Automated task processing with JIRA API. It’s no secret that task tracker is one of the most critical resources of any big organization. The whole working process can be represented as creating, processing and closing various tasks. Without task tracker there will be complete disaster, collapse and anarchy. So, it’s very important to work with this instrument efficiently. And when I write efficiently, I mean in automated way. It’s a blog about security automation after all. 😉
This post will be about Jira task tracker. I have already wrote how Jira can be used in VM Remediation process. That post was mainly about the main principles and how remediation tasks look in Jira WEB-GUI. Now, I will go further and show how to use it as a source of important information and easily deal with daily routine tasks using some trivial scripting. It is all possible because of advanced Jira Rest API.

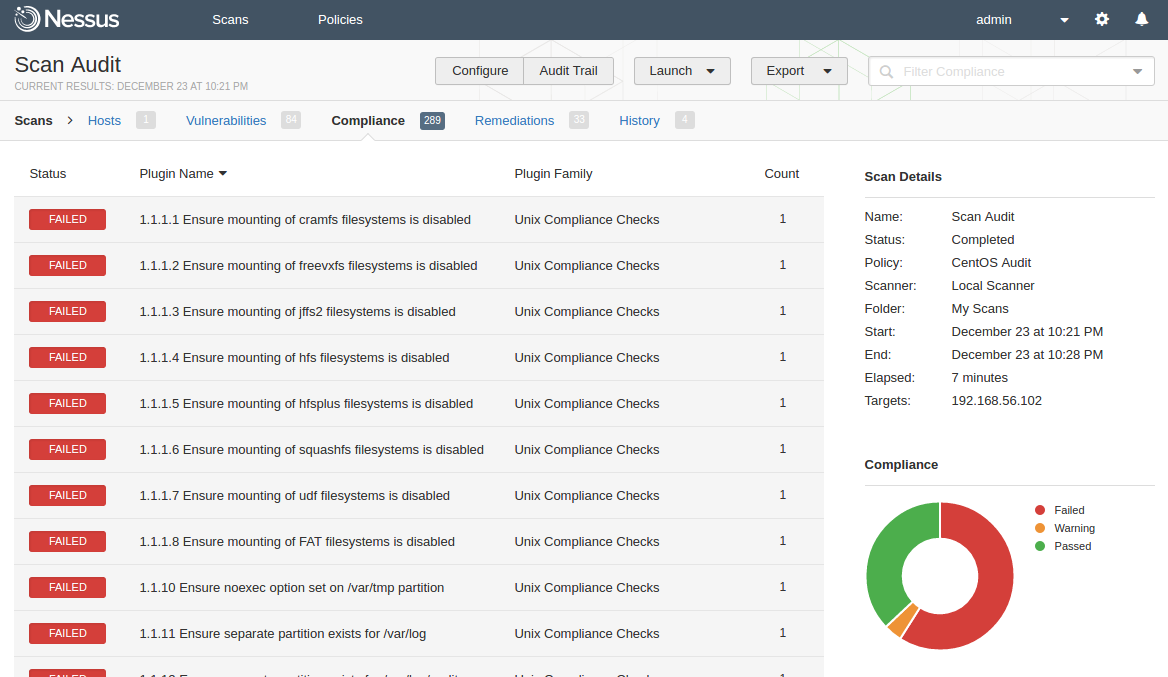
Let’s say we have some regular tasks of some type. For example, to detect vulnerabilities on some hosts using Nessus and make a comment about founded vulnerabilities in the task. You can make a script that we will search for this kind of tasks in Jira, process them, add scan results to the comment and close the task. Of course it works the best when these tasks are also were created with in some automated way, in this case parsing will be much easier.
“Issue”, is the right name for the task in Jira; but I frequently use “issue”, “task” and “ticket” interchangeably. Sorry for this.
So, we need to take this steps:
- Authorization
- Search for existing Jira issues using some search request
- View description, data and comments of the issue
- Download files attached to the issue
- Make some task processing
- Add a new comment to the issue
- Change status of the issue