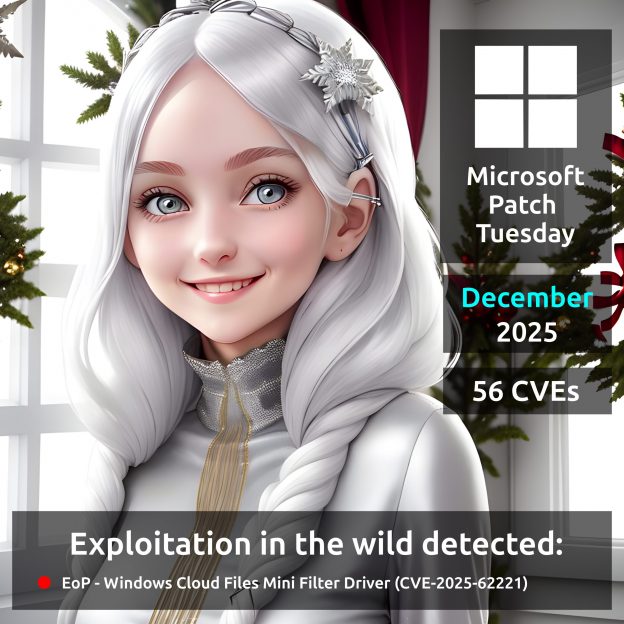
December Microsoft Patch Tuesday. A total of 56 vulnerabilities were fixed – 9 fewer than in November. There is one vulnerability with confirmed in-the-wild exploitation:
🔻 EoP – Windows Cloud Files Mini Filter Driver (CVE-2025-62221)
There are currently no vulnerabilities with publicly available exploits. Among the remaining vulnerabilities, the following stand out:
🔹 RCE – Microsoft Office (CVE-2025-62554, CVE-2025-62557), Microsoft PowerShell (CVE-2025-54100), Microsoft Outlook (CVE-2025-62562), GitHub Copilot for JetBrains (CVE-2025-64671)
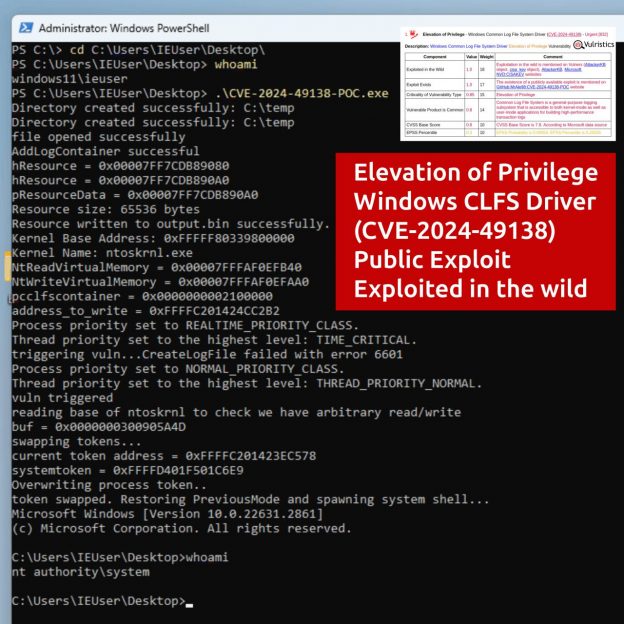
🔹 EoP – Windows Win32k (CVE-2025-62458), Windows Cloud Files Mini Filter Driver (CVE-2025-62454, CVE-2025-62457), Windows Common Log File System Driver (CVE-2025-62470), Windows Remote Access Connection Manager (CVE-2025-62472), Windows Storage (CVE-2025-59516)