Non-reliable Nessus scan results. Do you perform massive unauthenticated vulnerability scans with Nessus? It might be a bad idea. It seems that Nessus is not reliable enough to assess hundreds and thousands of hosts in one scan and can lose some valuable information.
The thing is that sometimes Nessus does not detect open ports and services correctly. And without successful service detection it will not launch other vulnerability detection plugins (see Nessus Scan stages in my post about Tenable University ). Scan results for the host will be empty, however in reality it may have some critical vulnerabilities, that you simply will not see!
Upd. When you use Nessus inside your corporate network only, it might not be issue for you. But if you deploy Nessus on some remote hosting to perform regular perimeter scans, emulating attacker’s actions, it’s quite a possibility that you will face such kind of errors. Especially if Nessus and scan targets are placed in different geograpfical locations and it takes many hops for Nessus to reach each target. If you use load balancers in your organisation to increase capacity and reliability of applications, this can also lead to errors.
Anyway, it’s good to know when Nessus was not able to detect services on some hosts and you should not relly on these scan results. Let’s see how we can figure this out.
So, I have one vulnerability scan task for 130 hosts. The scanning lasts 6-7 hours. I see a regular problem: Nessus does not make all the checks for some hosts.
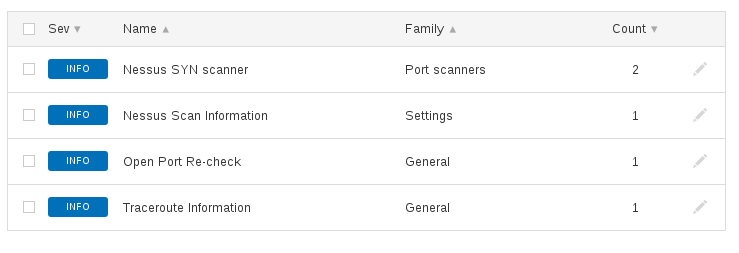
For example, during the mass scan Nessus successfully detects open ports (“Nessus SYN scanner”, 11219), but does not detect the services (“Service Detection”, 22964):
When I created a task with the same policy for only one of such hosts, all the checks performed successfully.
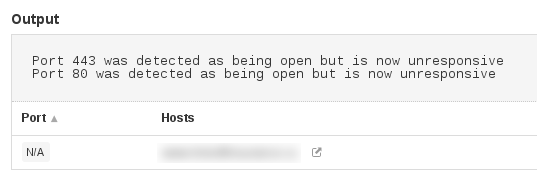
In this case note the plugin “Open Port Re-check” (10919). The output of this plugin contains information that some port was detected as being open initially but was found unresponsive later:
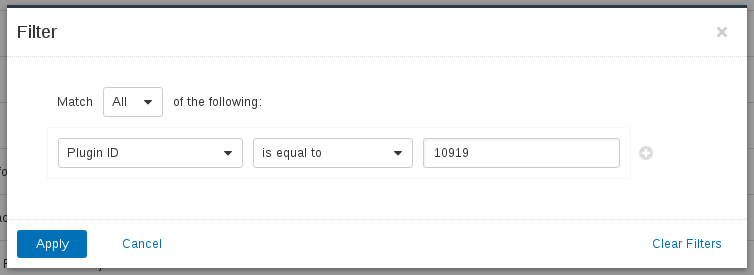
You can find this plugin in Nessus GUI using this Vulnerability filter:
What can be the reason:
- Scan may have caused a service to freeze or stop running. Something like a DoS attack.
- Particular service was stopped during the scanning process or host was switched off.
- Scanner was blocked by IDS/IPS.
- Remote network cannot be reached anymore by the scanner.
Well, if you make a task for only one of host and get complete results the reason is pretty obvious – timeouts during the port and service detection. You can increase the timeout settings at “Scan Policy -> Settings -> Advanced -> Performance Options”:
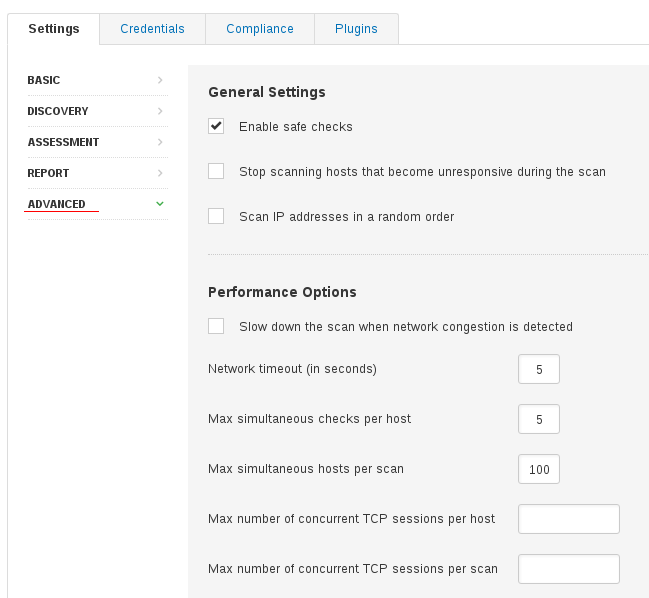
Note these parameters:
- Network timeout (in seconds)
- Max simultaneous checks per host
- Max simultaneous hosts per scan
Tenable Support recommends to set “Network timeout” 10 at first, if it still doesn’t work try 15, 20 etc. You can try to reduce the Max simultaneous checks per host found in the same location.
Setting the timeout parameters helped me partially. The total number of hosts with unreliable results has decreased by half. However, the scan took two times more time as well. So, It seems more efficient to scan hosts with errors in separate tasks, after the main mass scan will be finished.
But what to do in situation when Nessus detects services, but not all the services? For example, if Nessus detected web-server at 80 tcp, but didn’t detect it at 443 tcp (even if, this port was detected as open). Nessus doesn’t give information about these issues. In this case it may be useful to make port scan and service detection with other tools (for example nmap) and compare results with Nessus.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

You are using Nessus in a way it was not intended . . . you will have built a much better user experience in Tenable.io.
But I am sure you knew that having heard it before 🙂
It is the same situation with Tenable.io. Moreover, there are bugs in policies (scans created several years ago do not receive updates) that Tenable Support cannot debug.
On a serious note, I am investigating a similar problem, but it appears to be worse than you suggest.
Authenticated scans may be affected on an internal network.
As for changing timeouts and scanning a few affected hosts at a time – this is the sort of thing one would normally use the API to achieve . . . at least in the past.
Nessus is rapidly becoming not fit for purpose.
Pingback: Dealing with Nessus logs | Alexander V. Leonov
Pingback: Asset Inventory for Network Perimeter: from Declarations to Active Scanning | Alexander V. Leonov