If you open Tenable Products page right now you will not see Nessus Manager there anymore. Nessus Manager page “The Power of Nessus for Teams” was also deleted.
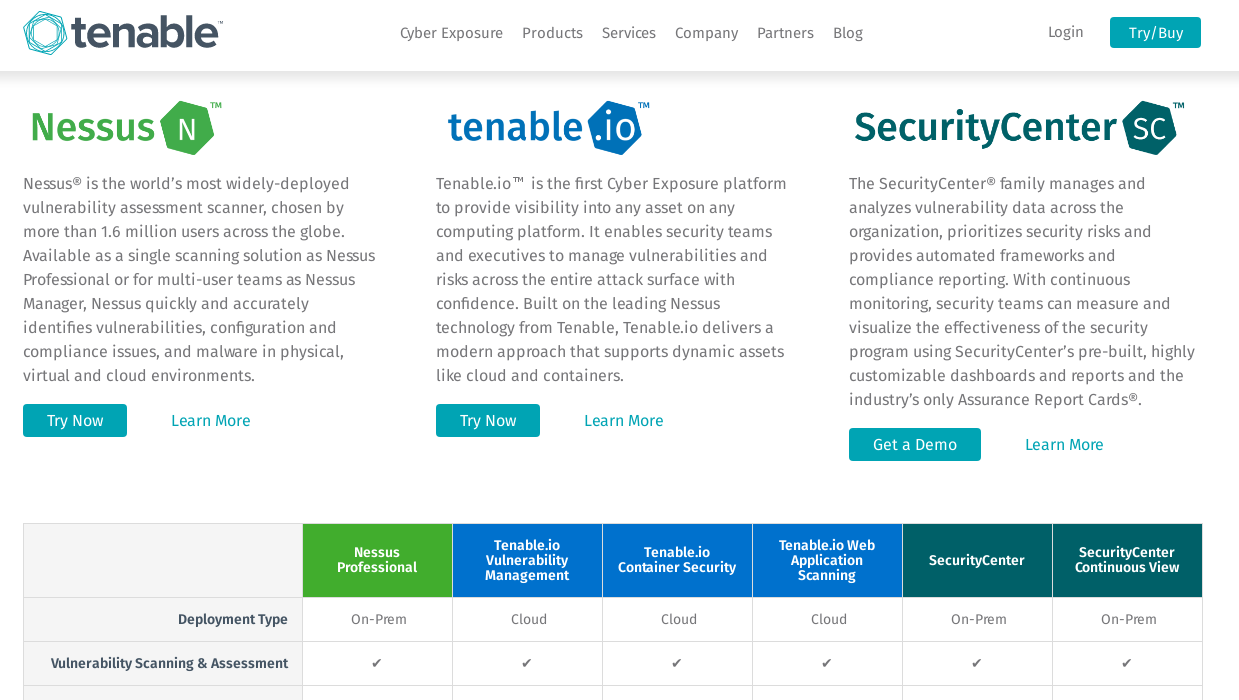
However, it is still mentioned in the product comparison. Agent-Based Scanning in SecurityCenter and SecurityCenter Continuous View “* Requires Tenable.io Vulnerability Management or Nessus Manager for agent management.”
And there is also a broken link to Nessus Manager page in the menu:
It is probably connected to announce of “Tenable.io On-Prem”, that was published last Friday. I think this new product will take a place of Nessus Manager. There are no technical details for the moment. As you can see, in comparison table “Tenable.io Vulnerability Management” is marked only as Cloud.
In the announce it is said that on-prem version “provides the majority of capabilities offered by the cloud-based Tenable.io and a similar user experience, although some capabilities will only be offered in the cloud version.” It’s pretty intriguing what this features will be available only in cloud version.
Tenable.io On-Prem will for sure support:
- Nessus sensors active scanning
- Nessus sensors for agent-based scanning
- Nessus sensors for passive network monitoring (ex-PVS)
- API/SDK
In the datasheet it is also mentioned that Tenable.io On-Prem will have “elastic asset licensing model”. Somebody was waiting for unlimited scanner with API in exchange for a highly limited Nessus Proffessional 7? Not this case. 😉
I don’t wait for sensation, but it will interesting to see the list of features that will be available only in Cloud version of Tenable.io and prices.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

I have a question about using Token value to get the scan information:
If you use cloud version, you need to get the session token from the tenable IO. and then use that token for various services such as scan list, policy list etc.
Don’t you think its an insecure process to use as problems such as “Session Hijacking” could occur with such information in the plaintext?
Example:
curl -s -k -X GET -H “X-Cookie: token=8bXXXXXXXXXXXXXXXXXXXXXXXXXXXXX025” https://cloud.tenable.com/scans | python -m json.tool
What could be the solution for such situations?
Alexander,
And about Nessus Manager?
I subscribe, in 18′ January a lot of licences, and the API to extract results are the bigger winpoint to me. I received today a “alert” to update my Manager to v7, but, when I read the documentation, only founf about APIs on Nessus Professional. I’m afraid thinking if I wish or not update my Nessus Manager :/
Hi Rafael! I don’t know. It seems that there won’t be Nessus Manager anymore. I am curious in how your Nessus Manager will look like after the update. I supposed earlier Tenable could update Nessus Managers to Tenable.io on-prem. But from your words it seems like they will keep Nessus Manager till the expiration of existing licences.
In the User GUide of Nessus v7:
“Nessus Manager is no longer sold as of February 1, 2018. For existing customers, service will continue to be provided through the duration of your contract. For prospective customers, please consider Tenable.io for your vulnerability management needs.”
Thanks God if Tenable don’t stop to permit Vuln database update for manager