Hi guys! I was on vacation this week. So I had time to work on my Vulristics project. For those who don’t know, this is a framework for prioritizing known CVE vulnerabilities. I was mainly grooming the HTML report.
I added a logo at the top, set a max width for the report, added a timestamp when the report was created so you can now see how fresh it is. I have combined CVSS and Vulristics score statistics in two parallel columns.
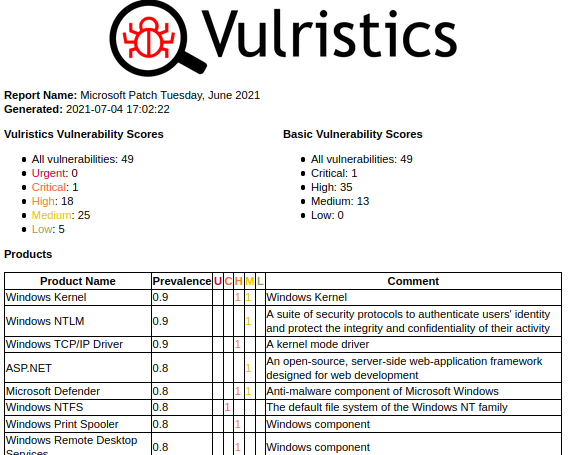
But the main new feature is the tables of vulnerable products and types of vulnerabilities. The products are sorted by “prevalence”. You can review this list and ask yourself if this order is correct in your opinion or change the “prevalence” values for some products in the config dictionary. For software products with unknown “prevalence”, you will see the comment “Unclassified Product”.
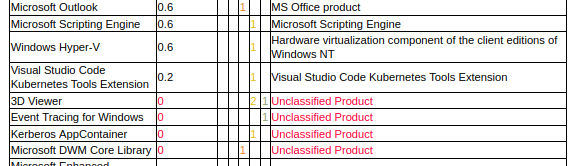
Currently, “prevalence” indicates that people are more likely to face certain products and vulnerabilities in those products. SharePoint, as a popular enterprise product, will have more “prevalence” than, for example, an optional extension for VSCode. And that’s fine if you’re using Vulristics as an analyst or consultant and want to deal with new vendor advisories, for example. But if you want to use Vulristics to prioritize vulnerabilities in your infrastructure, you will probably need to use “prevalence” values that reflect what is being actually used in your particular infrastructure. Because you will not worry about SharePoint vulnerabilities if it is not used in your company, and VSCode extension vulnerabilities become extremely important if all of your developers use this particular extension. So, for this use case, we need to get IT Asset Management information about hosts and installed software. I hope I will add this functionality to Vulristics in the foreseeable future.
But let’s go back to the report. In cases where for some reason it was not possible to find a vulnerable product, you will see “Unknown product” and related vulnerabilities. To get rid of this, configure product detections.
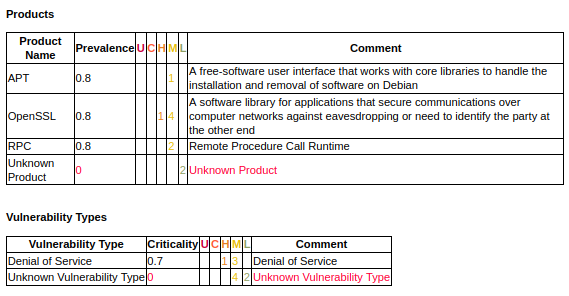
The table with the types of vulnerabilities is similar. In the table you can see how many vulnerabilities of different types and criticalities you have. Pay attention to the “Unknown Vulnerability Type”, which requires configuration of detection rules.
I find this view to be very helpful. It shows the correct workflow for Vulristics. You run the script. For some CVEs it works fine, for some it doesn’t, and shows problems. So you tweak Vulristics for these cases and it starts to work better. I think it is very important to make all problems visible, not sweep them under the rug . Not to give false hopes that everything will always work fine automatically and out of the box, as some other vendors do.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
