This time I want to write about the service of my friends from Antiphish. They call it “security awareness and employee behaviour management platform”. Simply put, they teach company employees how to detect and avoid phishing attacks.
By the way, they are great guys, made a demo for me, prepared custom templates, like in real PoC for a corporate client. Thanks so much for the excellent work!
The main idea
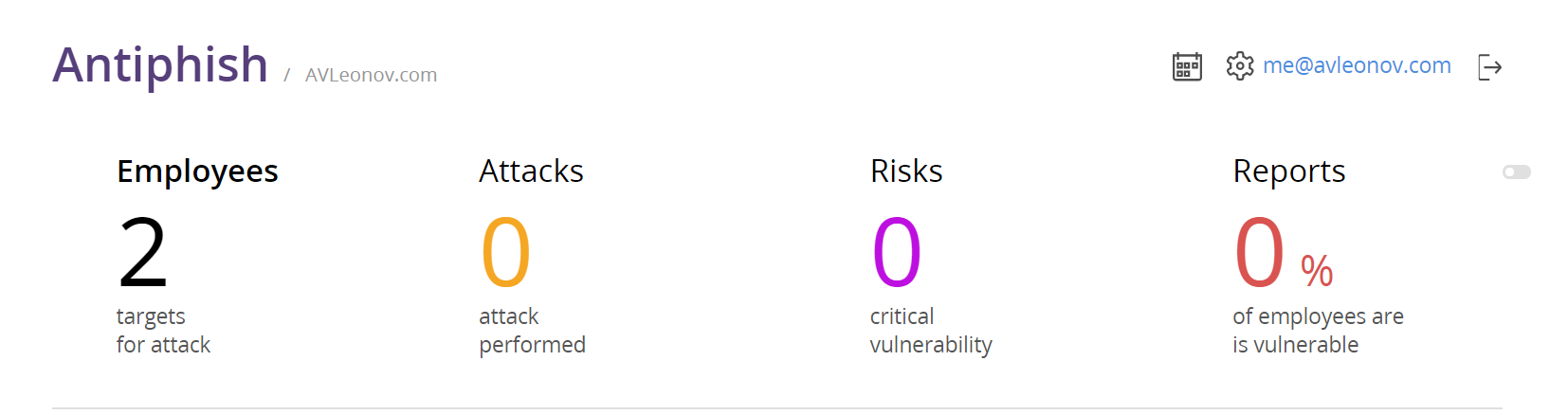
When you sign in to the Antiphish interface, you see the dashboards with information about the people who studied security courses, were tested during the course and were checked using emulated phishing attacks (some of these attacks are amazing, and I’ll show them at the end). This is the main idea. How can you protect your organization from phishing attacks? Educate people and constantly provoke them. Not just to send an email and see the employees who visited your “malicious” website. No, there should be a process!
I will not describe the educational part here. You can get some ideas from the free “How to Work From Home and Stay Safe” guide. If you have to conduct Security Awareness Training for your organization’s employees (for ordinary people, not security professionals!), this can be a good basis. There are ten short videos beautifully dubbed and the main points for them.
Also, I will not describe the methodology: why phishing email messages work, how often you should send them to your employees, and how to respond to their failures. Believe me, Antiphish has described and formalized all this.
Basic attacks
Let’s go straight to actual attacks. Antiphish team made several attack patterns for me: invitation to security conference and Vulnerability Management meetup, an urgent email message from the HR department and notification from an insurance company.
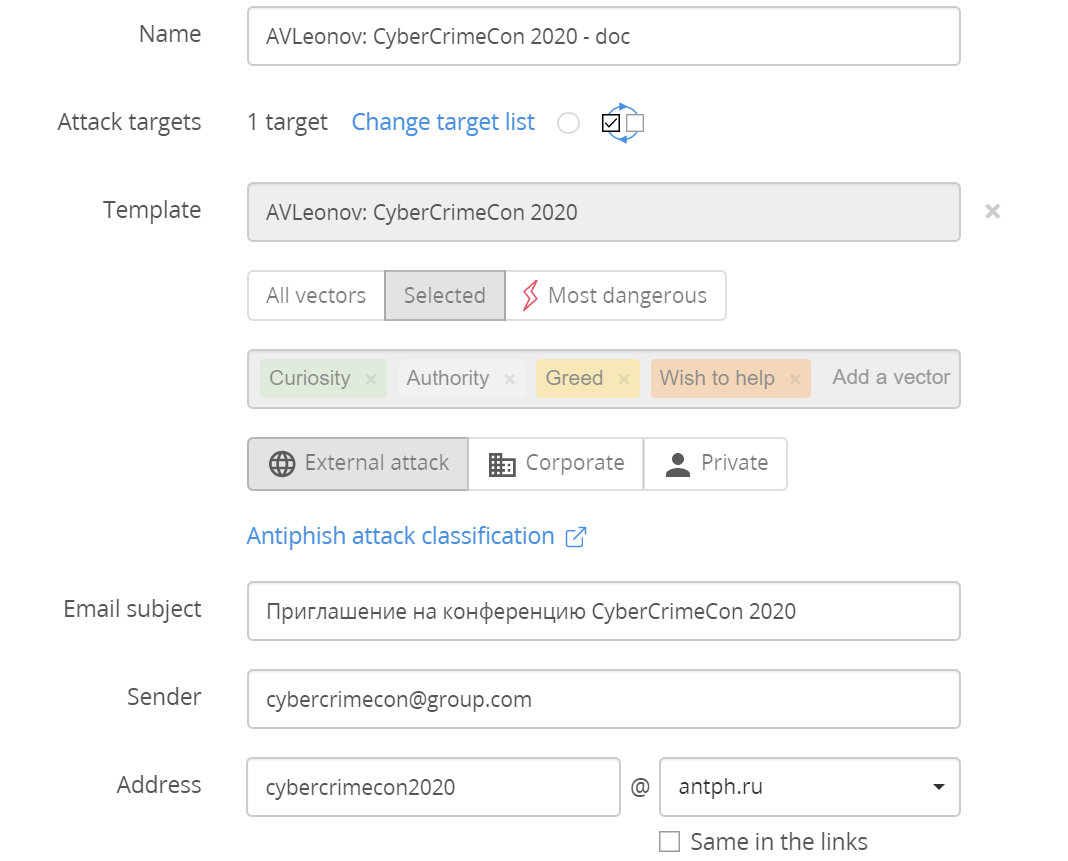
The message can be changed in WYSIWYG editor:
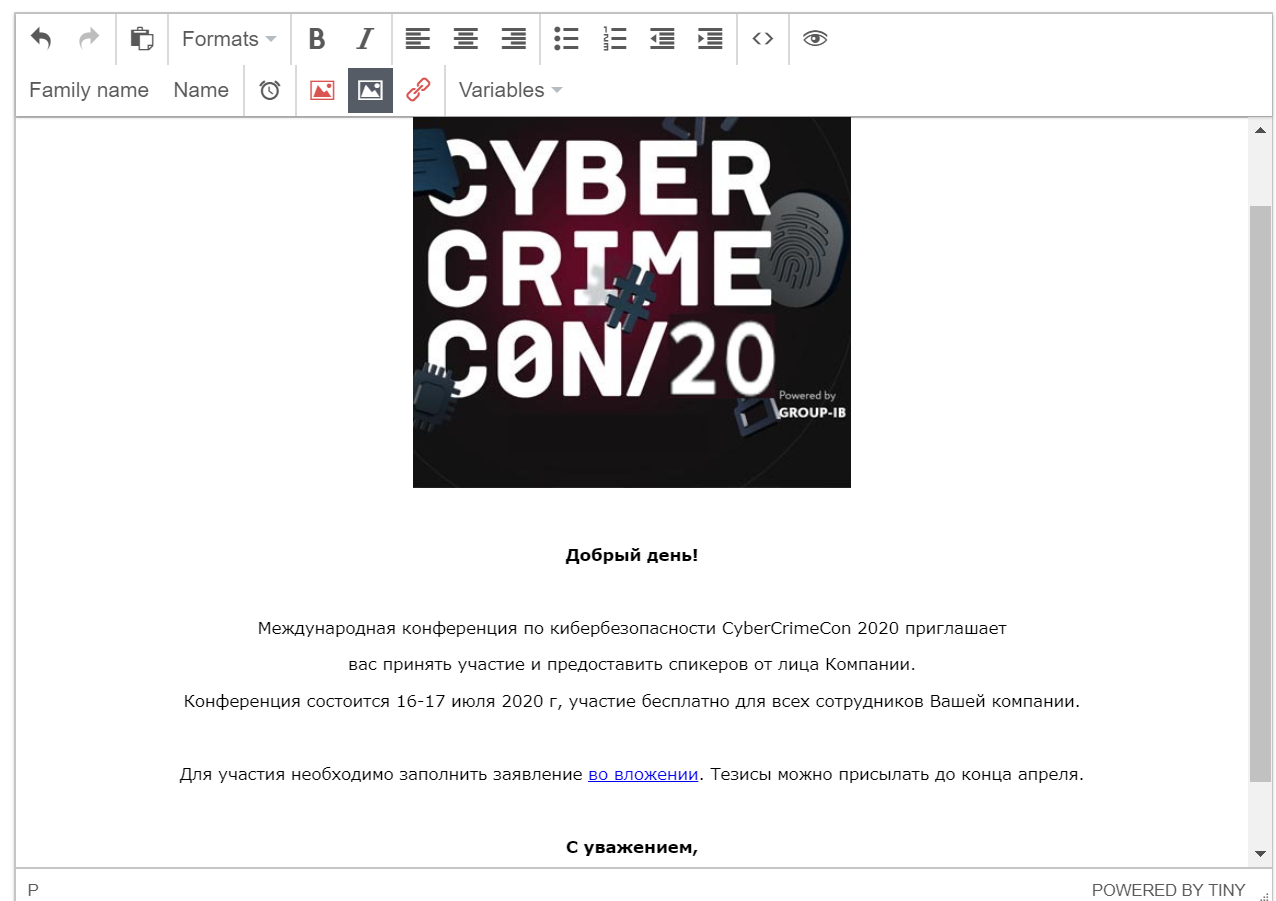
The message is in Russian, because these attacks have been prepared to target me. Here are some more examples of Antiphish attack templates in English, so you could get some ideas how they look like:


It’s also possible to manage “malicious” attachments and the final URL of the page, that will inform employee that they visited a phishing page:
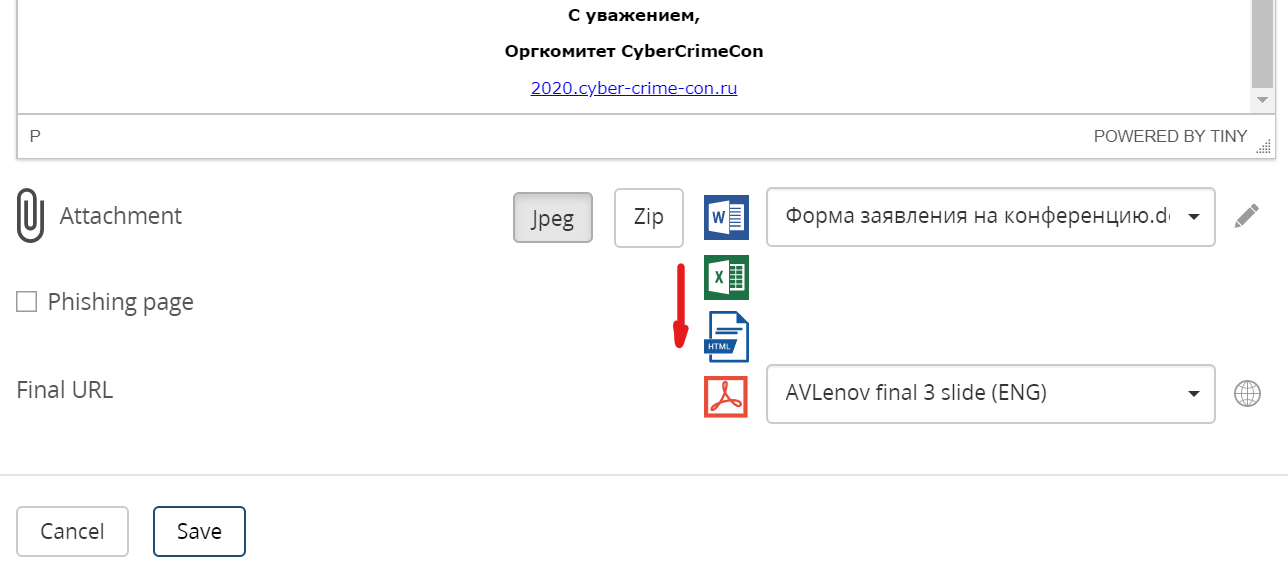
To get started, I made an attack with a “malicious” .docx attachment and sent an email to myself.
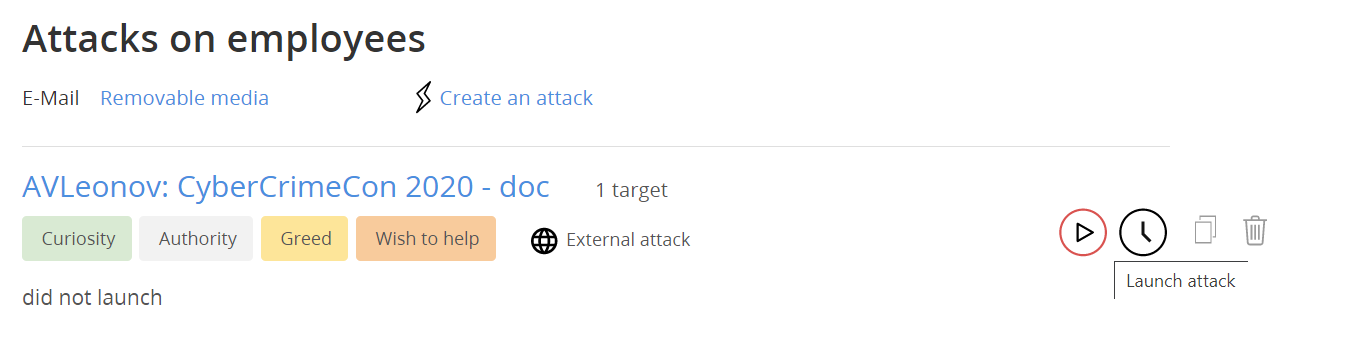
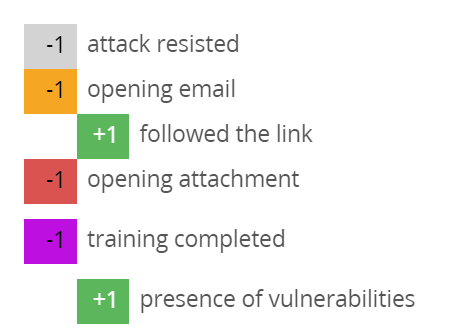
When I opened the email, I lost some points in Antiphish, and when I opened the attachment, I lost even more points and received instant feedback that my computer could be infected if it were a real attack.

All this is visible in real-time.
Advanced attacks
What about more exciting stuff?
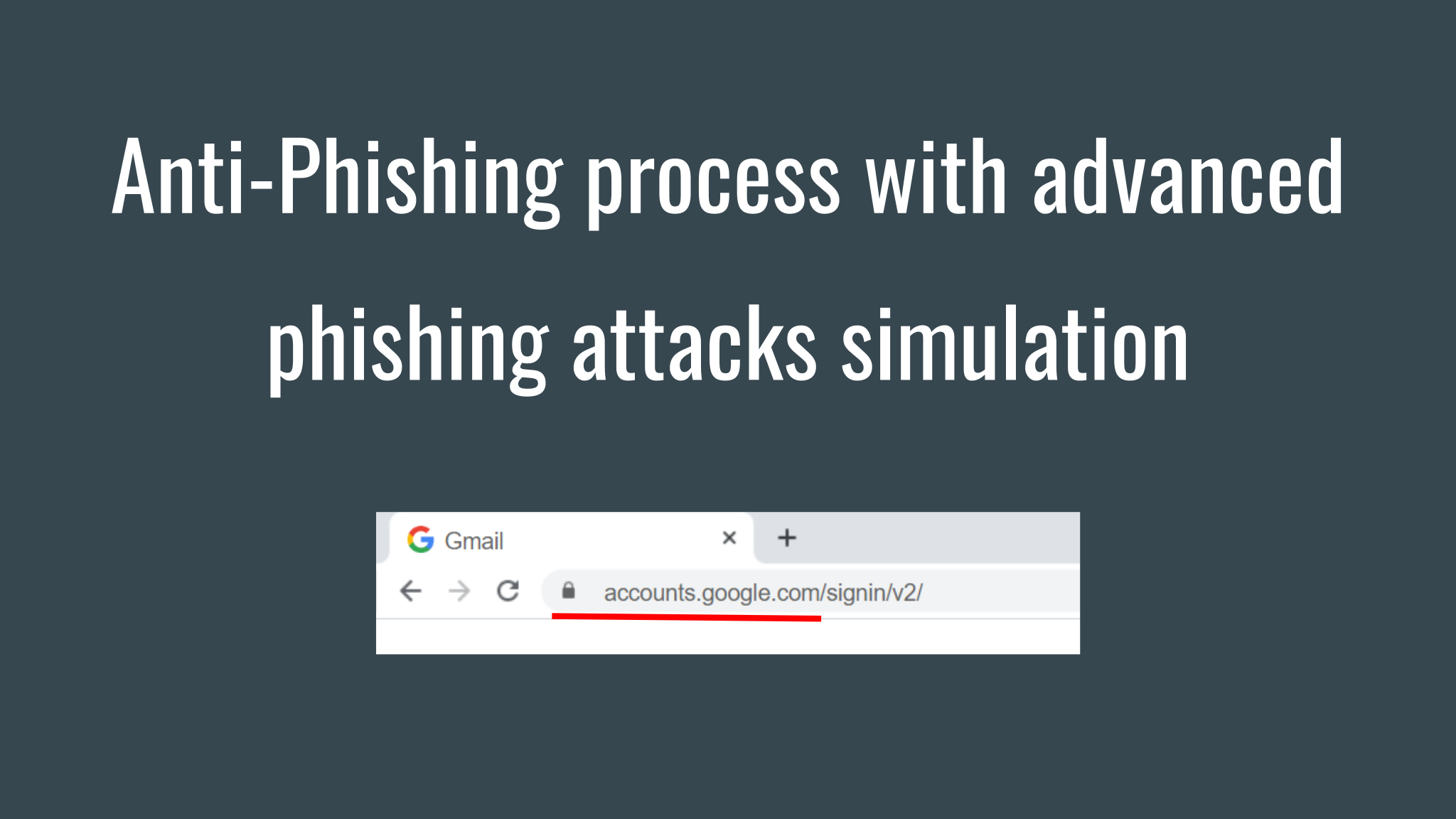
How do we usually identify a suspicious website? Well, probably, the domain name in the browser address bar will be unusual (contains typos, similar letters, some additional words). There may not be a lock icon. But what if everything is fine with this?
Antiphish designed and shipped three advanced attacks for me. I have received the emails and will demonstrate them.
Insurance company
I click on the link, see some banner, click on it, a new web page opens on which everything seems solid. There is a correct address in the address bar, the lock icon. Well, the page opened in a slightly strange way, hiding the Windows 10 taskbar, but nothing more.
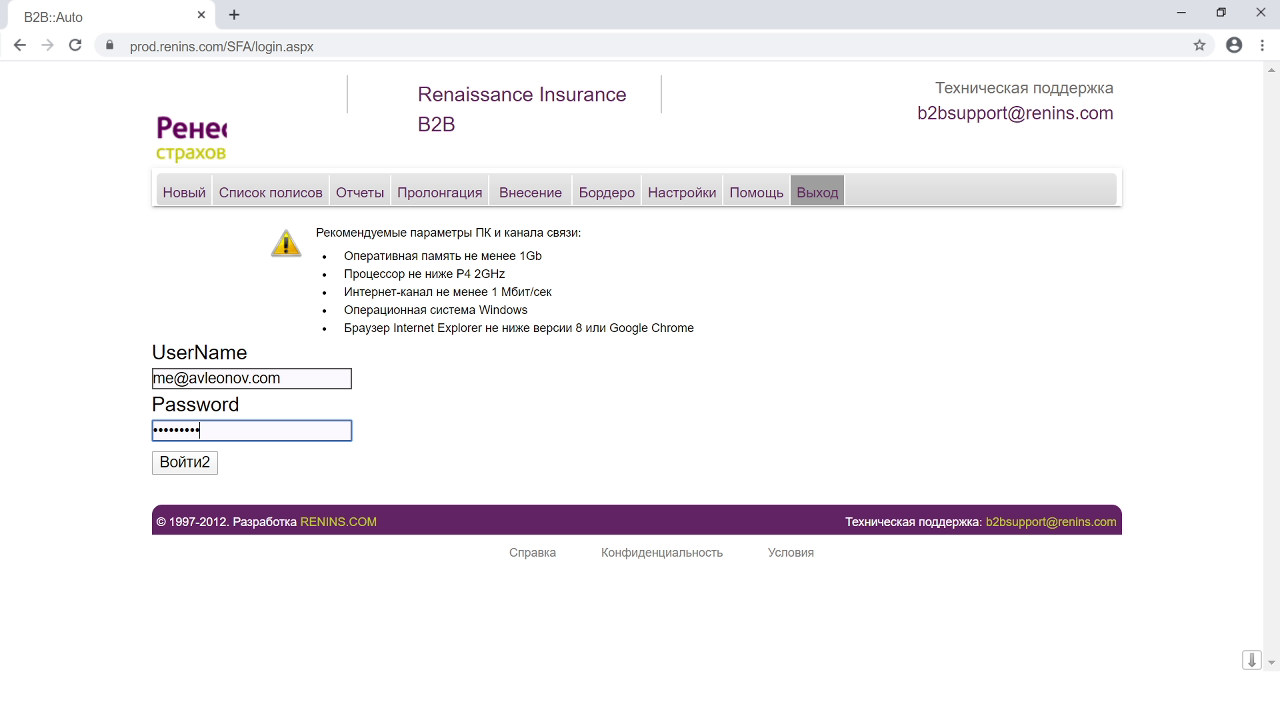
And the secret is that this interface of Google Chrome is not really a web browser interface, it is part of the web page content, and the page is opened in full-screen mode. Cool, right? When I entered authentication data, I got instant feedback warning:
You followed the link in a phishing email. Your computer has been hacked and all files are encrypted.
Fortunately, it was a training attack. You’re lucky. There’s nothing wrong with your computer…
Please be careful!! Don’t open attachments and don’t follow links in emails sent by unknown senders. Don’t answer suspicious emails. If in doubt, forward the letter with the attachment and / or link to the Information Security Department.
Google site
The second example is even better. I see an element that looks like Google reCAPTCHA antibot protection, that I see regularly and regularly click on it.
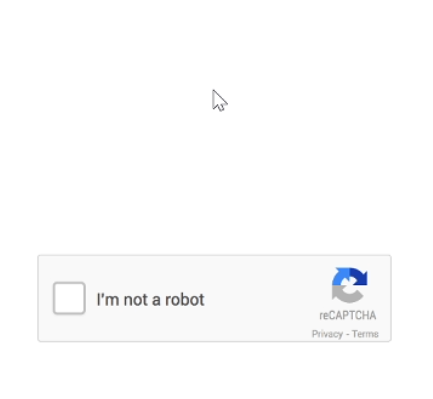
Then I get a page in full screen that emulates a Google Chrome web browser, but now it also draws a Windows 10 taskbar.
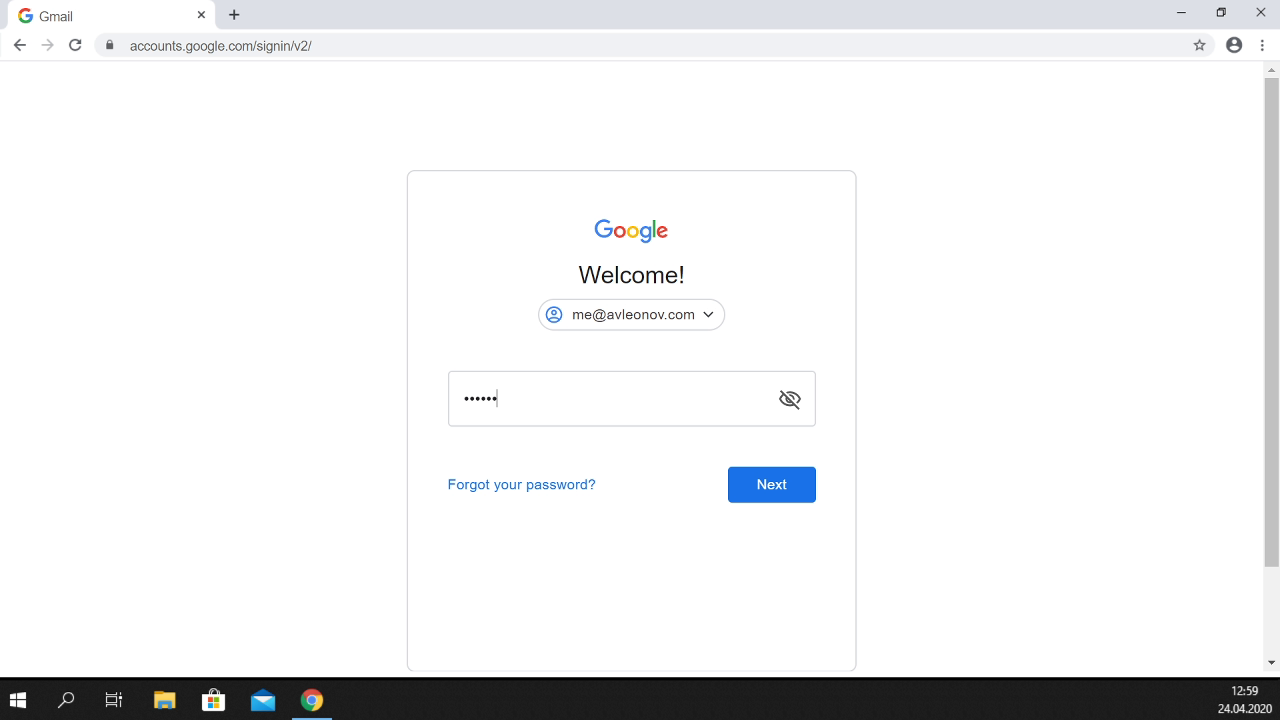
Your users are typically trained to look at the address bar to detect phishing websites. Could it work out in this sophisticated attack, huh?
And when I enter the authentication data to this page, I get the same warning.
Windows 10 login screen
The last example is the most interesting. The page shows something like a window with a Windows error message.
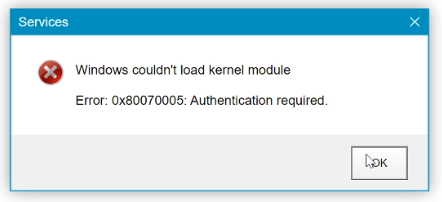
When I click on it, it shows me the login screen in Windows 10 with unlock gesture support. Of course, this is just a page in full screen.

It’s a bit messy, but it’s still easy to enter the domain password here. My name and email address were taken from Antiphish, and userpic was automatically grabbed from Social Networks, to make this attack targeted with zero efforts:
And when I enter the authentication data, I get the same warning as before.
So what do you think of this? When I saw this, it made a wow effect. ? Please share in the comments about how you deal with phishing in your organization.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
