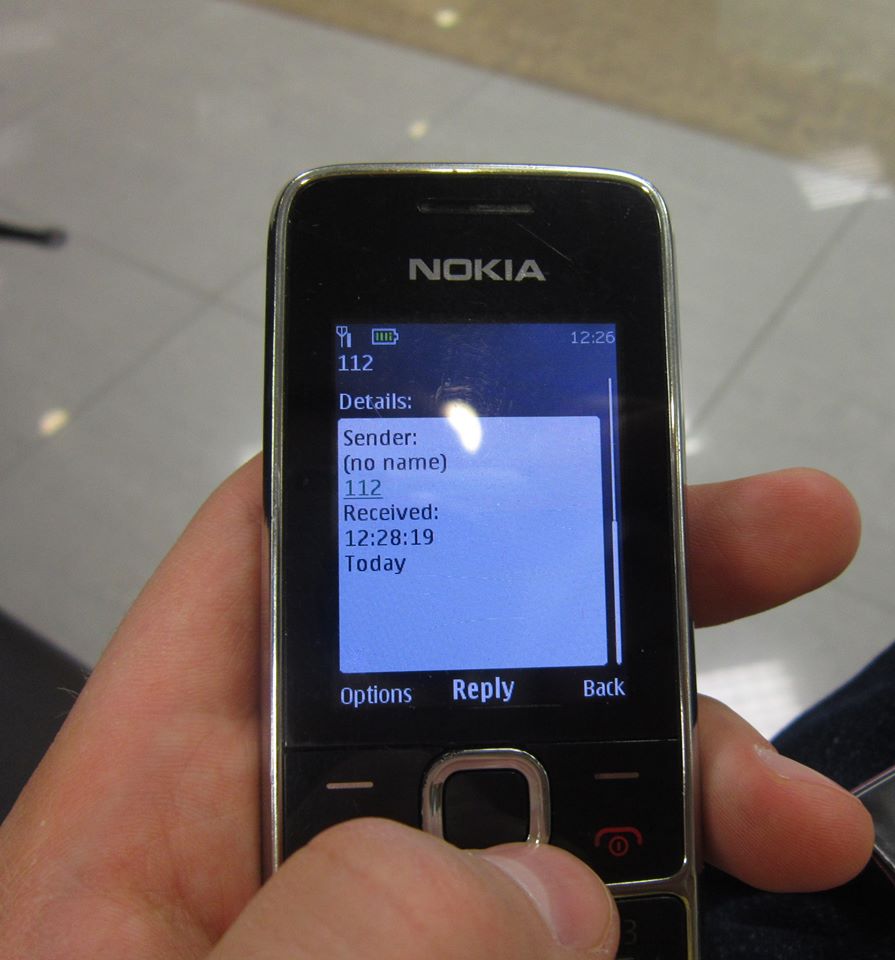
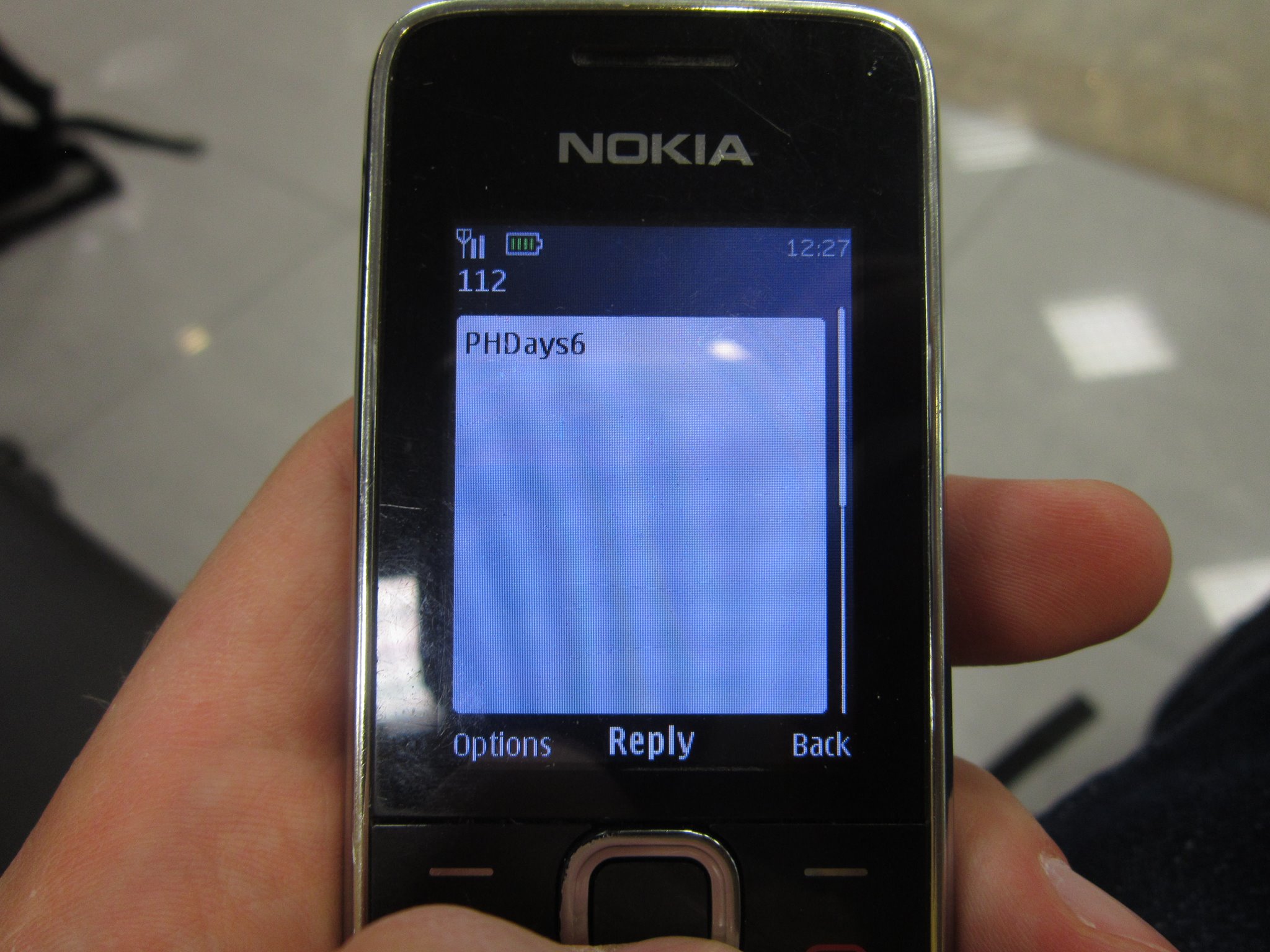
And do not relax an a hacker conference . You can get arbitrary sms from arbitrary phone numbers.
And you can get your Telegram hacked (rus) if you connect to the fake “PHD”, “Beeline_WiFi_FREE”, or “MosMetro_Free” wi-fi hotspot.
I’ve never been a fan of CTF competitions. But this year CTF/CityF was different. Besides attacking teams there were teams of defenders and SOC. Unusual format. As for me, it was much more realistic and entertaining.
Vulners defenders team acted great. They collected as much as 5 awards!

I have also an inside, that one of the SOC teams actively used Qualys products, including fresh Qualys ThreatPROTECT.
It is a pity that we do not yet know all the details of the PHDays CityF. I think it would be a very useful demonstration of different products and techniques. I hope that the organizers, despite the criticism, will repeat this CTF format next year.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Tenable doesn’t want to be Tenable anymore | Alexander V. Leonov
Pingback: QSC16: from Vulnerability Management to IT Visibility | Alexander V. Leonov
Pingback: Post-SIEM black boxes | Alexander V. Leonov