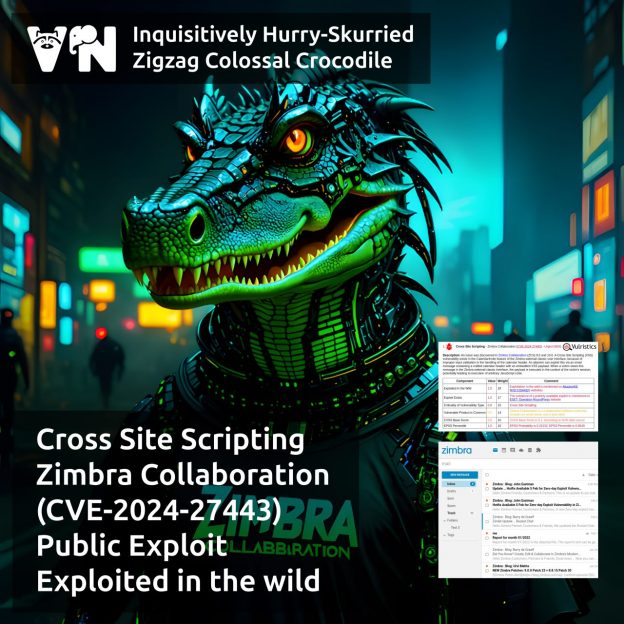
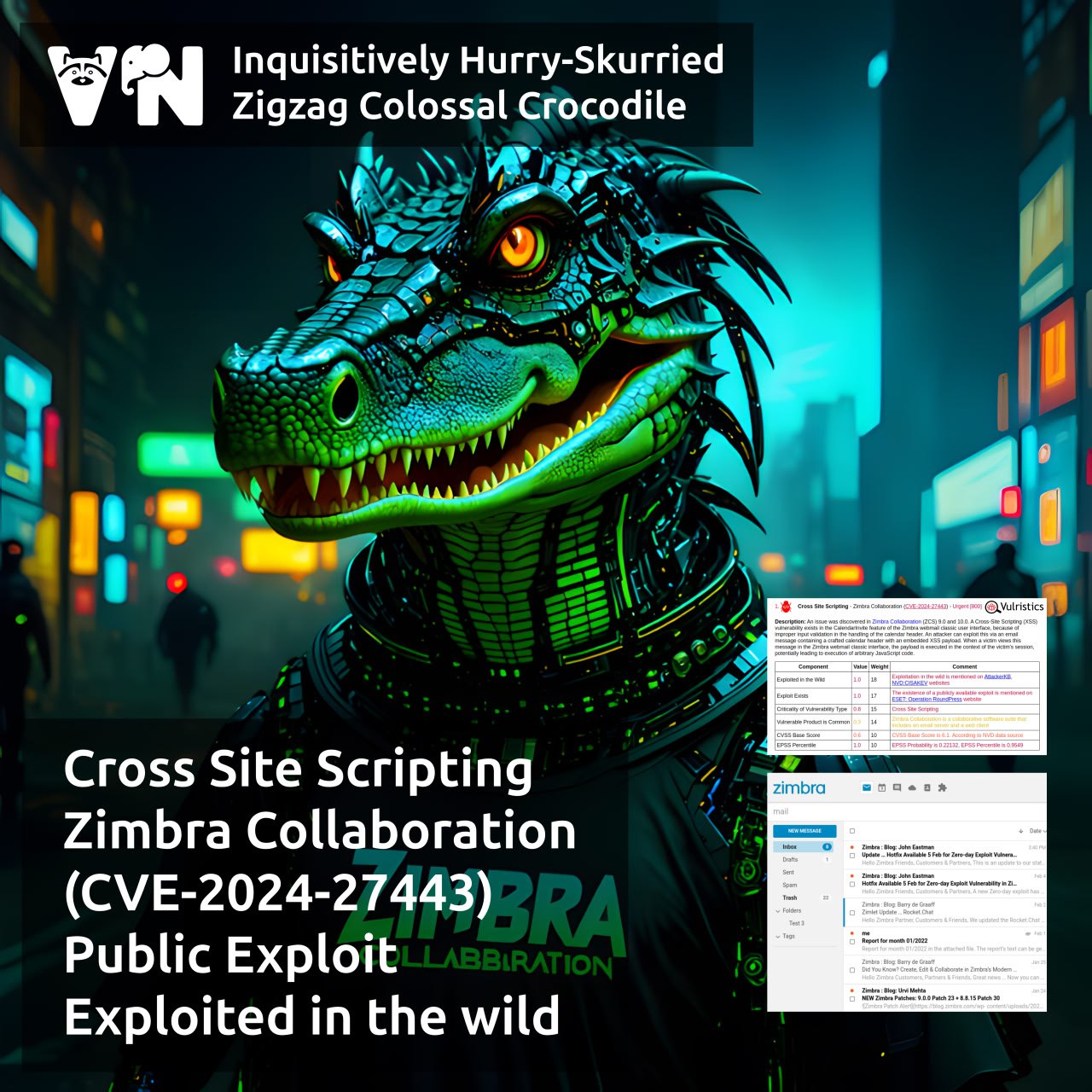
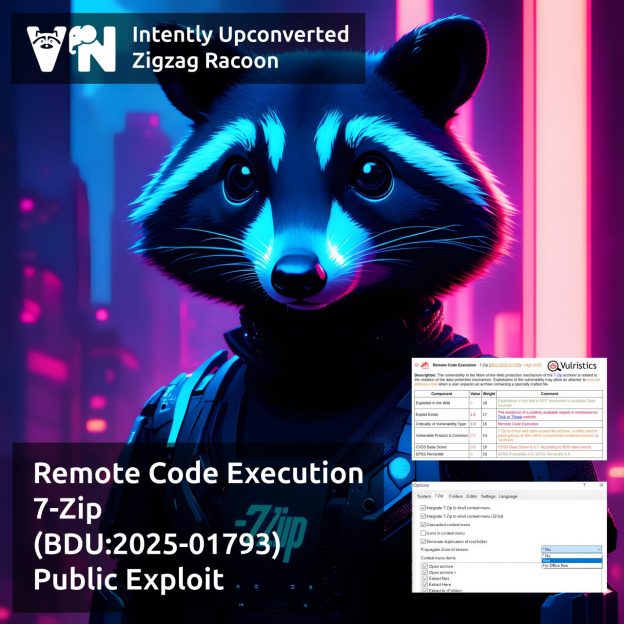
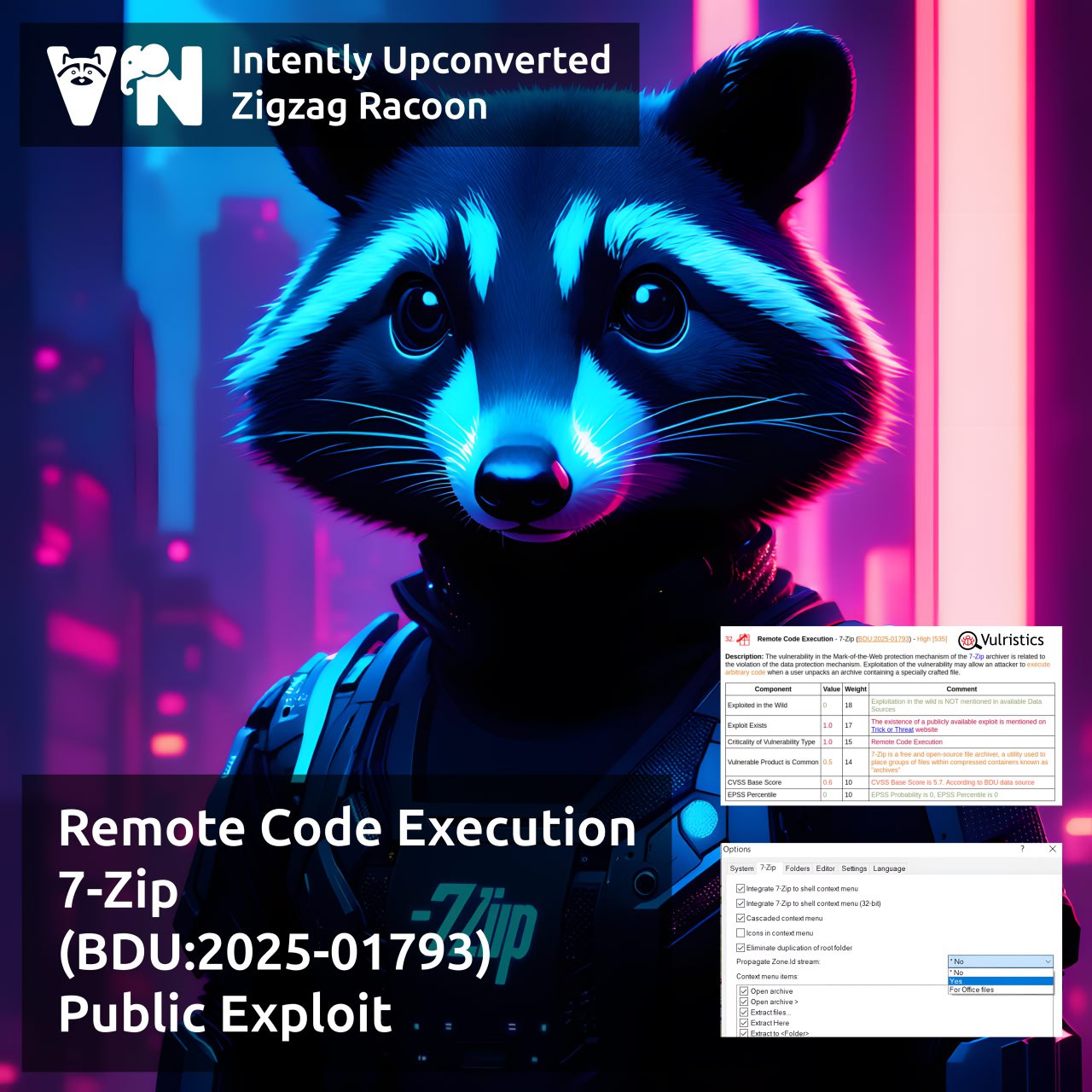
About Elevation of Privilege – Microsoft DWM Core Library (CVE-2025-30400) vulnerability. The vulnerability, patched as part of May Microsoft Patch Tuesday, affects the Desktop Window Manager component. This is a compositing window manager that has been part of Windows since Windows Vista. Successful exploitation could grant an attacker SYSTEM-level privileges. At the time the vulnerability was disclosed, there were signs of in-the-wild exploitation. No details about the attacks are available yet.
According to the Acknowledgements, exploitation was discovered by the Microsoft Threat Intelligence Center, which rarely shares details. 🤷♂️ We’ll have to wait for reports from other researchers or a public exploit. There is currently one GitHub repository with a PoC, but its functionality is highly questionable. 🤔
The previous actively exploited EoP vulnerability in the DWM Core Library (CVE-2024-30051) was patched in May last year.