
Over the weekend, I achieved the first results in my open source vulnerability detection project Vuldetta. 😇
What I managed to do:
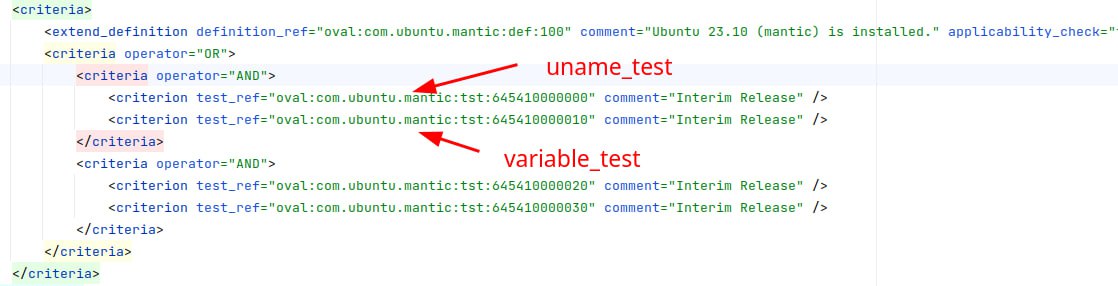
🔹 I parsed Ubuntu OVAL into simple detection rules based on package versions. The structure of Ubuntu OVAL is quite sophisticated, especially when it comes to detecting kernel vulnerabilities (not by packages, but by uname_test and variable_test 🤯). Despite the fact that OVAL content for each distribution version is downloaded in a separate file, distribution version checks are also implemented in OVAL. Now I just go through all the definitions, see which dpkginfo_test are used in the criteria and parse only them.
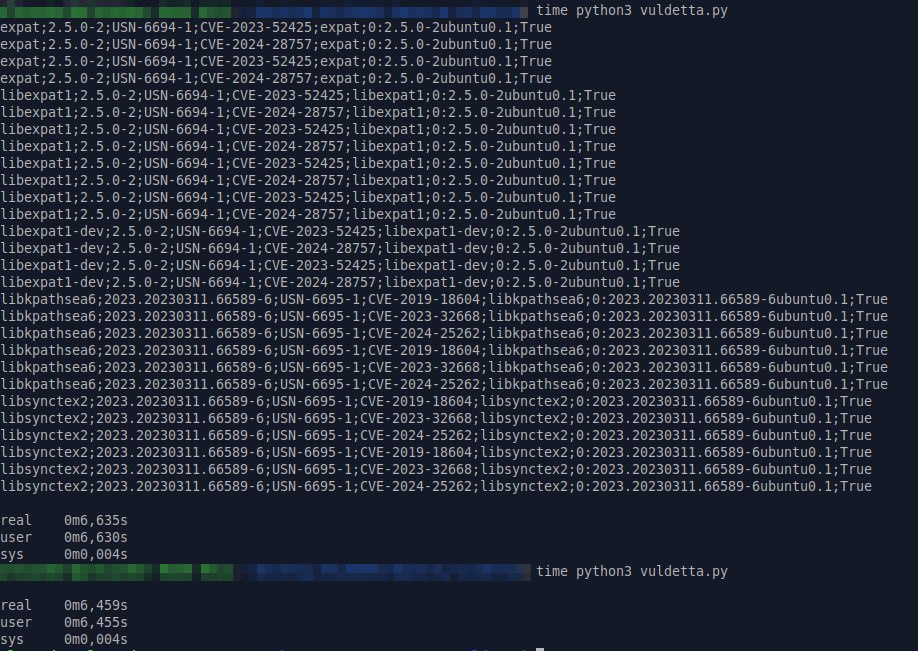
🔹 I made a primitive utility that uses these detection rules. Without any optimizations, parsing OVAL and calculating vulnerabilities takes 6.5 seconds. It works. 🙂👍
All code is available on Github. Next I will deal with kernel vulnerabilities, optimization and turn the code into an http API.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

