February 2024: Vulremi, Vuldetta, PT VM Course relaunch, PT TrendVulns digests, Ivanti, Fortinet, MSPT, Linux PW. Hello everyone! In this episode, I will talk about the February updates of my open source projects, also about projects at my main job at Positive Technologies and interesting vulnerabilities.
Alternative video link (for Russia): https://vk.com/video-149273431_456239140
Let’s start with my open source projects.
Vulremi
A simple vulnerability remediation utility, Vulremi, now has a logo and a repository on GitHub.
The logo features a long-handled farming weeding tool and a special pushing stick from the International Gladiators TV show from the 90s.

The weeding tool symbolizes the routine but necessary work of describing IT assets and establishing regular patching agreements. The push stick symbolizes efforts to motivate IT to comply with asset patching agreements.
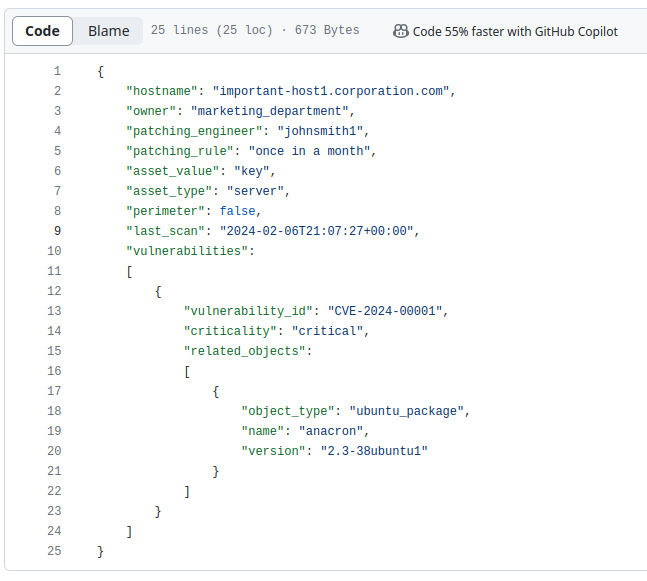
So far, this project has a description in three posts in Russian [1, 2, 3] and an example of an IT asset description.
Vuldetta
I also worked on the Vuldetta project – an API for detecting vulnerabilities based on a list of Linux packages.
I’m going to use it as the “brains” for my Scanvus vulnerability scanner. In the same way as the commercial Vulners Linux API or Vulns.io API are used now.
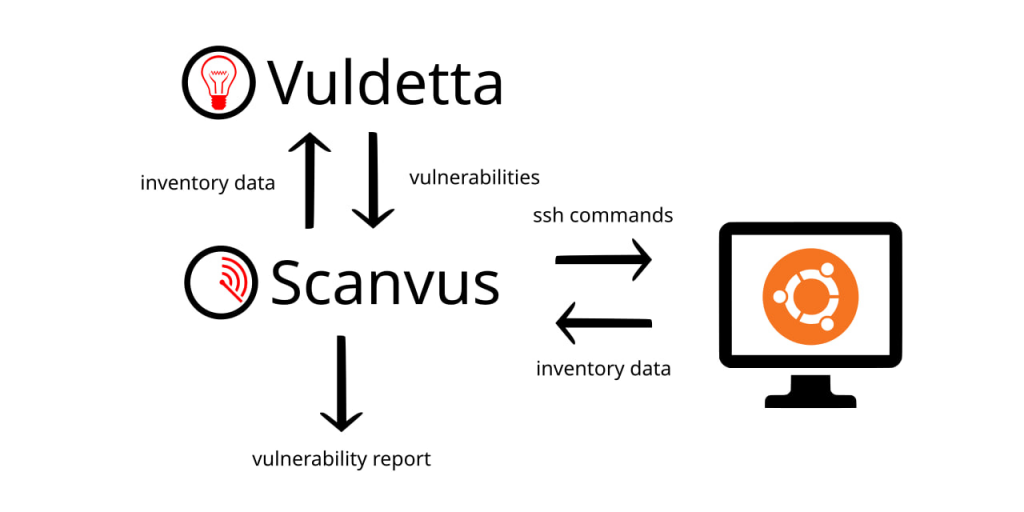
I’m currently researching the structure of Ubuntu OVAL content to turn it into something easier to work with.
Positive Technologies
VM Education
In my day job at Positive Technologies, I was involved in preparations for the relaunch of the Vulnerability Management training course on March 24th. The course content has been expanded and improved.

I recorded 2 new video modules for it:
🔹 Building a Vulnerability Management system based on open source and freeware components. 🆓 What tools can be used to detect and prioritize vulnerabilities, as well as visualize the state of the infrastructure. What are the pitfalls there? 🪨
🔹 Network perimeter scanning. Starting from understanding what an organization’s perimeter consists of, to how to organize regular scanning and vulnerability remediation. 📊
Digests of trending vulnerabilities
At Positive Technologies, we also began publishing monthly digests on trending vulnerabilities. We have released the January and February digests. The February digest will also be released in video format.
Vulnerabilities
Now let’s talk about the interesting vulnerabilities of February.
Ivanti
The most hyped vulnerabilities of February on a global scale were 3 vulnerabilities in the products Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA (CVE-2024-21887, CVE-2023-46805, CVE-2024-21893), which allow attackers to compromise hardware and virtual appliances.
These solutions require access from the Internet to operate, so it is not surprising that these Ivanti solutions are good targets for attackers.
Public exploits are available for all three vulnerabilities and there are signs of active exploitation in the wild. Exploitation also includes the installation of backdoors such as DSLog and GLASSTOKEN.
A recent study by Eclypsium showed that Ivanti devices run on an outdated, unsupported version of the Linux distribution CentOS 6.4 and use outdated packages with many critical vulnerabilities.
But there’s good news. Despite the fact that Ivanti is a very popular vendor on a global scale, it is practically not represented in Russia.
This is also true for ScreenConnect, a remote desktop solution developed by ConnectWise, which had a critical exploitable RCE (CVE-2024-1708, CVE-2024-1709) in February.
Fortinet
Also in February, a critical Arbitrary Code Execution vulnerability was released in Fortinet FortiOS and FortiProxy (CVE-2024-21762). According to the vendor, the vulnerability could already be exploited in hacker attacks.
Fortinet previously reported that attackers used a similar FortiOS vulnerability to deploy the COATHANGER remote access Trojan.
Cisco
The Cisco ASA Information Disclosure vulnerability (CVE-2020-3259), discovered by Positive Technologies researchers 4 years ago, in May 2020, is used by the Akira ransomware to gain initial access.
The forensics team of the Swedish company Truesec reported this on January 29. They found that in at least 6 incidents related to the Akira ransomware, the entry point was Cisco AnyConnect with the Information Disclosure vulnerability CVE-2020-3259. On February 15, the vulnerability was added to CISA KEV.
Microsoft Patch Tuesday
As usual, I analyzed Microsoft Patch Tuesday vulnerabilities using my open source Vulristics project. The February Microsoft Patch Tuesday contained 105 (104) vulnerabilities (this includes 32 that have appeared since January).
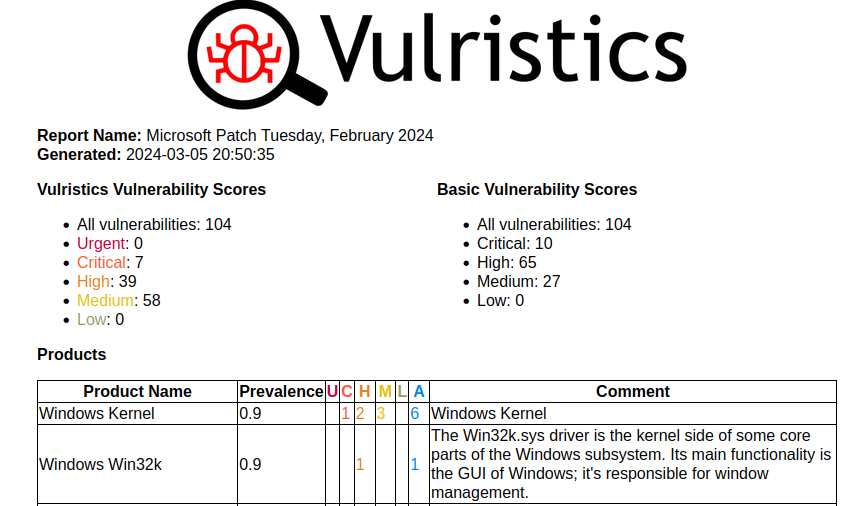
Microsoft has changed the descriptions for several vulnerabilities, so in the end the following vulnerabilities show signs of exploitation in the wild:
🔻Two of them are related to Bypassing Security Features in Windows SmartScreen (CVE-2024-21351) and Internet Shortcut Files (CVE-2024-21412). In both cases, the point is that the user can open a downloaded malicious file and this dangerous activity will not be blocked by the Windows Defender protection mechanism.
🔻 Two more vulnerabilities are related to email and NTLM Relay attacks: Elevation of Privilege in Microsoft Exchange (CVE-2024-21410) and Arbitrary Code Execution in Microsoft Outlook (CVE-2024-21413). As for the Outlook vulnerability, Microsoft marked this vulnerability as being exploited in the wild, but then they changed their decision and removed the mark. But for this vulnerability there is a CheckPoint article with a detailed technical description and exploit code that allows an attacker to gain access to the victim’s computer after clicking on a link in an incoming email message in Outlook.
🔻 At the very end of February, a sign of exploitation in the wild appeared for the Elevation of Privilege – Windows Kernel (CVE-2024-21338). Researchers from Avast released a write-up in which they claim that the vulnerability was exploited by the Lazarus group.
🔻And finally, one Chromium vulnerability that is actively exploited in the wild. This is Memory Corruption – Chromium (CVE-2024-0519).
Of the rest, the following can be noted:
🔹 Elevation of Privilege – Windows Kernel (CVE-2024-21345, CVE-2024-21371)
🔹 Remote Code Execution – Microsoft Outlook (CVE-2024-21378)
🗒 February Microsoft Patch Tuesday Vulristics report
Linux Patch Wednesday
As usual, I analyzed Linux Patch Wednesday vulnerabilities using Vulristics. Linux vulnerabilities that started being patched last month. 149 vulnerabilities.
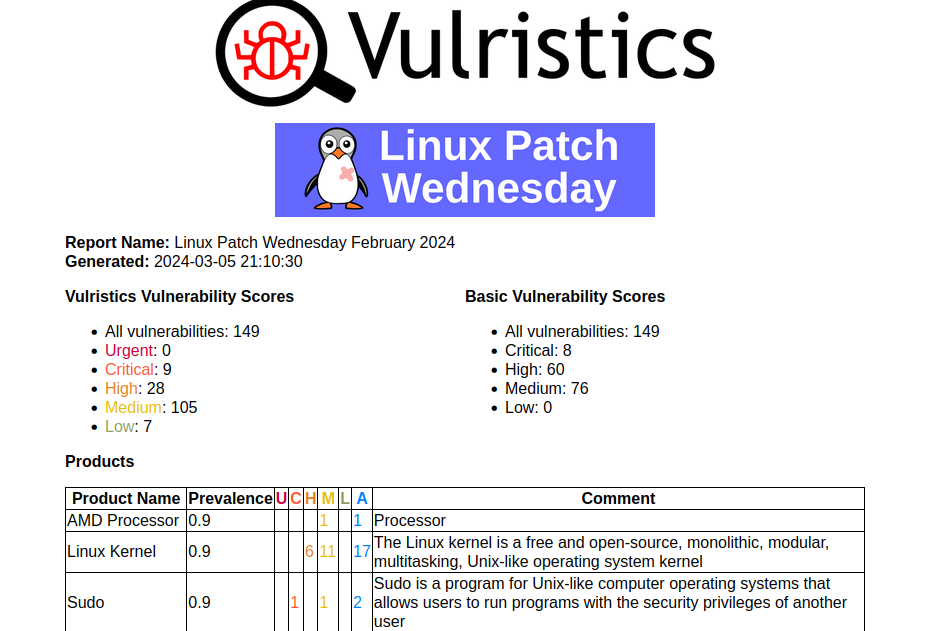
Among them there are no vulnerabilities with the sign of active exploitation in the wild. There are 20 vulnerabilities with PoCs/exploits. At first glance, all the high-profile vulnerabilities of the month are in place:
🔻 Elevation of Privilege – GNU C Library (CVE-2023-6246). This is another glibc vulnerability that Qualys found.
🔻 Information Disclosure – runc (CVE-2024-21626). This is a container breakout vulnerability.
🔻 Denial of Service – dnsmasq (CVE-2023-50387). This is about the ‘KeyTrap’ attack on DNSSEC.
🔻 Authentication Bypass – Sudo (CVE-2023-42465). The only publication about this vulnerability was in 2023, but this vulnerability began to be patched in RPM-based distributions in February 2024.
🗒 February Linux Patch Wednesday Vulristics Report

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Закругляю февраль традиционным англоязычным постом и видяшкой | Александр В. Леонов