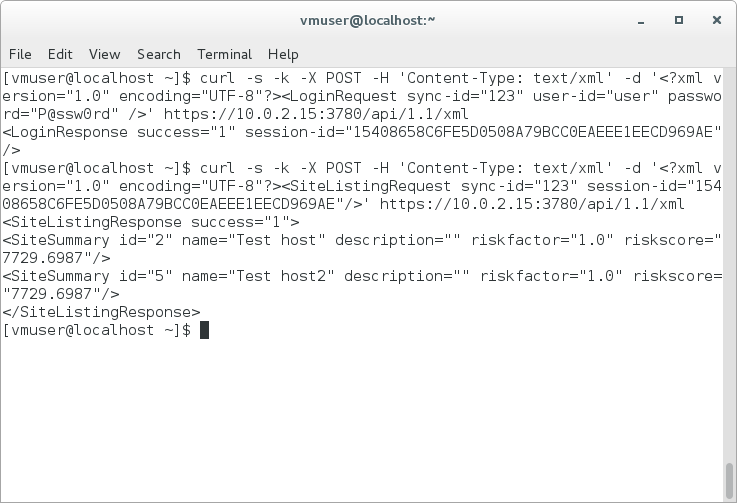
The most serious problem of Vulnerability Scanners is that they are too complex and unpredictable. Usually they don’t affect the target hosts, but when they do, welcome to hell! And if you scan huge infrastructure, tens thousands hosts and more, it’s not “if” the scanner will break the server it’s “when” it will do it.
As a responsible person for Vulnerability Management you will be also responsible for all the troubles that VM product can make in the IT infrastructure. And what will you say to the angry mob of your colleagues from IT and Business when they will be quite curious to know why did the service/server go down after the scan? Actually, it’s not much to say.
Continue reading