This will be my third Microsoft Patch Tuesday report in video and audio format. And for the third time in a row, Microsoft has addressed over a hundred vulnerabilities. With my Microsoft Patch Tuesday parser, it was possible to generate a report almost on the same day. But, of course, it takes much more time to describe the vulnerabilities manually.
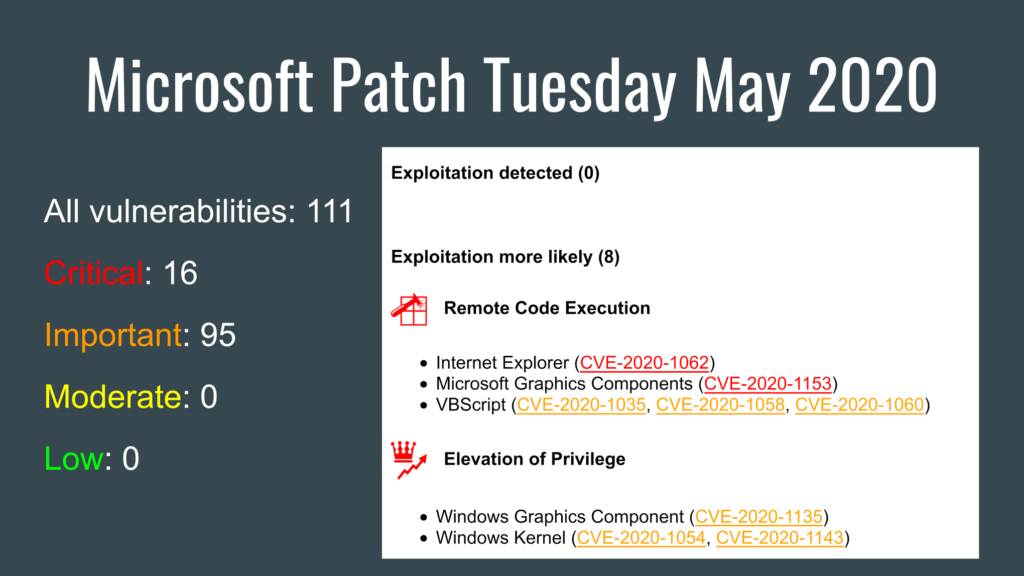
- All vulnerabilities: 111
- Critical: 16
- Important: 95
- Moderate: 0
- Low: 0
Last time I complained that different VM vendors release completely different reports for Microsoft Patch Tuesday. This time I decided that it’s not a bug, but a feature. I upgraded my script to not only show vulnerabilities, but also show how these vulnerabilities were mentioned in the reports of various VM vendors (Tenable, Qualys, Rapid7 and ZDI). In my opinion, it seems pretty useful.
Exploitation detected (0)
In the old report, we can see that there are no vulnerabilities actively used in attacks.
Exploitation more likely (8)
There are 8 vulnerabilities that MS considers more likely to be exploited. We see the types of these vulnerabilities and what products they affect. But all other details should be googled.
 Remote Code Execution
Remote Code Execution
- Internet Explorer (CVE-2020-1062)
- Microsoft Graphics Components (CVE-2020-1153)
- VBScript (CVE-2020-1035, CVE-2020-1058, CVE-2020-1060)
 Elevation of Privilege
Elevation of Privilege
- Windows Graphics Component (CVE-2020-1135)
- Windows Kernel (CVE-2020-1054, CVE-2020-1143)
And here my script adds comments about vulnerabilities from the vendors and highlights vulnerabilities that were mentioned (or not mentioned).
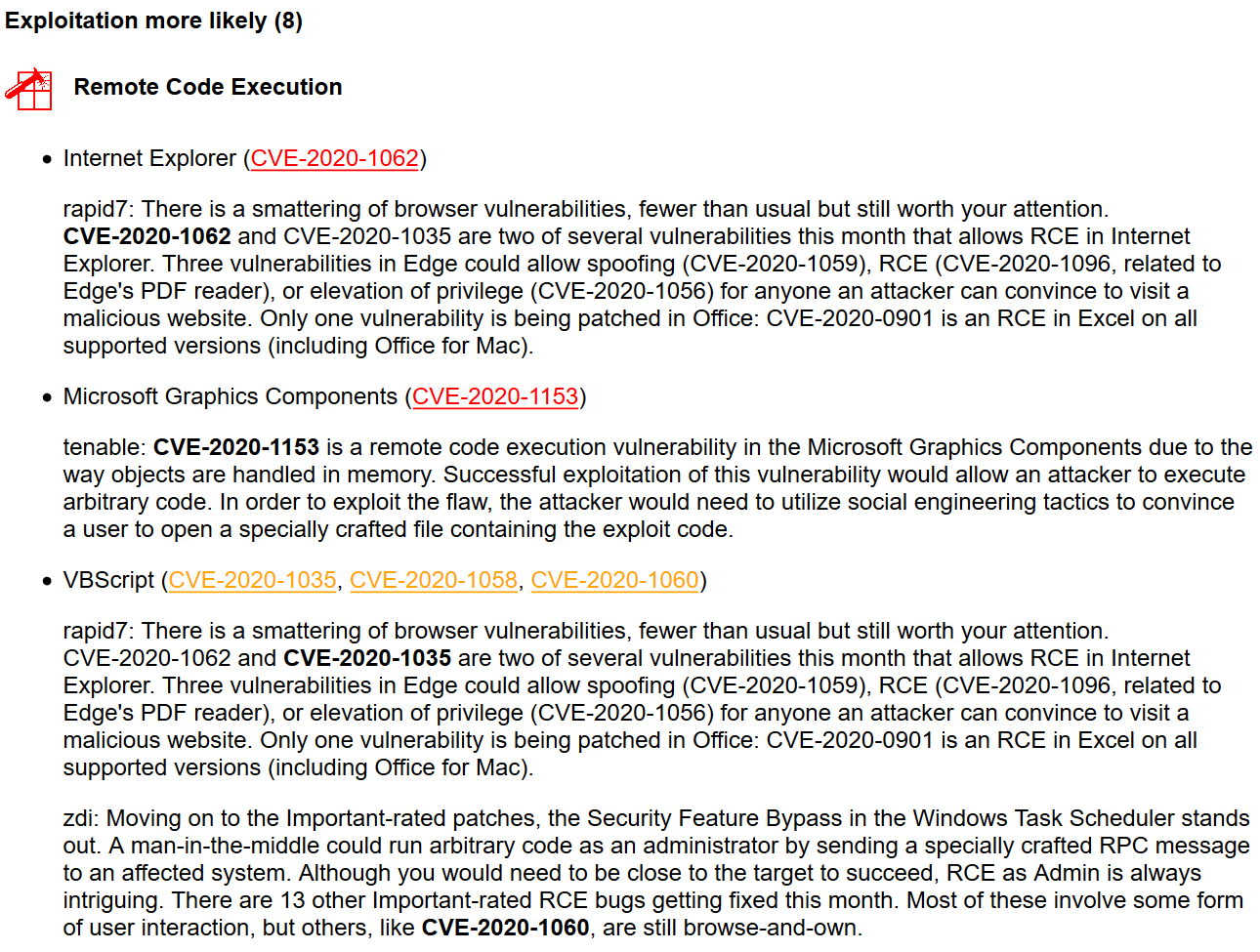
We can see right away that Rapid7 recommends paying attention to RCE in Internet Explorer (CVE-2020-1062), although other vendors ignore this vulnerability.
According to W3Counter, the current IE11 share is only 1.75%. But, on the other hand, it can still be used in some organizations to access legacy systems. And so this vulnerability may be exploited in targeted attacks.
Tenable pays attention to RCE in Microsoft Graphics Components. “The attacker would need to utilize social engineering tactics to convince a user to open a specially crafted file”. Finally, ZDI claims that VBScript RCE (CVE-2020-1060) is especially interesting because “does’t involve some form of user interaction”.
Agree that looking at Microsoft Patch Tuesday vulnerabilities in this way is much more fun. 🙂
Regarding the Elevation of Privilege, ZDI claims that Windows Graphics Component EoP (CVE-2020-1135) is a real exploitable thing. Tenable mentions vulnerabilities of this type in Windows Kernel (CVE-2020-1054, CVE-2020-1143).
These were all “more likely to be exploited” vulnerabilities, according to Microsoft.
Other Product based (36)
What about other vulnerabilities? Let’s see the large groups of vulnerabilities in the same product. Strictly speaking, there is only one product, Microsoft SharePoint, with a bunch of different vulnerabilities. The rest are EoPs in Windows components that no VM vendor mentions.
Microsoft SharePoint
 Remote Code Execution (CVE-2020-1023, CVE-2020-1024, CVE-2020-1102, CVE-2020-1069)
Remote Code Execution (CVE-2020-1023, CVE-2020-1024, CVE-2020-1102, CVE-2020-1069) Information Disclosure (CVE-2020-1103)
Information Disclosure (CVE-2020-1103) Cross Site Scripting (CVE-2020-1099, CVE-2020-1100, CVE-2020-1101, CVE-2020-1106)
Cross Site Scripting (CVE-2020-1099, CVE-2020-1100, CVE-2020-1101, CVE-2020-1106) Spoofing (CVE-2020-1104, CVE-2020-1105, CVE-2020-1107)
Spoofing (CVE-2020-1104, CVE-2020-1105, CVE-2020-1107)
Windows Runtime
 Elevation of Privilege (CVE-2020-1077, CVE-2020-1086, CVE-2020-1090, CVE-2020-1125, CVE-2020-1139, CVE-2020-1149, CVE-2020-1151, CVE-2020-1155, CVE-2020-1156, CVE-2020-1157, CVE-2020-1158, CVE-2020-1164)
Elevation of Privilege (CVE-2020-1077, CVE-2020-1086, CVE-2020-1090, CVE-2020-1125, CVE-2020-1139, CVE-2020-1149, CVE-2020-1151, CVE-2020-1155, CVE-2020-1156, CVE-2020-1157, CVE-2020-1158, CVE-2020-1164)
Windows State Repository Service
 Elevation of Privilege (CVE-2020-1124, CVE-2020-1131, CVE-2020-1134, CVE-2020-1144, CVE-2020-1184, CVE-2020-1185, CVE-2020-1186, CVE-2020-1187, CVE-2020-1188, CVE-2020-1189, CVE-2020-1190, CVE-2020-1191)
Elevation of Privilege (CVE-2020-1124, CVE-2020-1131, CVE-2020-1134, CVE-2020-1144, CVE-2020-1184, CVE-2020-1185, CVE-2020-1186, CVE-2020-1187, CVE-2020-1188, CVE-2020-1189, CVE-2020-1190, CVE-2020-1191)
But they write a lot about SharePoint, especially about RCEs (CVE-2020-1023, CVE-2020-1024, CVE-2020-1069, CVE-2020-1102). Three of the four RCEs involve uploading a malicious application package to exploit the vulnerabilities, while the other involves uploading a malicious page. In short, if you use SharePoint in your organization, you need to patch again.
Other Vulnerability Type based (67)
And what about the remaining vulnerabilities in various products. Of course, the RCEs that can be used in phishing attacks are most interesting. These are vulnerabilities in Microsoft Color Management (CVE-2020-1117), Edge PDF (CVE-2020-1096) and Excel (CVE-2020-0901).
Vendors paid a lot of attention to RCEs in Visual Studio Code Python Extension (CVE-2020-1171, CVE-2020-1192). But IMHO this is just a funny case. It is unlikely that attacks that require opening a specially crafted file or a repository with malicious code in Visual Studio Code will be massive.
It is also worth noting the RCE vulnerability in Windows (CVE-2020-1067). ZDI guys write that: “the only thing keeping this from being Critical is the fact that the attacker needs a domain user account for their specially crafted request to succeed. This makes the bug a prime target for insider threats, as well as penetration testers looking to expand their foothold in a target enterprise.”
 Remote Code Execution
Remote Code Execution
- Chakra Scripting Engine (CVE-2020-1037, CVE-2020-1065)
- Internet Explorer (CVE-2020-1092)
- Jet Database Engine (CVE-2020-1051, CVE-2020-1174, CVE-2020-1175, CVE-2020-1176)
- MSHTML Engine (CVE-2020-1064)
- Microsoft Color Management (CVE-2020-1117)
- Microsoft Edge PDF (CVE-2020-1096)
- Microsoft Excel (CVE-2020-0901)
- Microsoft Script Runtime (CVE-2020-1061)
- VBScript (CVE-2020-1093)
- Visual Studio Code Python Extension (CVE-2020-1171, CVE-2020-1192)
- Windows (CVE-2020-1067)
 Denial of Service
Denial of Service
- .NET Core & .NET Framework (CVE-2020-1108)
- ASP.NET Core (CVE-2020-1161)
- Connected User Experiences and Telemetry Service (CVE-2020-1084, CVE-2020-1123)
- Microsoft Windows Transport Layer Security (CVE-2020-1118)
- Windows (CVE-2020-1076)
- Windows Hyper-V (CVE-2020-0909)
 Memory Corruption
Memory Corruption
- Media Foundation (CVE-2020-1150, CVE-2020-1028, CVE-2020-1126, CVE-2020-1136)
 Elevation of Privilege
Elevation of Privilege
- .NET Framework (CVE-2020-1066)
- DirectX (CVE-2020-1140)
- Microsoft Edge (CVE-2020-1056)
- Microsoft Windows (CVE-2020-1010, CVE-2020-1068, CVE-2020-1079)
- Windows Background Intelligent Transfer Service (CVE-2020-1112)
- Windows Clipboard Service (CVE-2020-1111, CVE-2020-1121, CVE-2020-1165, CVE-2020-1166)
- Windows Common Log File System Driver (CVE-2020-1154)
- Windows Error Reporting (CVE-2020-1021, CVE-2020-1082, CVE-2020-1088)
- Windows Error Reporting Manager (CVE-2020-1132)
- Windows GDI (CVE-2020-1142)
- Windows Installer (CVE-2020-1078)
- Windows Kernel (CVE-2020-1087, CVE-2020-1114)
- Windows Print Spooler (CVE-2020-1048, CVE-2020-1070)
- Windows Printer Service (CVE-2020-1081)
- Windows Push Notification Service (CVE-2020-1137)
- Windows Remote Access Common Dialog (CVE-2020-1071)
- Windows Storage Service (CVE-2020-1138)
- Windows Update Stack (CVE-2020-1109, CVE-2020-1110)
 Security Feature Bypass
Security Feature Bypass
- Windows Task Scheduler (CVE-2020-1113)
 Information Disclosure
Information Disclosure
- Windows CSRSS (CVE-2020-1116)
- Windows GDI (CVE-2020-0963, CVE-2020-1141, CVE-2020-1145, CVE-2020-1179)
- Windows Kernel (CVE-2020-1072)
- Windows Subsystem for Linux (CVE-2020-1075)
 Cross Site Scripting
Cross Site Scripting
- Microsoft Active Directory Federation Services (CVE-2020-1055)
- Microsoft Dynamics 365 (On-Premise) (CVE-2020-1063)
 Spoofing
Spoofing
- Microsoft Edge (CVE-2020-1059)
- Microsoft Power BI Report Server (CVE-2020-1173)
Among DoS vulnerabilities, the most promising is DoS in TLS (CVE-2020-1118). An attacker sends a malicious Client Key Exchange message to TLS client or server during a handshake. This flaw can cause the target system to stop responding or automatically reboot.
Memory Corruption in Media Foundation (CVE-2020-1150, CVE-2020-1028, CVE-2020-1126, CVE-2020-1136) is in fact RCE that can allow full system access to an attacker.
Among many Elevation of Privilege vulnerabilities, vendors pay attention to the EoP in Microsoft Edge (CVE-2020-1056) and Windows Remote Access Common Dialog (CVE-2020-1071). Among other vulnerabilities, they mentionт Cross Site Scripting in Microsoft Active Directory Federation Services (CVE-2020-1055) and Spoofing in Microsoft Edge (CVE-2020-1059).
That’s all for the May Microsoft Patch Tuesday vulnerabilities.
Older vulnerabilities
- The PoC for previous month RCE in Microsoft SharePoint (CVE-2020-0932) was demonstrated by ZDI. “You can download all the necessary files to try this yourself.”
- Windows SMBv3 Client/Server Remote Code Execution Vulnerability (CVE-2020-0796) now has POC by Ricerca Security. The code is still not available.
- And nothing new for .LNK files processing (CVE-2020-0684) and Mysterious Windows RCE (CVE-2020-0662) from February.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
