In this episode, I would like to share my thoughts about the new Vulnerability Management product by Positive Technologies – MaxPatrol VM. It was presented on November 16th, at the Standoff365 online conference (full video in Russian). The presentation and concept of the product were very good. I really liked them. However, as it always happens on vendor’s events, some critical topics were not covered. So I also want to highlight them. I will try to be as objective as possible. Although it is difficult for me, since I have worked in the company for 6 years, and many of my good friends work there.

Positive Technologies is best known in the Russian Vulnerability Management market. The volume of the Russian VM market in 2019 is $40-46 million. The volume of the world market, according to IDC, is $1.2 billion. So the Russian market is ~3% of the world market. And 78% of it is occupied by Positive Technologies products: Maxpatrol 8 and XSpider. Disclaimer: all numbers are from the Maxpatrol VM presentation and I haven’t done fact checking. But in this case, the numbers are not so important.
Maxpatrol 8 and XSpider are Vulnerability Scanners. Roughly speaking, they are something like Nessus. They operate in a paradigm of scans, not assets. The goal of the new MaxPatrol VM is to control vulnerabilities across the entire infrastructure. Roughly speaking, it should be something like Tenable.SC or Qualys.
To be honest, Maxpatrol VM is not entirely new. Since 2015, PT has been implementing the Vulnerability Management functionality in MP SIEM (after all, the underlying technologies are the same). But it didn’t work well. Priority was given to core SIEM functionality and not enough VM features were implemented. It’s great that now PT are not afraid to admit this even in the official presentations. Their latest concepts look much better. In fact they are quite similar to my own thoughts on this. But I have some doubts as well. So, let’s go through the main points of the presentation, and I will try to demonstrate some weaknesses of these points.
There can be no good Vulnerability Management without good IT Asset Management
That’s why MaxPatrol VM has built-in IT Asset Management. New hosts can be added using active scanning, traffic analysis (something like Nessus Network Monitor), AD and SCCM integration. It is also possible to import scan in *.csv format or create assets manually by specifying its attributes (ip-address, hostname, operating system and even software list).
I agree that IT Asset Management is very important and ideally we should know about all the hosts in the infrastructure. But I don’t think that collecting all this data is the task of the Information Security department and that VM solution is the right tool for this. In my opinion, it is much better when the IT department is responsible for the IT Assets inventory, they store all the data in some sort of CMDB, and the Security guys only control the quality of the data.
But even if the Information Security department decided to collect information about IT assets from different sources independently (once again – it’s not the best option), it would be wise to do it in a very flexible solution. For example, when I track and classify IT Assets, I put data from different sources into Splunk and create a dashboard that shows the contradictions in those sources for further investigation.
Is MaxPatrol VM suitable for this?
- MaxPatrol VM should have an Asset Management API, to manage IT assets flexibly. In other words, it should be possible to create/delete an asset, edit all of its fields and links. Thus, it will be possible to make custom connectors for other systems that have IT assets related data.
- It should be possible to add custom fields for IT assets.
There is no public Asset Management API in MaxPatrol VM yet, but it doesn’t look too complicated. It’s possible to work with custom fields in MaxPatrol VM (set, select, create dynamic groups), but the whole process is a bit tricky.
I find it pretty rash to rely only on the inventory methods implemented in the MaxPatrol VM. Simply because there are problems with active scanning (network access, scan credentials and permissions, unresponsive hosts, etc.) and traffic detection (what about isolated segments?).
But once again, I think that IT Asset Management, ideally, is not a task of the Information Security department. And if the IT Department is not ready to manage IT assets, there cannot be a full-scaled Vulnerability Management process.
Vulnerability management doesn’t mean pushing IT to install every patch
The task of the VM analyst is to track deviations from the adopted corporate Patch Management policy. In fact, this means monitoring scan coverage, keeping the scan process alive (network access exists, credentials are valid, scanner nodes are active, etc.), and highlighting the issues when the IT Department does not meet remediation deadlines.
This sounds good… But.
A popular Russian anecdote:
The mice came to the Owl: “You are an old and wise owl. We want cats to stop catching and eating us. What should we do?”
The owl tells them: “Mice, you should become hedgehogs. If you will be prickly, nobody will eat you!”
The mice were delighted and ran home, but then returned to the owl again. “Owl, tell us – how can we become hedgehogs?”
And the Owl answered them: “I am solving important strategic issues! Deal with the tactics yourself!”
Now let’s go back to adopting the corporate Patch Management policy and autonomous Patch Management process. I agree that, ideally, it should be so. But from the mouth of a vendor, it sounds like “Mice, you should become hedgehogs”.
How to introduce such KPIs with an iron fist? How could the CISO maintain own position in the process? Why should the IT Department have to volunteer to do a huge amount of extra work to patch things on a regular basis? Why should QA / Dev be happy to test everything after each update? Don’t they have more important things to do? Why should top managers suddenly support such revolutionary changes?
The answer might be automated patching and testing (not necessarily based on solutions of a single vendor). Or at least the development of guidelines for implementing Patch Management process in an organization: strategy, dealing with objections, best practices for automatic vulnerability remediation for different types of systems, etc. IMHO, VM vendors shouldn’t distance themselves from the actual patching.
There should be a separate process for the most critical and exploitable vulnerabilities
A regular patching process with agreed deadlines is great, but there are often times when you need to start patching a specific critical vulnerability immediately. This is normal in the new PT concept. It’s just a different process. So, you can set time ranges for fixing such critical vulnerabilities. But how do you get the most critical vulnerabilities? For better prioritization there is a separate vulnerability feed by PT experts with hand-picked vulnerabilities seen in real attacks and exploited in penetration tests. This is similar to Qualys Threat Protection, but, unlike Qulays, PT provides this feed for free to all MaxPatrol VM users.
I agree that this is important and CVSS is not enough to prioritize vulnerabilities effectively. But it is worth paying attention to the fact that they suggest to prioritize vulnerabilities existing only in one vendor’s vulnerability database. Some vulnerabilities will appear in this database with a long delay or won’t appear at all. This is reality.
IMHO, if a vulnerability management system claims to control the entire infrastructure, it should be able to import vulnerability data from external sources. There must be an API for this. At the moment, MaxPatrol VM does not have such API and it is not planned yet.
It is also important to have a good description of the attack vector for each vulnerability, because this greatly simplifies the task of proving criticality for the IT department.
Unified Vulnerability Management dashboard
All data related to
- IT assets
- common vulnerabilities in regular patch management control process
- critical vulnerabilities in immediate remediation process
- vulnerabilities that PT considers most critical
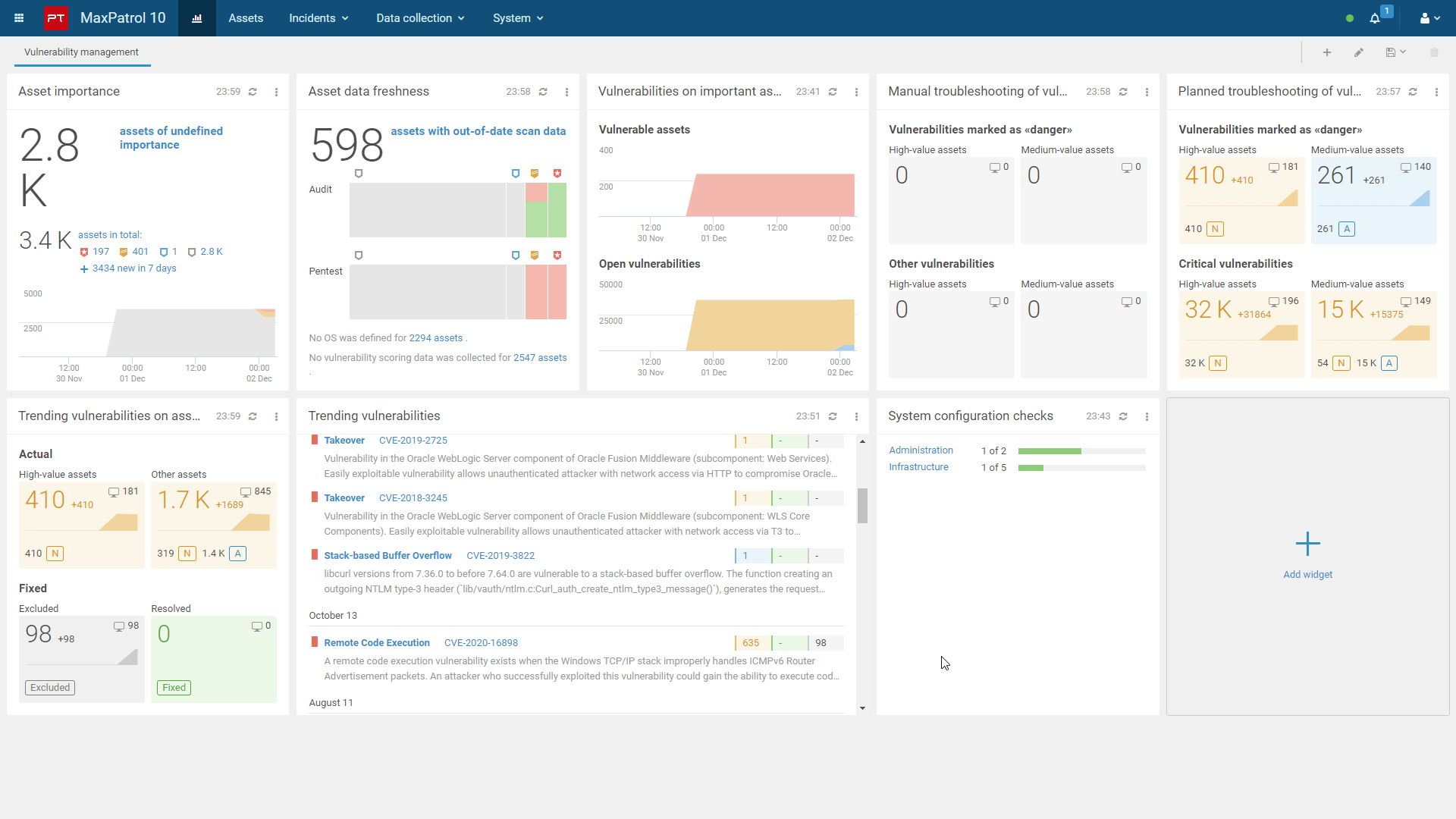
is available in one dashboard in which you can go deeper and investigate possible troubles.
Dashboards really look very convenient and informative. The custom query language allows you to flexibly select IT assets and vulnerabilities. And this can be done through the API.
In conclusion
The need for such a product on the Russian market arose long ago. Here are the results of PT’s study about the complexity of the Vulnerability Management process in Russian organizations (In Russian). I liked it very much. Everything looks like real life there: infrastructure – wild and dark forest, you can’t just scan it – God forbid if something breaks, IT guys do not agree to fix found vulnerabilities using 1001 different excuses and so on. Everything is relevant, except perhaps bragging about the speed of fixing vulnerabilities.
It was difficult to operate in such circumstances using a solution that operates only with scans. Moving to an asset-based approach is definitely a step in the right direction. In addition, the asset inventory made it possible to detect new vulnerabilities without re-scans using just the data collected last time.
There are analogies with other Vulnerability Management products, especially Qualys. IMHO, there are some similarities, but there are still much more differences between them. Qulays is primarily a cloud solution, despite private clouds and other exotics, unlike MaxPatrol VM. And in MaxPatrol VM there is no strict separation between the VM and AM modules. MaxPatrol VM GUI is more flexible. MaxPatrol VM has no cloud agents and no built-in patch management. But PT has its own SIEM and passive scanner. In terms of GUIs, all major vendors (Qualys, Nessus, Rapid7) make quite similar interfaces. What is really different is Vulnerability Knowledge Bases. But all the vendors are pretty quiet about this.
Anyway, my main idea where I would like to end: Positive Technologies is finally back in the Vulnerability Management game! For the past 5 years, the focus has been on SIEM, AST, etc. And I really like these changes. I hope the product will be successful in the market. and the great ideas, including a continuous and comprehensive Patch Management process as a norm, will help transform the IT infrastructures of Russian companies.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
