August episode of “In The Trend of VM”: 5 vulnerabilities in Microsoft Windows and one in WordPress. We have branched off from Seclab news videos and started releasing separate episodes. Hooray! 🥳😎 If we get enough views, we will continue to release them in the future. It’s up to you, please follow the link to the video platform and click “Like” button and/or leave a comment. 🥺
📹 Video “In The Trend of VM” on YouTube
🗞 A post on Habr (rus) a slightly expanded script of the video
🗒 A compact digest (rus) on the official PT website
List of vulnerabilities:
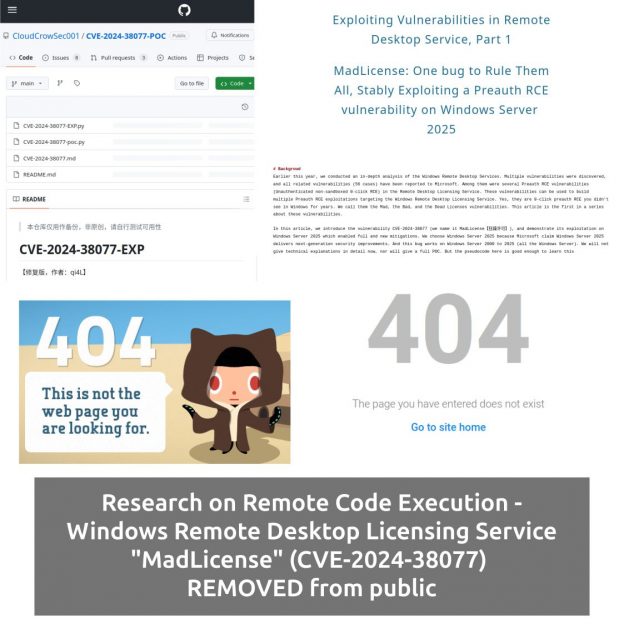
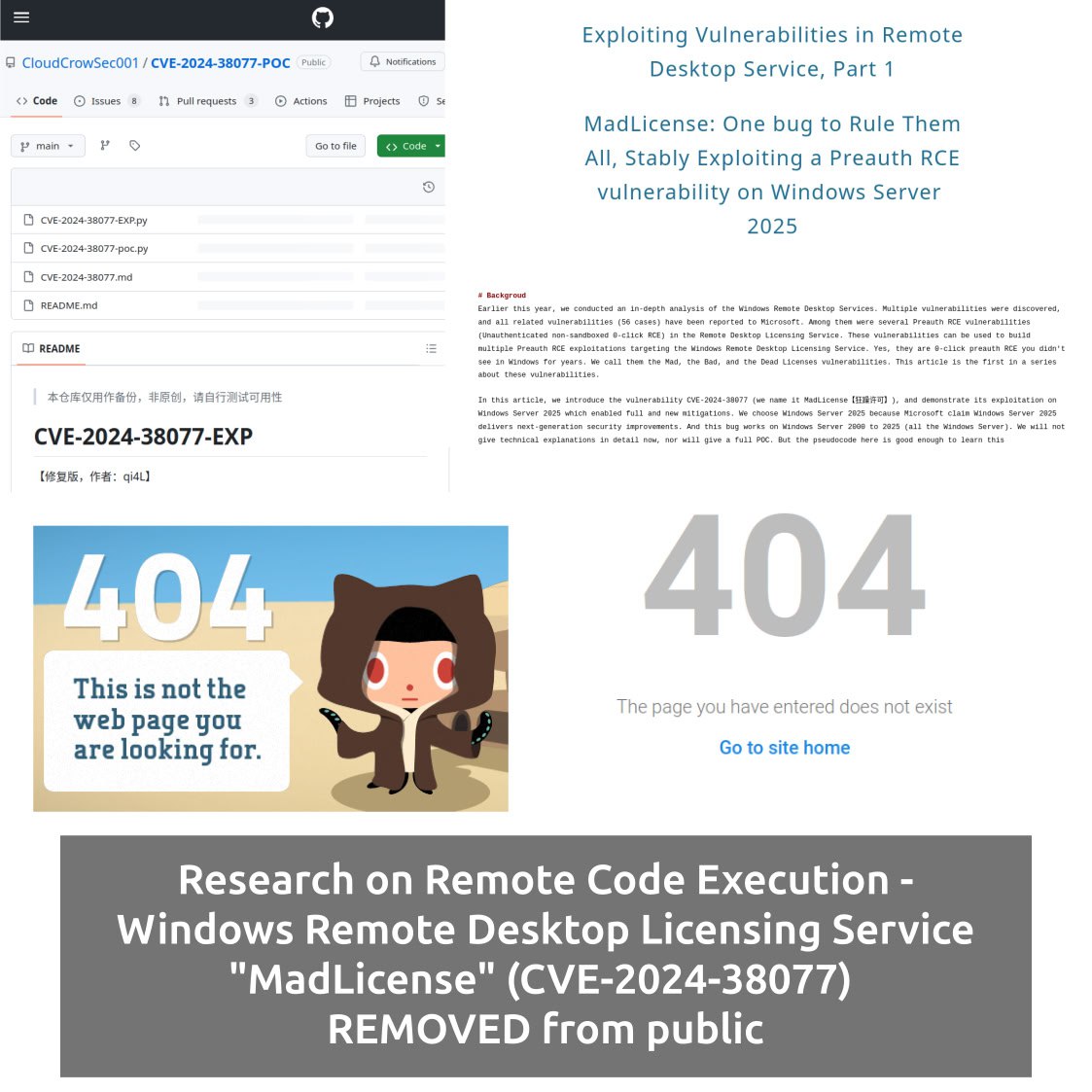
🔻 00:48 Remote Code Execution – Windows Remote Desktop Licensing Service “MadLicense” (CVE-2024-38077)
🔻 02:22 Security Feature Bypass – Windows Mark of the Web “Copy2Pwn” (CVE-2024-38213)
🔻 03:23 Elevation of Privilege – Windows Ancillary Function Driver for WinSock (CVE-2024-38193), Windows Kernel (CVE-2024-38106), Windows Power Dependency Coordinator (CVE-2024-38107)
🔻 04:50 Unauthenticated Elevation of Privilege – WordPress LiteSpeed Cache Plugin (CVE-2024-28000)
English voice over was generated by my open source utility subtivo (subtitles to voice over)
06:39 Check out the final jingle I generated using AI services 😉 (ToolBaz for lyrics and Suno for music)