Let’s Encrypt for shared hosting. I have recently moved my blog to https using free Let’s Encrypt (Linux Foundation Project) certificate.
Let’s Encrypt service works the best, when you have your own server. You just need to configure some scripts that will regularly request new certificates and everything will work automatically. But, even if your site is on shared hosting, it’s still possible to use Let’s Encrypt. You can make the certificate on your machine, I used Ubuntu Linux, and then add them in the web interface of your hoster, of course if this feature is supported. Certificate will be valid for 4 month, and then you will need make a new one.
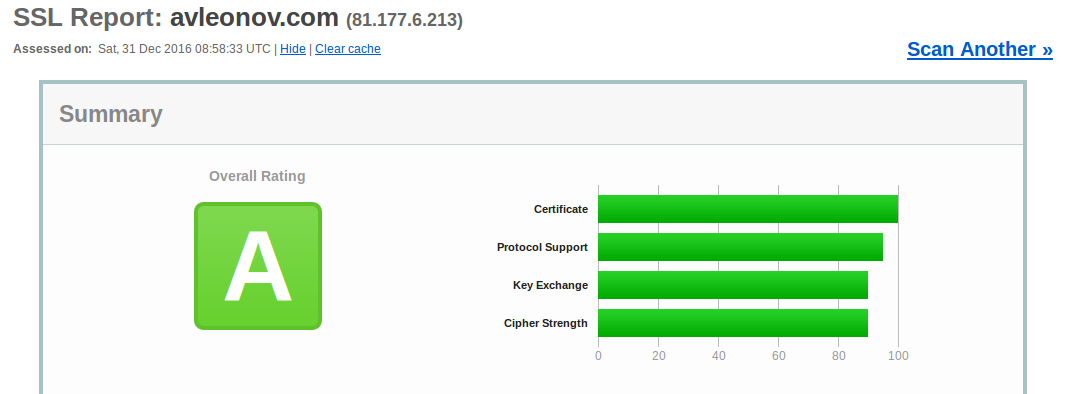
To say the truth, I did it because search engines and browser vendors will discriminate http-only sites very soon. And, of course, for fun. Green lock icon in address bar looks cool. ^_^
Installation
First of all, you will need to download and run certbot installation script:
wget https://dl.eff.org/certbot-auto
chmod a+x ./certbot-auto
./certbot-auto
Now launch certbot
cd ~/.local/share/letsencrypt/bin/
sudo ./certbot certonly --manual
Input the data:
- Email for contact
- Agree with Terms of Service
- Domain name(s)
- Agree that your IP will be logged.
Approve that you control the domain name. I think this way is the best for the shared hosting. You just need to create a new file on your website:
Make sure your web server displays the following content at
https://avleonov.com/.well-known/acme-challenge/kOMy3BD_bx6_q2ii1SLjgdn00Z74PDW43mRZxrOmX40 before continuing:kOMy3BD_bx6_q2ii1SLjgdn00Z74PDW43mRZxrOmX40.G1K1JWvR23OjJgtT7zA8R1XA-hPTlT35TREKxOE08_g
Now you can get your certificate:
IMPORTANT NOTES:
– Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/avleonov.com/fullchain.pem. Your cert will
expire on 2017-03-30. To obtain a new or tweaked version of this
certificate in the future, simply run certbot again. To
non-interactively renew *all* of your certificates, run “certbot
renew”
– If you lose your account credentials, you can recover through
e-mails sent to me@avleonov.com.
– Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
– If you like Certbot, please consider supporting our work by:Donating to ISRG / Let’s Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Here they are:
sudo cp /etc/letsencrypt/live/avleonov.com/fullchain.pem ~/Desktop/fullchain.pem
sudo cp /etc/letsencrypt/live/avleonov.com/privkey.pem ~/Desktop/privkey.pem
Upload them in the web interface of your hosting provider.
What’s next?
If you use wordpress, I can recommend “Really Simple SSL” plugin to configure everything related to SSL automatically.
You can also make redirection from http to https in .htaccess file in the root of your site:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteCond %{ENV:HTTPS} !=on
RewriteRule ^.*$ https://%{SERVER_NAME}%{REQUEST_URI} [R,L]
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Could you please tell me how you got the URL
“Make sure your web server displays the following content at
https://avleonov.com/.well-known/acme-challenge/kOMy3BD_bx6_q2ii1SLjgdn00Z74PDW43mRZxrOmX40 ”
The part after acme-challenge? I am trying to install letsencrypt cert on hostgator-hosted website and dont have terminal access on it. Do you think this is possible?
Hi, Abhi. Well, certbot script generates url with “kOMy3BD_bx6_q2ii1SLjgdn00Z74PDW43mRZxrOmX40”. It is just a file name, which you can create on your site using ftp access or using some web-gui of your hosting provider. I suppose, Let’s encrypt on their side make get request to this url, and if they see, that file exists and file content is ok, they return you a certificate for this url.