Hello everyone! This episode will focus on the news from my open source Vulristics project for vulnerability analysis and prioritization.
Alternative video link (for Russia): https://vk.com/video-149273431_456239122
EPSS v3
The third iteration of the Exploit Prediction Scoring System (EPSS) was released in March. It is stated that EPSS has become 82% better. There is a pretty cool and detailed article about the changes. For example, EPSS Team began to analyze not 16 parameters of vulnerabilities, but 1164. I have a suspicion that most of these properties are vendor labels, as in the table.
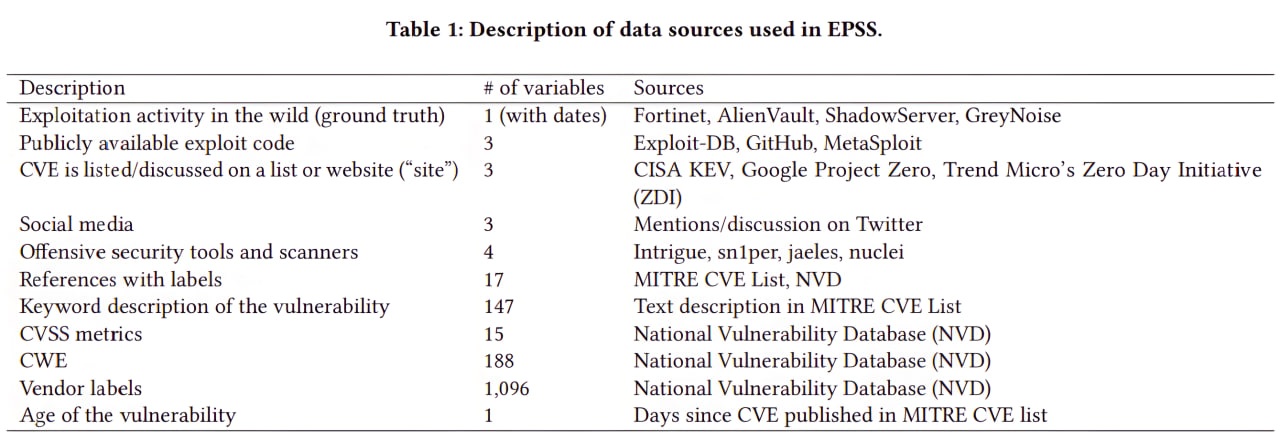
But trying to figure out how it actually works is not very promising. After all, this is the output of some neural network. So there is no algorithm there. In terms of complexity and incomprehensibility, this is already similar to Tenable VPR. But the fact that EPSS is available for free redeems everything. 😇 By the way, the article mentions Tenable VPR and other commercial scores and criticizes them for their proprietary nature, public inaccessibility, and the fact that these scores are partly based on expert opinion, and not just on data.
I have looked at the EPSS values for some CVEs:
- For a MS Word RCE vulnerability (CVE-2023-21716) with a recent PoC, EPSS is very high (0.16846,0.95168).
- For SPNEGO (CVE-2022-37958), for which a public exploit should appear in Q2, EPSS is also high (0.07896,0.93195).
- For a random MS Edge vulnerability (CVE-2023-0696) from February MS Patch Tuesday (there are dozens of them every month), EPSS is low (0.00062,0.24659)
- I took a vulnerability with high EPSS – CVE-2023-0297 (0.04128,0.90834). It is also clear why, there is a link to the exploit directly in NVD.
At first glance, everything is quite adequate. 👍
I wouldn’t recommend prioritizing vulnerabilities solely based on EPSS. But using it as an additional factor with the same weight as the CVSS Base Score (and possibly higher) can be quite good. This value is unlikely to rise up for no reason at all. If it goes to 0.9 and above, it makes sense to take a closer look at the vulnerability.
EPSS v3 Support in Vulristics
I have added support for EPSS data in Vulristics. EPSS has become another data source, so the command to analyze a set of CVE identifiers will look like this:
$ python3 vulristics.py --report-type "cve_list" --cve-project-name "New Project" --cve-list-path "analyze_cve_list.txt" --cve-comments-path "analyze_cve_comments.txt" --cve-data-sources "ms,nvd,epss,vulners,attackerkb" --rewrite-flag "True"
Adding a new source is not a difficult task. I did it by analogy with NVD. However, the question arose: which value of EPSS to use. There were 2 options:
- Probability – “probability of observing exploitation activity in the next 30 days”.
- Percentile – a value indicating how many CVE vulnerabilities has a lower probability to be observed exploited, than this particular CVE vulnerability. “For example, an EPSS probability of just 0.10 (10%) rests at about the 88th percentile — meaning that 88% of all CVEs are scored lower”.
I’ve come to the conclusion that the Probability values are too small and differ little from each other, so it’s better to use Percentile.
I updated the report for the April MS Patch Tuesday.
It looks good enough, but with some oddities.
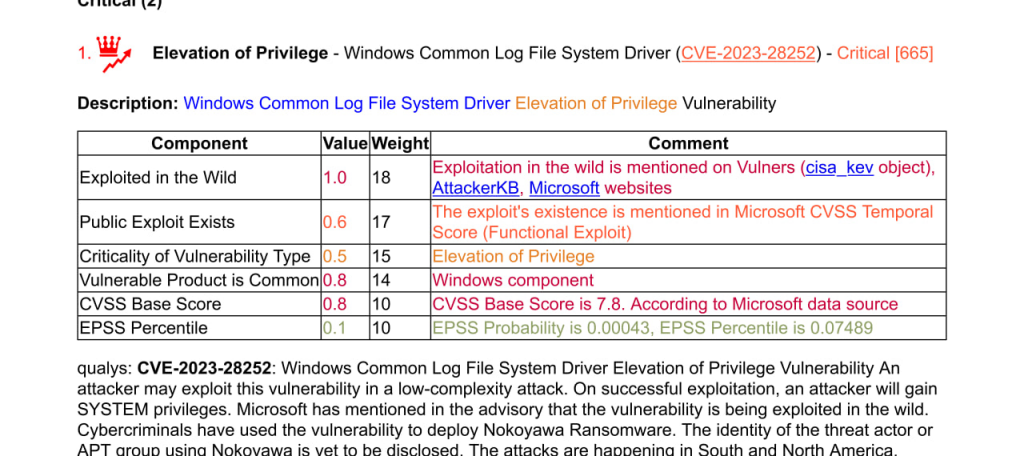
The most critical vulnerability Elevation of Privilege – Windows Common Log File System Driver (CVE-2023-28252), which is present in CISA KEV, has a very low EPSS for some reason. 🤷♂️ Therefore, the result of some ML analysis is, of course, good, but do not lose common sense. 😉
Vulristics integration into Cloud Advisor
Cloud Advisor uses Vulristics to prioritize vulnerabilities. A great example of how my open source project can be integrated into a commercial product. 🙂 In this case, into a Cloud Security Posture Management (CSPM) solution. Vulristics is released under the MIT license, so it can be freely used in any way: as a utility, as individual functions, as a methodology and algorithms for calculating the criticality of vulnerabilities. There are no requirements to open your derived code or anything like that.
Here is an excerpt from the press release about the new vulnerability management feature in Cloud Advisor:
“Additionally, the algorithms of the Vulristics tool are utilized for prioritization while taking into account a number of variables, such as the type of vulnerability, the CVSS score and the existence of a public exploit. This enables you to concentrate your efforts on fixing the vulnerabilities that actually pose a threat to your infrastructure.”
If you have a large cloud infrastructure and don’t know how to control its security, take a look at Cloud Advisor. By the way, this company was created by the founders of Agnitum, the vendor of the Agnitum Outpost personal firewall popular in the ’00s – I used it very actively. 🙂 They are very reasonable and skilled guys.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Microsoft Patch Tuesday April 2023: CLFS EoP, Word RCE, MSMQ QueueJumper RCE, PCL6, DNS, DHCP | Alexander V. Leonov
Pingback: Выпустил блогопост и видяшку по последним новостям Vulristics для англоязычного канала и блога | Александр В. Леонов