Kirill Isox Ermakov, the founder of Vulners, has recently presented a new open-source tool for searching and downloading exploits – getsploit.
Let’s say we want to pentest some WordPress blog. For example, this website avleonov.com. We can get WordPress version simply using curl:
$ curl -s https://avleonov.com | grep "generator"
<meta name="generator" content="WordPress 4.7.1" />
Ok, let’s get some sploits using this version:
$ sudo apt-get install git
$ git clone https://github.com/vulnersCom/getsploit
Cloning into 'getsploit'...
remote: Counting objects: 32, done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 32 (delta 13), reused 30 (delta 11), pack-reused 0
Unpacking objects: 100% (32/32), done.
Checking connectivity... done.
$ cd getsploit/
$ ./getsploit.py "title:WordPress AND title:4.7.1"
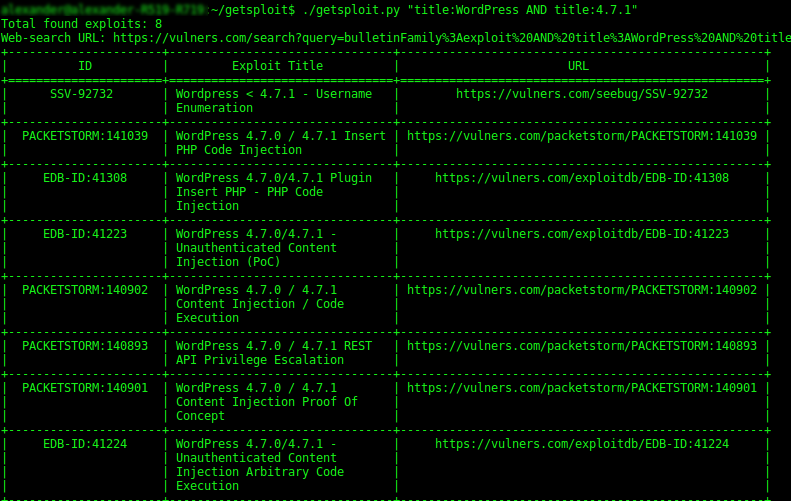
As you can see on the screen shot, getsploit makes a search request to vulners.com: bulletinFamily:exploit AND title:WordPress AND title:4.7.1 and matches objects in Immunity Canvas, DSquare Exploit Pack, Exploit-DB, Metasploit, Packet Storm, Malware exploit database, SAINTexploit™, seebug.org, Vulnerability Lab, 0day.today and Zero Science Lab.

Ok, great. PACKETSTORM:140902 “WordPress 4.7.0 / 4.7.1 Content Injection / Code Execution” in search results seems interesting and other exploits may be useful as well.
Let’s download them all using the same command with “-m” key:
$ ./getsploit.py -m "title:WordPress AND title:4.7.1"
Downloaded files:
$ ls titlewordpress-and-title471/
edb-id41223.txt edb-id41224.txt edb-id41308.txt packetstorm140893.txt packetstorm140901.txt packetstorm140902.txt packetstorm141039.txt ssv-92732.txt
Code of PACKETSTORM:140902 exploit:
$ cat titlewordpress-and-title471/packetstorm140902.txt | head
`# Exploit Title: WP Content Injection Shell Exploit
# Date: 31 Jan' 2017
# Exploit Author: Harsh Jaiswal
# Vendor Homepage: http://wordpress.org
# Version: WordPress 4.7 - 4.7.1 (Patched in 4.7.2)
# Tested on: Bacbox ubuntu Linux
# Based on: https://blog.sucuri.net/2017/02/content-injection-vulnerability-wordpress-rest-api.html
# This will inject js in post, which on execution will change akismet plugin index.php file to our backdoor (brute parameter) :)
# Credits : Marc, Sucuri, Brute
# Lang : Ruby

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
