Have you heard about vulners.com? Vulners.com is a new search engine for security content.
Guys from vulners.com collect vendor security bulletins, lists of vulnerabilities found by researchers, content of open vulnerability and exploit databases, posts on hack forums and even detection rules from vulnerability scanners. They investigate dependencies among all this entities and provide fast and efficient searching interface. Moreover, you can even automate searching process with Vulners Search API. All for free!
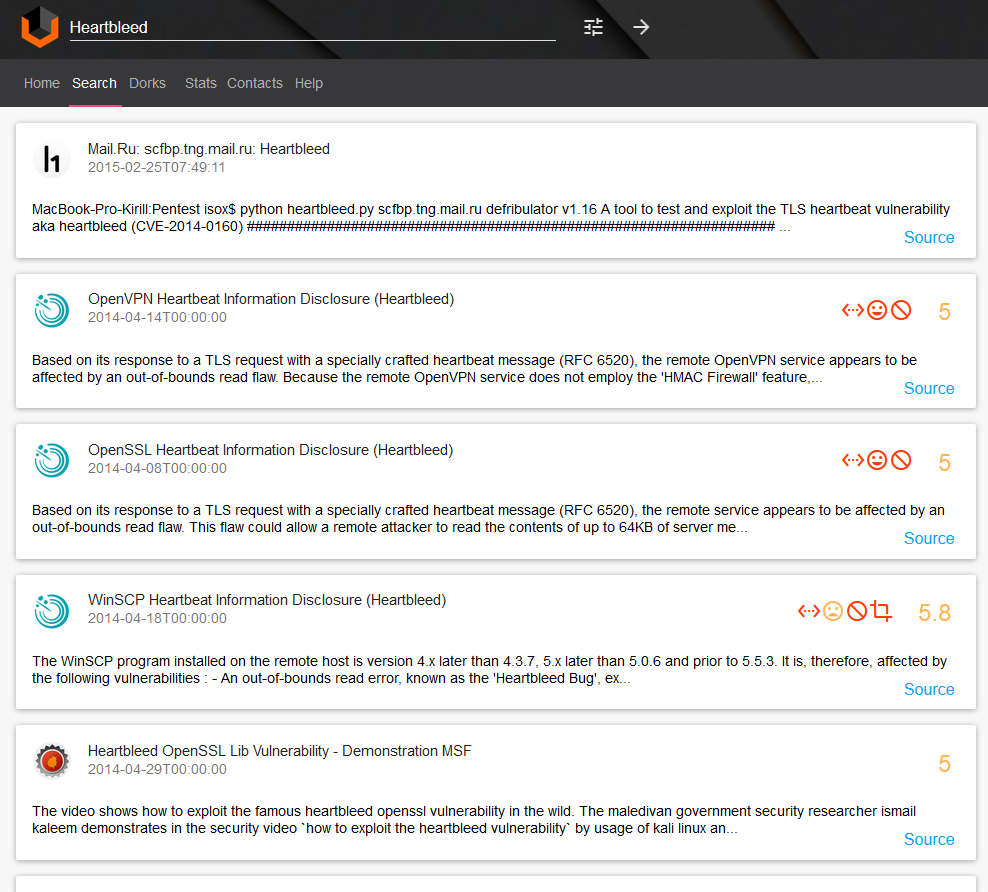
You can read Russian translation of this post on seclab. I can also recommend a great article “Vulners.com, a Shodan of vulnerability data” by Denis Gorchakov.
Why might you need it?
1. Well, obviously you can use it for searching phrases in security content,
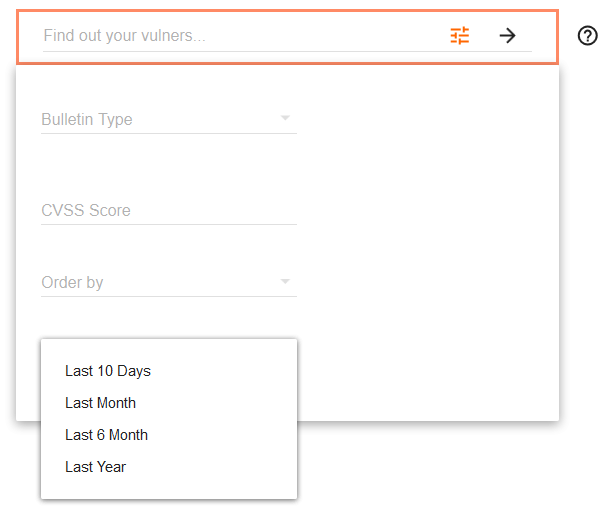
Various filters are available: bulletin type, CVSS Score, date.
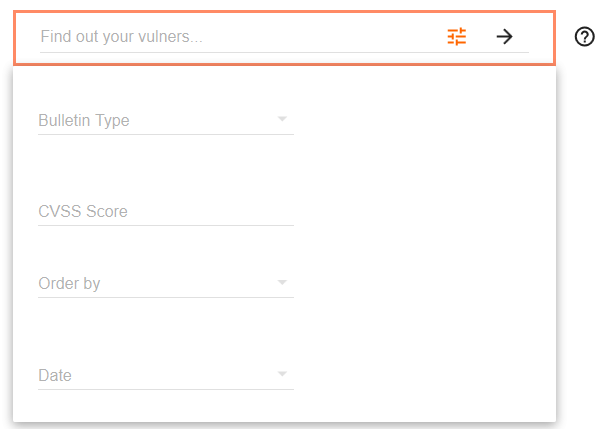
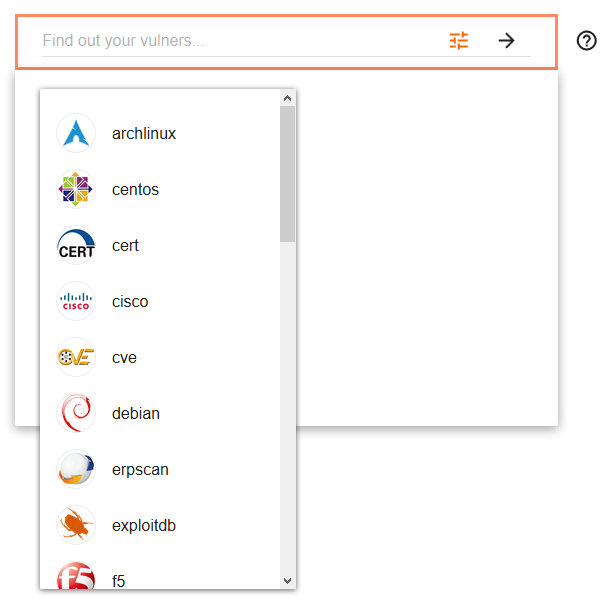
Bulletin type (27 different types):
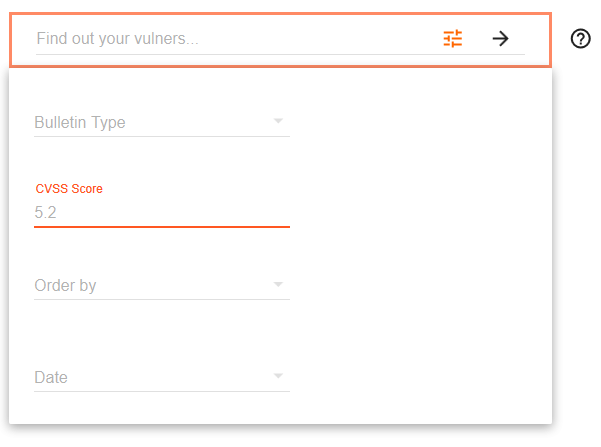
Common Vulnerability Scoring System (CVSS) Score (0-10):
You can sort results by publish date and CVSS Score:

Some more “order by” options that not described here: modified – date of modification, bounty – the size of bug bounty reward.
Date filters:
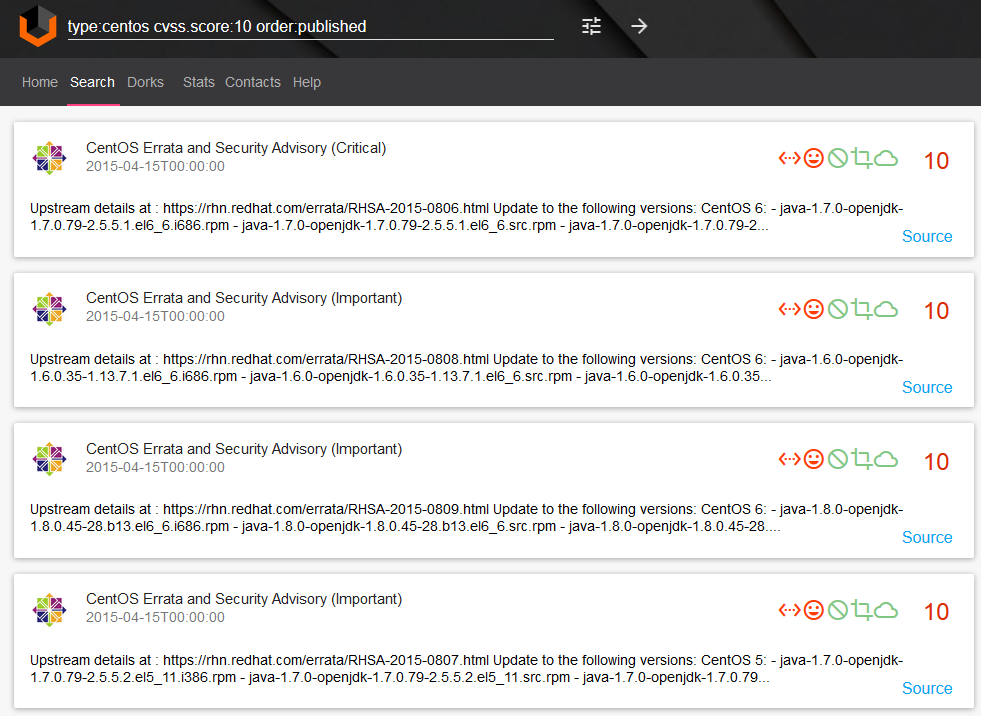
So, we can produce request “type:centos cvss.score:10 order:published” only by clicking on the filters:
2. You can use this instrument to get relevant information about particular vulnerability. On which platform it exists, how it could be exploited, how it could be patched on different platforms, what security experts are talking about this vulnerability on hack forums. And all this will be updated on regular bases fully automatically.
Searching CVEs related to Heartbleed “type:cve Heartbleed“:
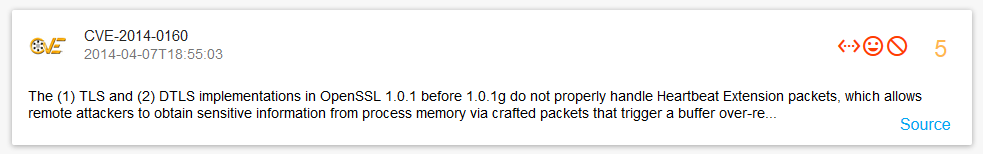
Detailed description with vulnerable software versions and links to related entities:

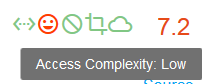
By the way, this line of icons in the upper right corner is a graphical representation of CVSS vector and base score, for example CVSS v2 Base Score 7.2 (HIGH) (AV:L/AC:L/Au:N/C:C/I:C/A:C):
3. Using vulners.com you can easily describe your IT department why vulnerabilities you found with vulnerability scanner are dangerous and should be patched. You can find exploits available for this vulnerabilities by CVE number or other IDs. Not only the fact that vulnerability is exploitable, but see full code of exploit.
Searching for exploits “CVE-2014-0160 type:exploitdb“:
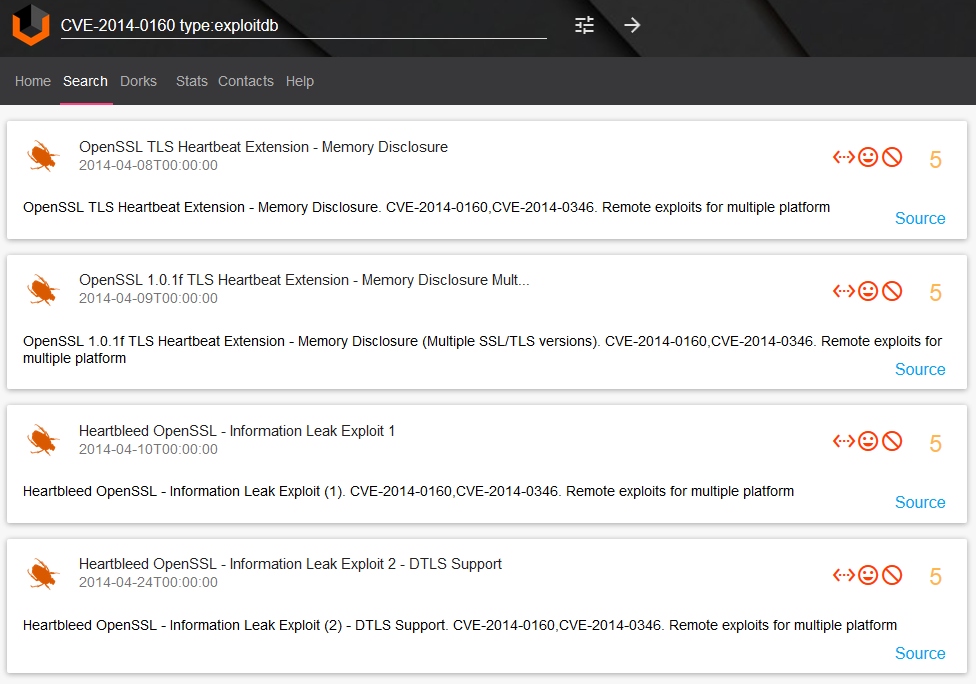
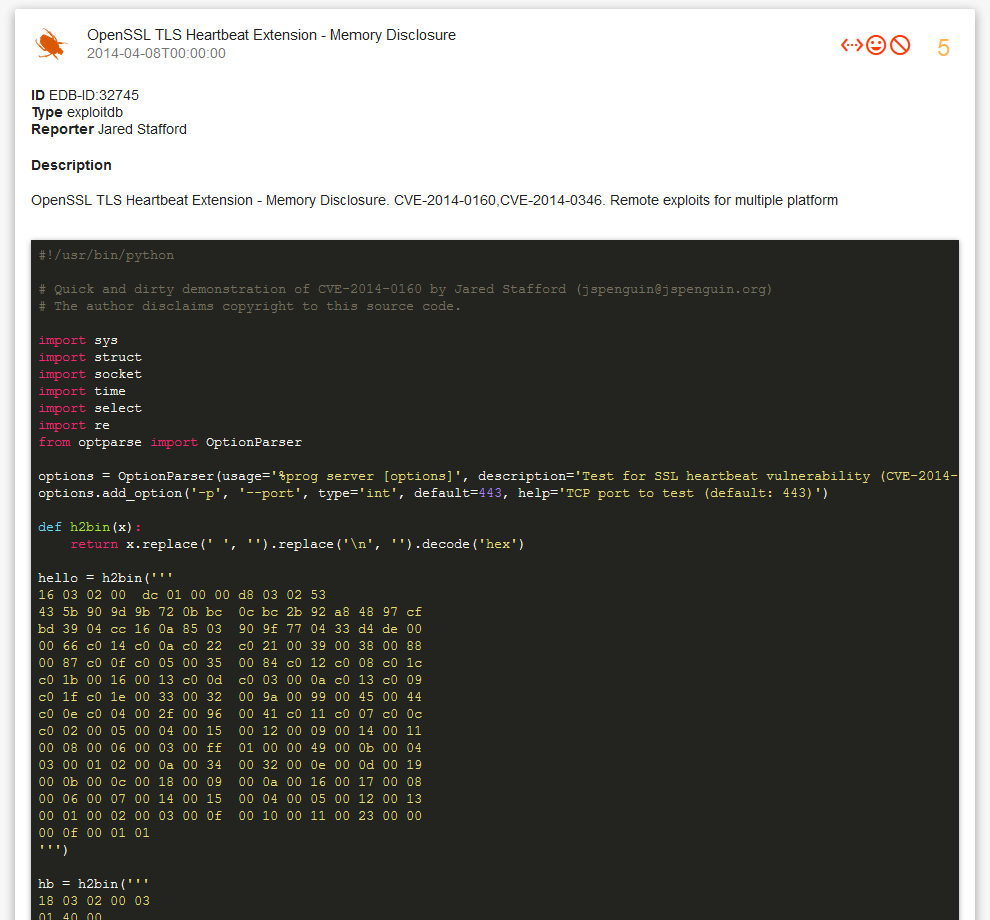
Detailed exploit description and source code:
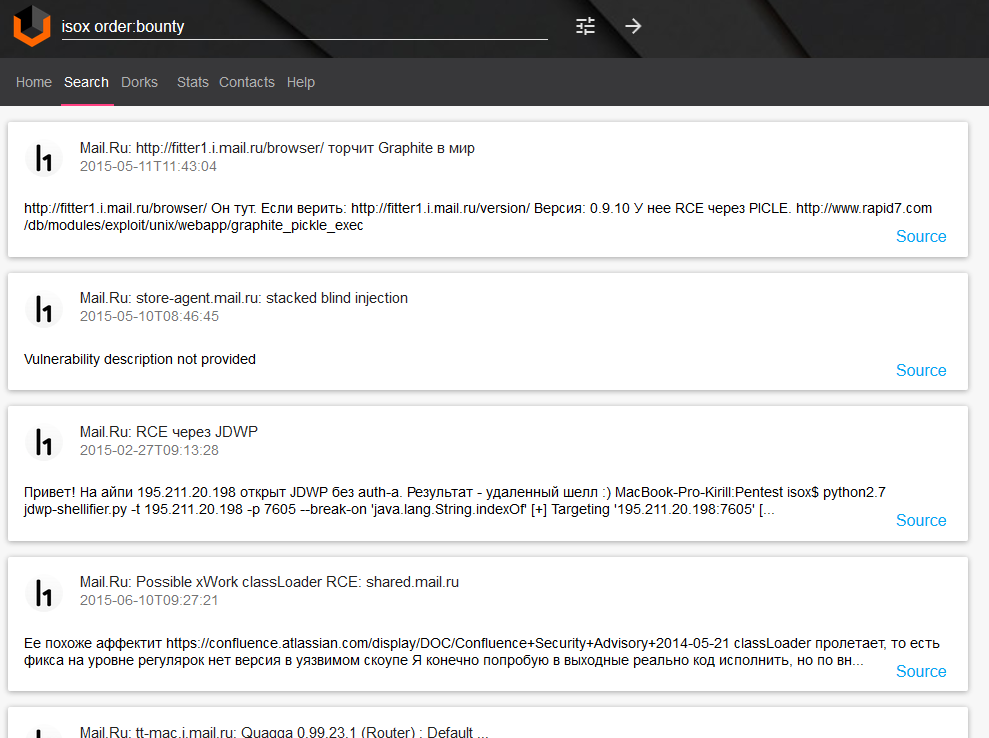
4. Maybe you are from HR and you looking for the best pentester or ethical hacker. Try to search your candidate on vulners.com. You can find what vulnerabilities he has reported and how lucky he was on bug bounty programs. And if you are that guy you can add this link to your resume by yourself 😉
Searching for person with sorting by bug bounty reward size “isox order:bounty“:
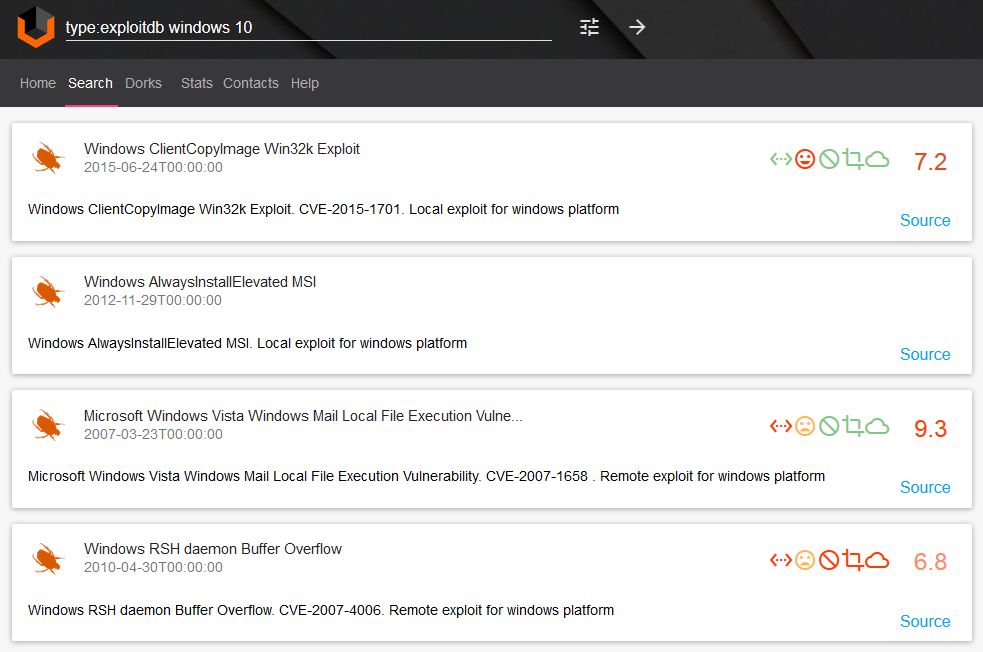
5. If you are doing pentests you can easily find exploits for the particular platform. Are you interested in examples of real SQL injections or vulnerabilities that were found, for example, on Vimeo? Easy! All to inspire you and make your job more efficient.
Windows 10 exploits “type:exploitdb windows 10“:
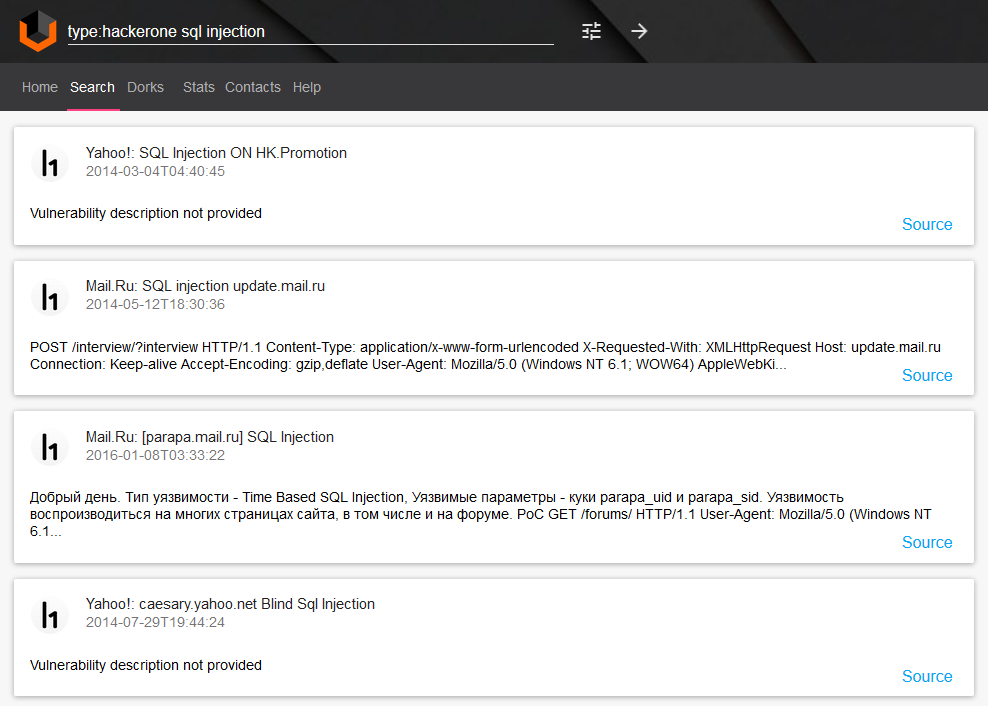
SQL injections from hackerone “type:hackerone sql injection“:
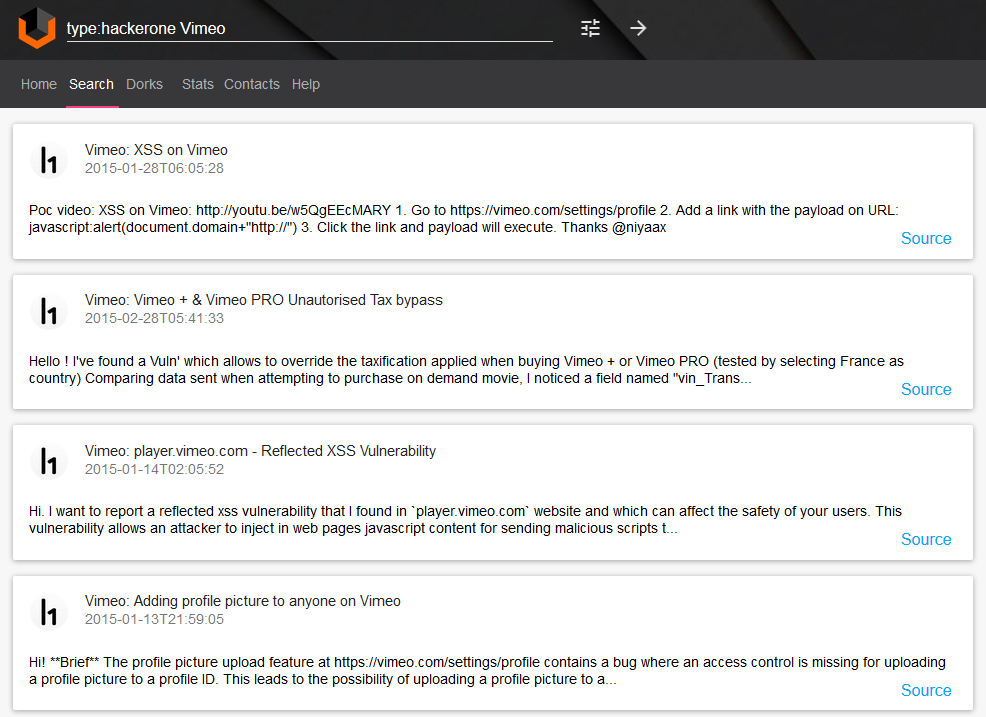
Vimeo vulnerabilities from hackerone “type:hackerone Vimeo“:
And much much more. If you know a good use case feel free to write it in comments bellow.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Vulners.com search API | Alexander V. Leonov
Pingback: PCI DSS 3.2 and Vulnerability Intelligence | Alexander V. Leonov