WannaCry about Vulnerability Management. Nearly all mainstream media wrote today about massive ransomware attacks around the world: 16 medical institutions in UK, strong rumours that huge companies in Russia, and even Russian Ministry of Internal Affairs suffered a damage.
At this moment Kaspersky recorded more than 45,000 attacks in 74 countries around the world, but mostly in Russia. During the attack WannaCry malware encrypts data with the extension “.WCRY” added to the filename – that’s why it is called this way.
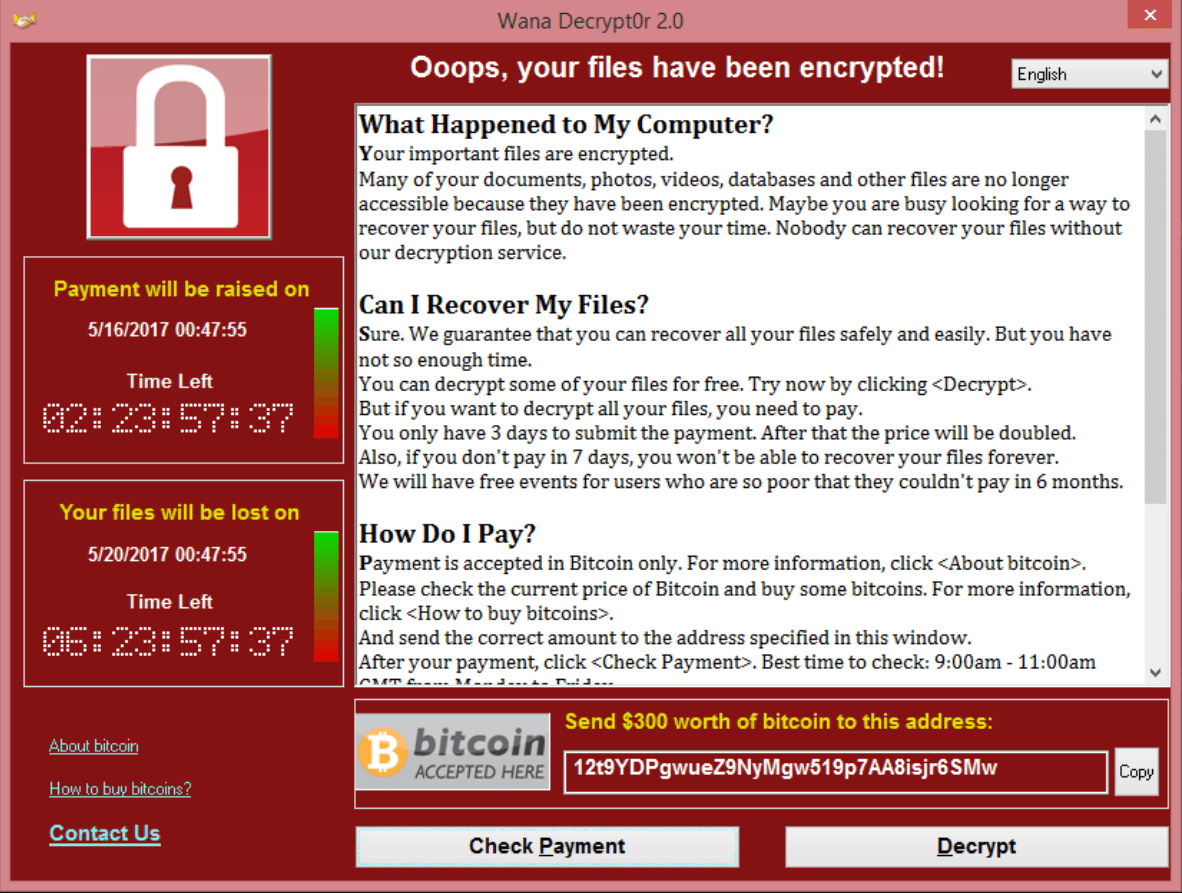
What I like in this WannaCry story, that it’s actually all about Vulnerability Management.
WannaCry uses EternalBlue exploit to attack computers running the Microsoft Windows operating system.
Maybe this exploit uses some unknown 0day vulnerability?
No, patch MS17-010 for this vulnerability was published 14.03.2017, month ago. It was marked as critical.
Maybe this vulnerability was hard to detect using vulnerability scanners?
No, here you can see Nessus local check plugin and remote uncredentialed check plugin. Don’t have budget for Nessus Professional? Here are similar vulnerability checks for free and open source OpenVAS: local check and remote uncredentialed check.
Maybe this vulnerability was hard to filter because of some weird CVSS vector and score?
No, Access Vector: Network, CVSS Base Score: 9.8. It was hard to miss this vulnerability in scan results.
Maybe this vulnerabilities were not discussed publicly?
No. Almost all media wrote about the NSA exploits Leaked By Shadow Brokers. It was breaking news.
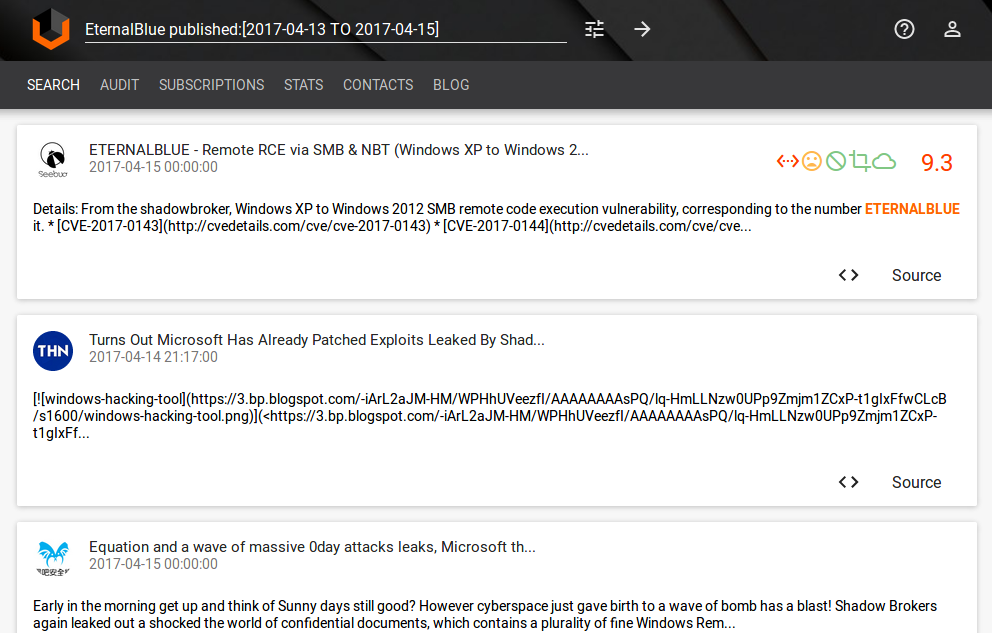
And it was obvious that very soon this exploits will be actively used by ordinary criminals. It was just a matter of time.
So, what can we tell about organisations that were massively affected by WannaCry?
They probably have some problems with Patch Management process. For some reason, MS17-010 patch was not installed automatically using standard Microsoft tools.
They probably have problems with Vulnerability Management process. For some reason, Security Team have not detected the fact that this critical vulnerability was not fixed for a long time, and did not force patch process.
It’s also important if there were backups (universal solution against CryptoLockers) and updated antivirus knowledge bases (definitely not a panacea, but still better than nothing).
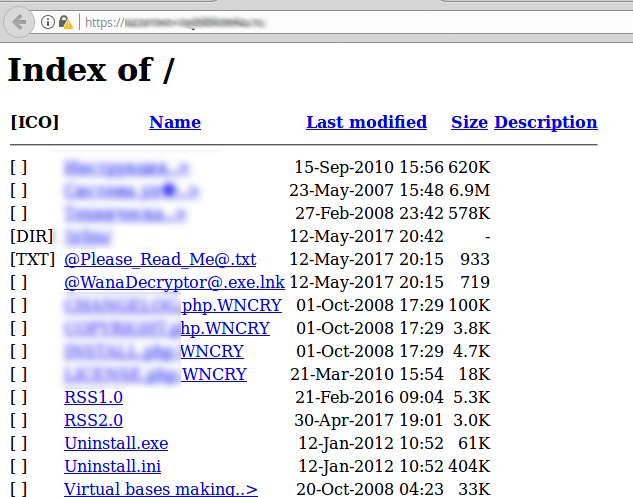
In conclusion, if you are curious how the result of attack looks like, you can use this simple Google dork: “WNCRY” intitle:”index of”. You will get plenty of website, hosted on vulnerable Windows machines.
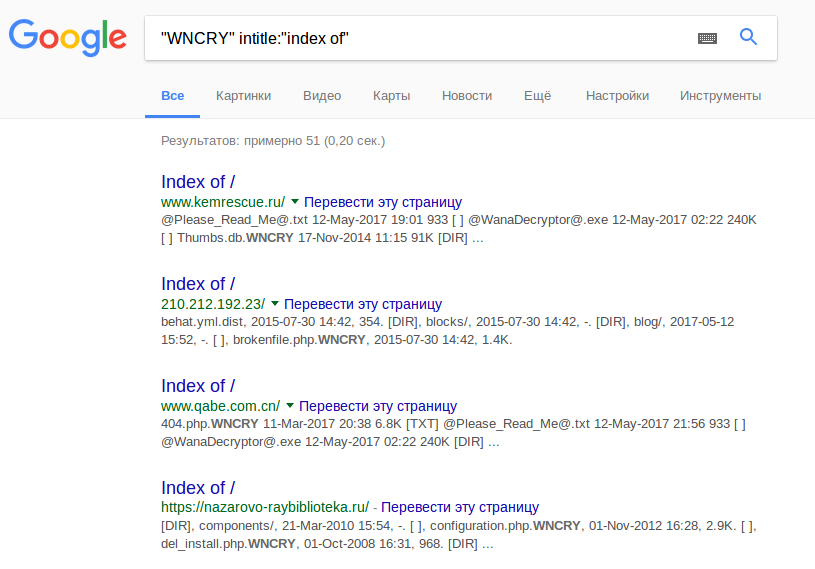
WannaCry was able to encrypt files in site directory, including index.html, so you can now see file structure of the site. It also created files @Please_Read_Me@.txt, @WanaDecryptor@.exe or @WanaDecryptor@.exe.lnk in affected folders.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: New VulnersBot for Telegram with advanced searches and subscriptions | Alexander V. Leonov
Pingback: PHDays VII: To Vulnerability Database and beyond | Alexander V. Leonov
Pingback: GSM Community Edition and lagging OpenVAS Plugin Feed | Alexander V. Leonov
Pingback: Petya the Great and why *they* don’t patch vulnerabilities | Alexander V. Leonov
Pingback: SOC Forum 2017: How I Learned to Stop Worrying and Love Massive Malware Attacks | Alexander V. Leonov
Pingback: MIPT/PhysTech guest lecture: Vulnerabilities, Money and People | Alexander V. Leonov
Pingback: Vulnerability Life Cycle and Vulnerability Disclosures | Alexander V. Leonov
Pingback: Vulnerability Management at Tinkoff Fintech School | Alexander V. Leonov
Pingback: Is Vulnerability Management more about Vulnerabilities or Management? | Alexander V. Leonov
Pingback: Microsoft Patch Tuesday for March 2020: a new record was set, SMBv3 “Wormable” RCE and updates for February goldies | Alexander V. Leonov
Pingback: Microsoft Patch Tuesday August 2022: DogWalk, Exchange EOPs, 13 potentially dangerous, 2 funny, 3 mysterious vulnerabilities | Alexander V. Leonov