Remediation capabilities of Vulnerability Management products. Vulnerability scanning and vulnerability management. This terms are often used synonymously. However, most top security vendors and institutions, express an opinion, that vulnerability management is a more complex process that includes vulnerability scanning (vulnerability assessment in general), remediation and some other stages, like asset management and risk assessment.
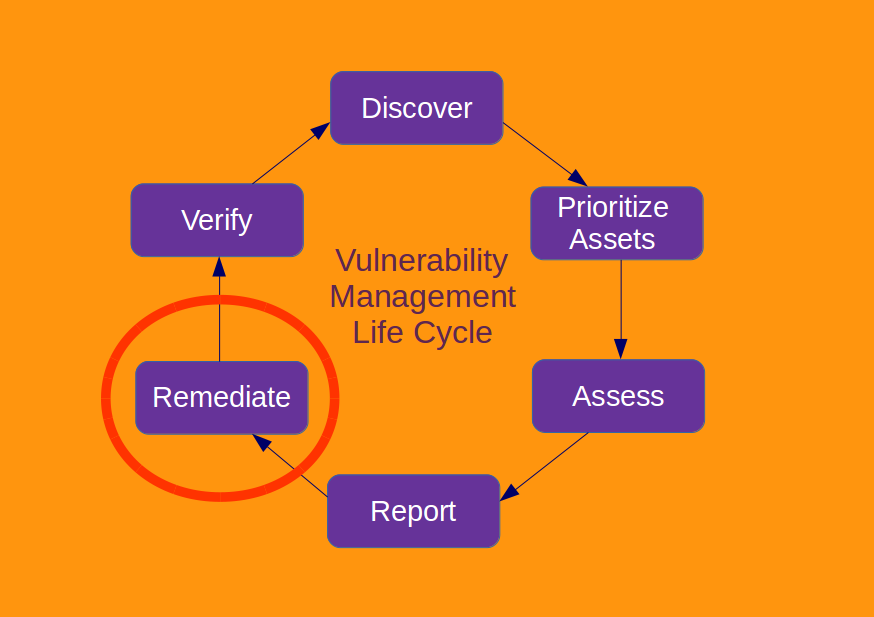
Remediation in most cases, does not mean that the vulnerability management product automatically tries to patch vulnerable system, but rather provide functionality to control remediation process. In other words, it contains a built-in task tracker, where security administrators could assign tickets (manually or automatically) on system administrators to patch or reconfigure vulnerable systems. For example, such functionality is implemented in Tenable Security Center and Qualys Cloud Suite.
NB: In most cases, but there are exceptions, as ERPScan, Secpod Saner or ConfigOS. This solutions can actually update vulnerable systems automatically.
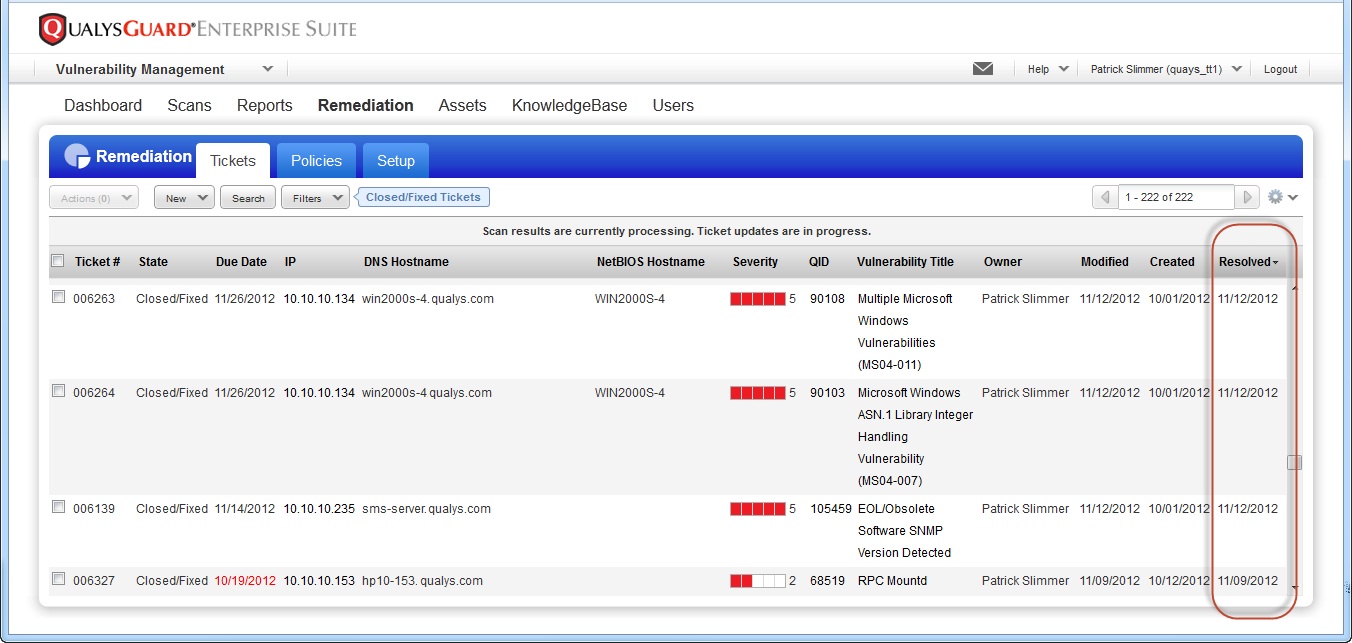
In Qualys Cloud Suite users can assign and check status of the remediation tickets. Ticket may be assigned per host or per vulnerability. Tickets can be created automatically as security scan is finished or manually by user.
Ticket updates in Qualys Cloud Suite occur automatically and resolved tickets may be automatically closed after vulnerability scan. Users may receive a daily email notification with ticket updates. Remediation behavior is configured with remediation policies. In remediation policies users can set match conditions for creation of the ticket, to whom remediation tickets will be assigned and expected ticket resolution date.
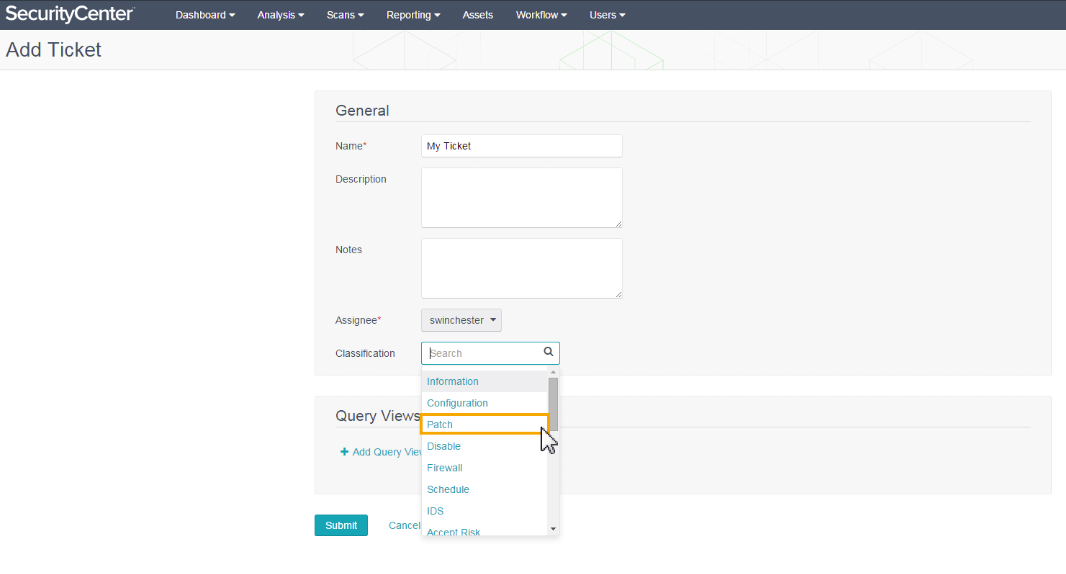
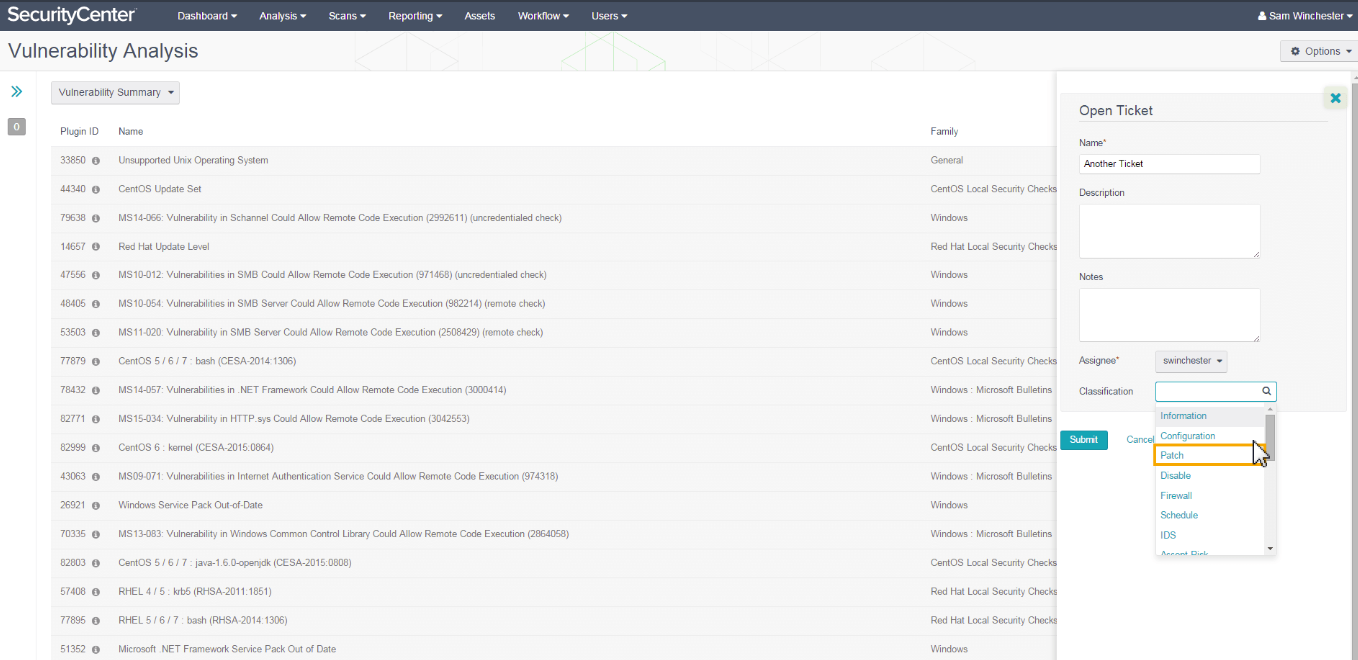
In Tenable Security Center users can create tickets manually or automatically. Ticket may be classified as one of the following issues: Information, Configuration, Patch, Disable, Firewall, Schedule, IDS, Accept Risk, Recast Risk, Re-scan Request, False positive, System Probe, External Probe, Investigation Needed, Compromised System, Virus Incident, Bad Credentials, Unauthorized Software, Unauthorized System, Unauthorized User or Other. To demonstrate the problem Query View can be added to the ticket.
Automated assignment of the tickets may be achieved with Alerts. In Action section of the Alert user should choose Assign Ticket option and then specify Name, Description and User for assignment. Ticket can be created right in Vulnerability Analysis window either.
As we see, remediation capabilities make possible to perform basic task tracking in Vulnerability Management solution. However, it often happens that the companies have already implemented other universal tool for managing tickets and when security administrations offer system administrators to use another specialized task tracker to control system patching it can cause anger and even sabotage. Therefore, even if your vulnerability management solution has remediation features, it may be reasonable to consider the integration with external task tracker.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: VM Remediation using external task tracking systems | Alexander V. Leonov
Pingback: Seccubus installation and GUI overview | Alexander V. Leonov
Pingback: А есть ли смысл в «Vulnerability Management Сycle»? | Александр В. Леонов