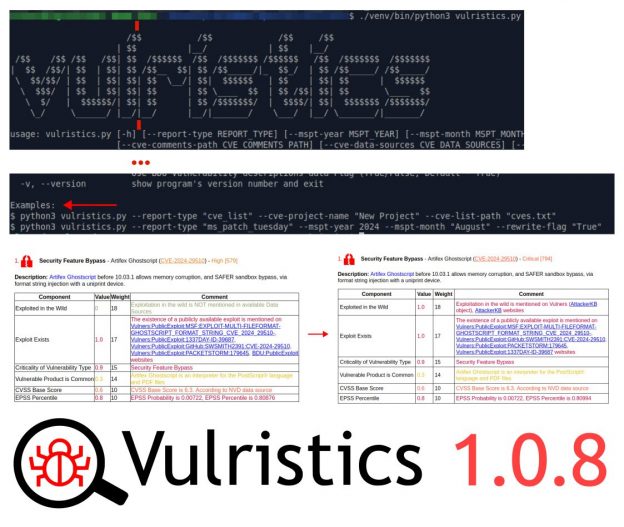
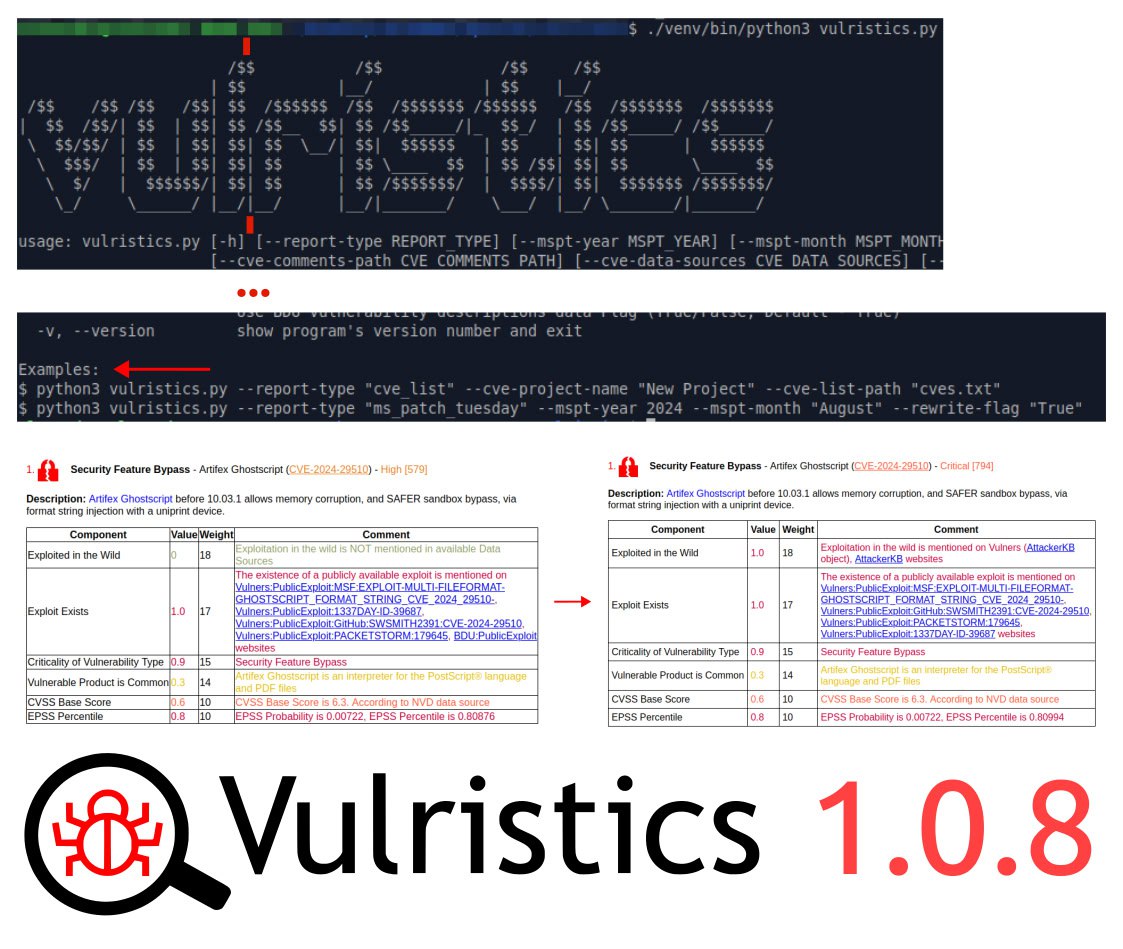
I have released a new version of Vulristics 1.0.8 with some minor usability improvements. I love it when my open source projects get pull requests. 😊 This time help came from user dvppvd:
🔹 Padding was set in the css table to make the html report more readable.
🔹 When you run the utility without parameters, help and examples are displayed. The examples show how to run the utility to analyze MSPT vulnerabilities for a specific month and year, or to analyze an arbitrary set of CVE identifiers.
🔹 Empty lines for the text banner have been added.
TODO for the next releases:
🔸 Support CVSS 4 for data sources that have already started providing this data.
🔸 Develop automated tests to verify the correct operation of the utility for known CVE identifiers.
🔸 Implement a new data source for the CVEProject GitHub repository for mass analysis of CVE vulnerabilities.
If you want to participate, join AVLEONOV Start. 😉