Microsoft Patch Tuesday February 2022. Hello everyone! This episode will be about Microsoft Patch Tuesday for February 2022. I release it pretty late, because of the my previous big episode about the blindspots in the Knowledge Bases of Vulnerability Scanners. Please take a look if you haven’t seen it. Well, if you are even slightly interested in the world news, you can imagine that the end of February 2022 in Eastern Europe is not the best time to create new content on Vulnerability Management. Let’s hope that peace and tranquility will be restored soon. And also that geopolitical confrontation between the largest nuclear powers will de-escalate somehow.
But let’s get back to information security. While working on Microsoft Patch Tuesday report for February 2022, I made a lot of improvements to my open source project for vulnerability prioritization Vulristics. I want to start with them.
How many CVEs?
One of the old problems is the number of CVEs. You can see in the Patch Tuesday reviews made by the VM vendors, that they always mention a different number of CVEs. For example for February Patch Tuesday Tenable stated that 48 CVEs were patched, while other VM vendors reported up to 70 CVEs (ZDI, Qualys, Rapid7). I understand where Tenable got the number 48 that’s what the Microsoft API returns.
{"@odata.context":"https://api.msrc.microsoft.com/sug/v2.0/en-US/$metadata#vulnerability","@odata.count":48,"value":[{"id":"00000000-0000-0000-0000-0000815caad0","releaseDate":"2022-02-08T08:00:00Z","cveNumber":"CVE-2022-23280","cveTitle":"Microsoft Outlook for Mac Security Feature Bypass Vulnerability","releaseNumber":"2022-Feb","vulnType":"Security Vulnerability","latestRevisionDate":"2022-02-09T08:00:00Z","mitreText":"MitreCVE-2022-23280","mitreUrl":"https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-23280","publiclyDisclosed":"No","exploited":"No","latestSoftwareReleaseId":2,"latestSoftwareRelease":"Exploitation Less Likely","olderSoftwareReleaseId":2,"olderSoftwareRelease":"Exploitation Less Likely","denialOfService":"N/A","tag":"Microsoft Office Outlook","issuingCna":"Microsoft","langCode":"en-US","articles":[{"articleType":"FAQ","description":"<p><strong>Is the Preview Pane an attack vector for this vulnerability?</strong></p>\n<p>Yes, the Preview Pane is an attack vector.</p>\n","ordinal":10000},...BTW, I changed
https://api.msrc.microsoft.com/sug/v2.0/en-US/affectedProduct
to
https://api.msrc.microsoft.com/sug/v2.0/en-US/vulnerability
Because this url is now used in Microsoft web interface.
As for other numbers, this is because they count not only vulnerabilities that were released on a specific date, but also the vulnerabilities released between Patch Tuesdays. And that makes sense, since most of security professionals and IT administrators review Microsoft issues once in a month. Therefore, if we will ignore the vulnerabilities that were published between them, there is a chance that something critical can go under the radar.
But starting from what date do VM vendors count CVEs? I took the beginning of the month and got 70 CVEs:
MS PT Year: 2022
MS PT Month: February
MS PT Date: 2022-02-08
MS PT CVEs found: 48
Ext MS PT Date from: 2022-02-01
Ext MS PT Date to: 2022-02-07
Ext MS PT CVEs found: 22
ALL MS PT CVEs: 70But it seems to me that it is more correct to take the next day after the previous Patch Tuesday as Ext MS PT Date from.
MS PT Year: 2022
MS PT Month: February
MS PT Date: 2022-02-08
MS PT CVEs found: 48
Ext MS PT Date from: 2022-01-12
Ext MS PT Date to: 2022-02-07
Ext MS PT CVEs found: 46
ALL MS PT CVEs: 94I decided to make a new profile in Vulristics “ms_patch_tuesday_extended”. It will include all vulnerabilities that have been published since the previous Patch Tuesday, including the current Patch Tuesday date. There will also be a comment that the vulnerability was released before Patch Tuesday.
Direct comment links
There also was an issue with a search on the Tenable blog. It didn’t work even in GUI. After trying to search for “Patch Tuesday” I keep getting the error “This page isn’t working. www.tenable.com redirected you too many times”. I hope Tenable will fix this, but bugs like this can happen regularly. So, I decided to add the ability to define comments links directly in the file.
python3.8 vulristics.py --report-type "ms_patch_tuesday" --mspt-year 2022 --mspt-month "February" --mspt-comments-links-path "comments_links.txt" --rewrite-flag "True" comments_links.txt file
Tenable|Microsoft’s February 2022 Patch Tuesday Addresses 48 CVEs (CVE-2022-21989)|https://www.tenable.com/blog/microsofts-february-2022-patch-tuesday-addresses-48-cves-cve-2022-21989Exploit exclusions
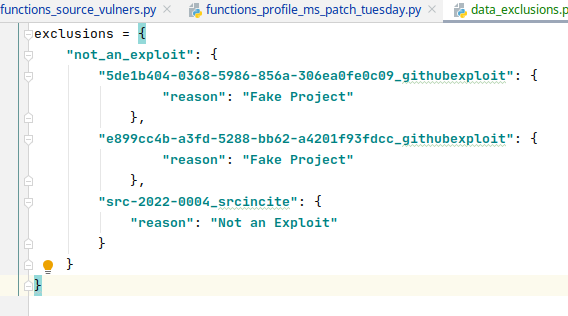
When I generated the report, I found many vulnerabilities there, for which there was a strange Log4Shell exploit. It was a fake project on github that mentioned thousands of CVEs.
What to do with it? Of course, you can simply exclude all github objects in Vulners.com API output and ignore such exploits. On the other hand, this is bad, because there may indeed be real exploits on github that other Exploit packs don’t have.
So instead I decided to add the ability to exclude vulners.com exploits in data_exclusions.py.
MS February 2020 Patch Tuesday
But let’s now take a look at the Patch Tuesday for February 2020. There were 94 vulnerabilities: 3 Critical, 20 High, 65 Medium and 6 Low.
The full report is available here: ms_patch_tuesday_february2022
Let’s look at 3 critical vulnerabilities:
- Remote Code Execution – Windows Kernel / Windows Runtime (CVE-2022-21971) and Remote Code Execution – Roaming Security Rights Management Services (CVE-2022-21974). Both of these vulnerabilities were not mentioned in the Patch Tuesday reports released by Vulnerability Management vendors. However, their criticality has increased due to the publication of exploits on github. These exploits were published by the same researcher. In both cases, exploitation requires opening a malicious rtf file in MS Word. Despite the fact that these are RCE vulnerabilities, they have Access Vector Local and User Interactions Required. Therefore, they are probably the most dangerous for desktops and will be exploited in phishing attacks.
- Remote Code Execution – Windows Authenticode (CVE-2013-3900). “A remote code execution vulnerability exists in the way that the WinVerifyTrust function handles Windows Authenticode signature verification for portable executable (PE) files. An anonymous attacker could exploit the vulnerability by modifying an existing signed executable file to leverage unverified portions of the file in such a way as to add malicious code to the file without invalidating the signature. An attacker who successfully exploited this vulnerability could take complete control of an affected system. Microsoft republishing a CVE from 2013 to inform customers that the EnableCertPaddingCheck is available in all currently supported versions of Windows 10 and Windows 11. Microsoft does not plan to enforce the stricter verification behavior as a default functionality on supported releases of Microsoft Windows. This behavior remains available as an opt-in feature via reg key setting, and is available on supported editions of Windows released since December 10, 2013. The reg key already exists in Window 10 and Window 11, so no security update is required but the reg key must be set. The vulnerability is exploited in the wild and is mentioned in CISA Known Exploited Vulnerabilities Catalog”.
Now let’s highlight some of the 20 high-level vulnerabilities:
- Elevation of Privilege – Windows Print Spooler (CVE-2022-21999, CVE-2022-22718). Two vulnerabilities with one exploit. “As researchers continue to focus their time on discovering flaws in Print Spooler, it is likely that attackers are as well, therefore organizations should apply these updates urgently”.
These were all vulnerabilities for which there is an exploit or a sign of “exploitation in the wild”. What other vulnerabilities are worth paying attention to?
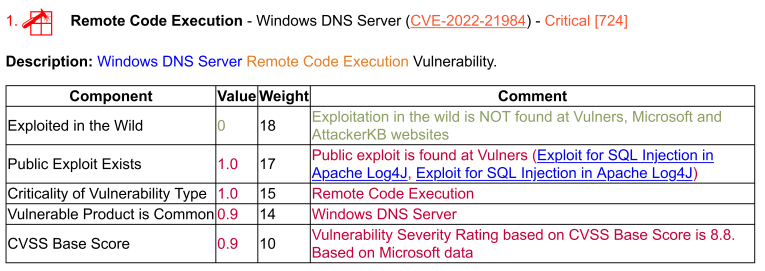
- Remote Code Execution – Windows DNS Server (CVE-2022-21984). “The server is only affected if dynamic updates are enabled, but this is a relatively common configuration. If you have this setup in your environment, an attacker could completely take over your DNS and execute code with elevated privileges. Since dynamic updates aren’t enabled by default, this doesn’t get a Critical rating. However, if your DNS servers do use dynamic updates, you should treat this bug as Critical.”
- Remote Code Execution – Microsoft SharePoint (CVE-2022-22005). “This patch fixes a bug in SharePoint Server that could allow an authenticated user to execute any arbitrary .NET code on the server under the context and permissions of the service account of SharePoint Web Application. An attacker would need “Manage Lists” permissions to exploit this, by default, authenticated users are able to create their own sites and, in this case, the user will be the owner of this site and will have all necessary permissions.”
- Remote Code Execution – Microsoft Office ClickToRun (CVE-2022-22004) and Remote Code Execution – Microsoft Office Graphics (CVE-2022-22003). “RCEs affecting Microsoft Office. Although this requires a local user to open a malicious file, these sorts of social engineering attacks are common and can be very effective. Updates should be rolled out to end users as soon as reasonably practicable.”
Among the vulnerabilities of the medium level, the following vulnerabilities are quite interesting:
- Elevation of Privilege – Windows Kernel (CVE-2022-21989) and Windows Win32k (CVE-2022-21996). Not much is known about these vulnerabilities, but if exploits come out, these vulnerabilities can cause a lot of trouble.
- Security Feature Bypass – Microsoft Outlook (CVE-2022-23280). “Microsoft Outlook for Mac Security Feature Bypass Vulnerability. This Outlook bug could allow images to appear in the Preview Pane automatically, even if this option is disabled. On its own, exploiting this will only expose the target’s IP information. However, it’s possible a second bug affecting image rendering could be paired with this bug to allow remote code execution. If you are using Outlook for Mac, you should double-check to ensure your version has been updated to an unaffected version.”
There were also a lot of vulnerabilities in Microsoft Edge. Most of them were published before February 2022 Patch Tuesday from 2022-01-12 to 2022-02-07. Some of them have the Memory Corruption type, for 6 the type could not be detected from the description.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
