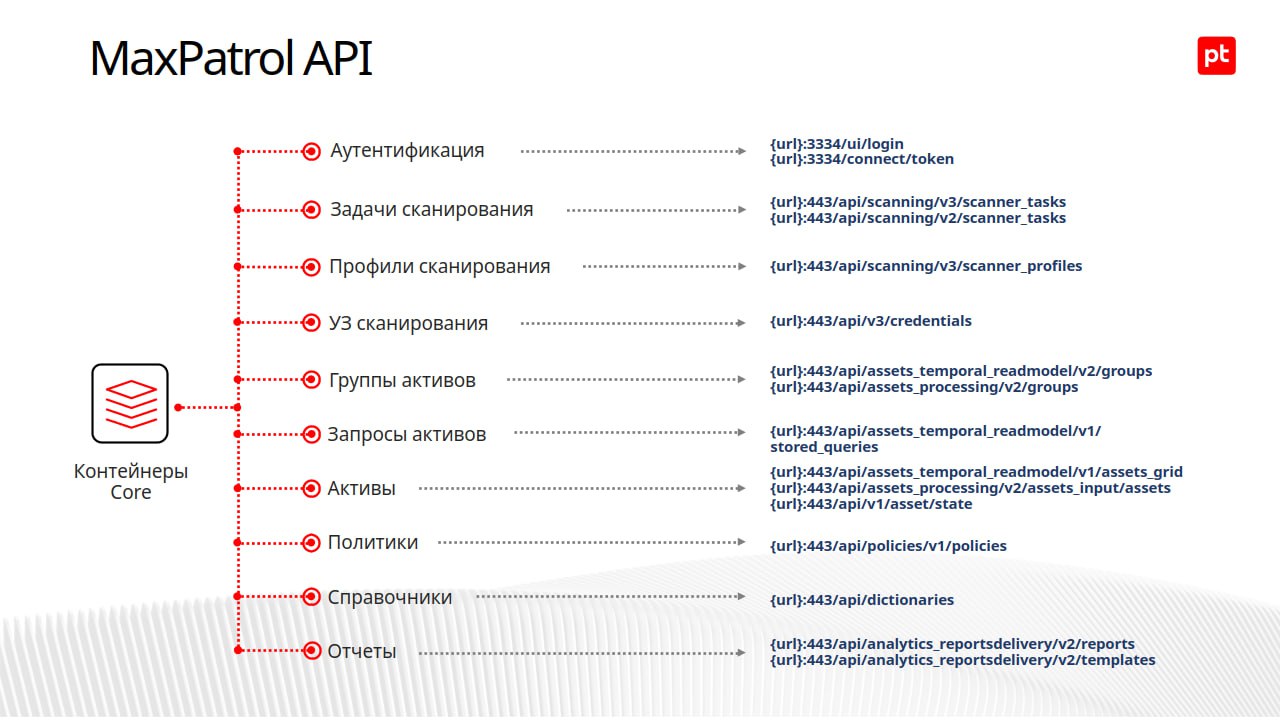
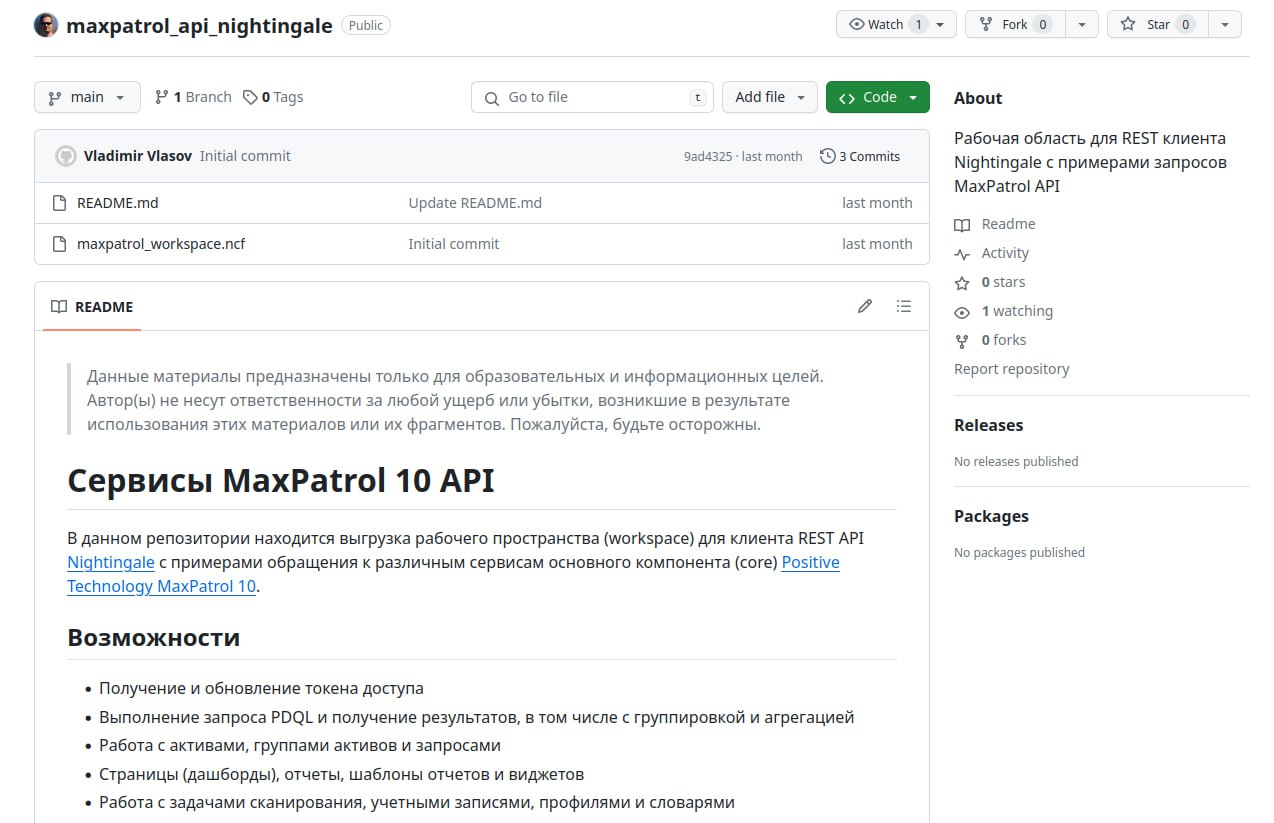
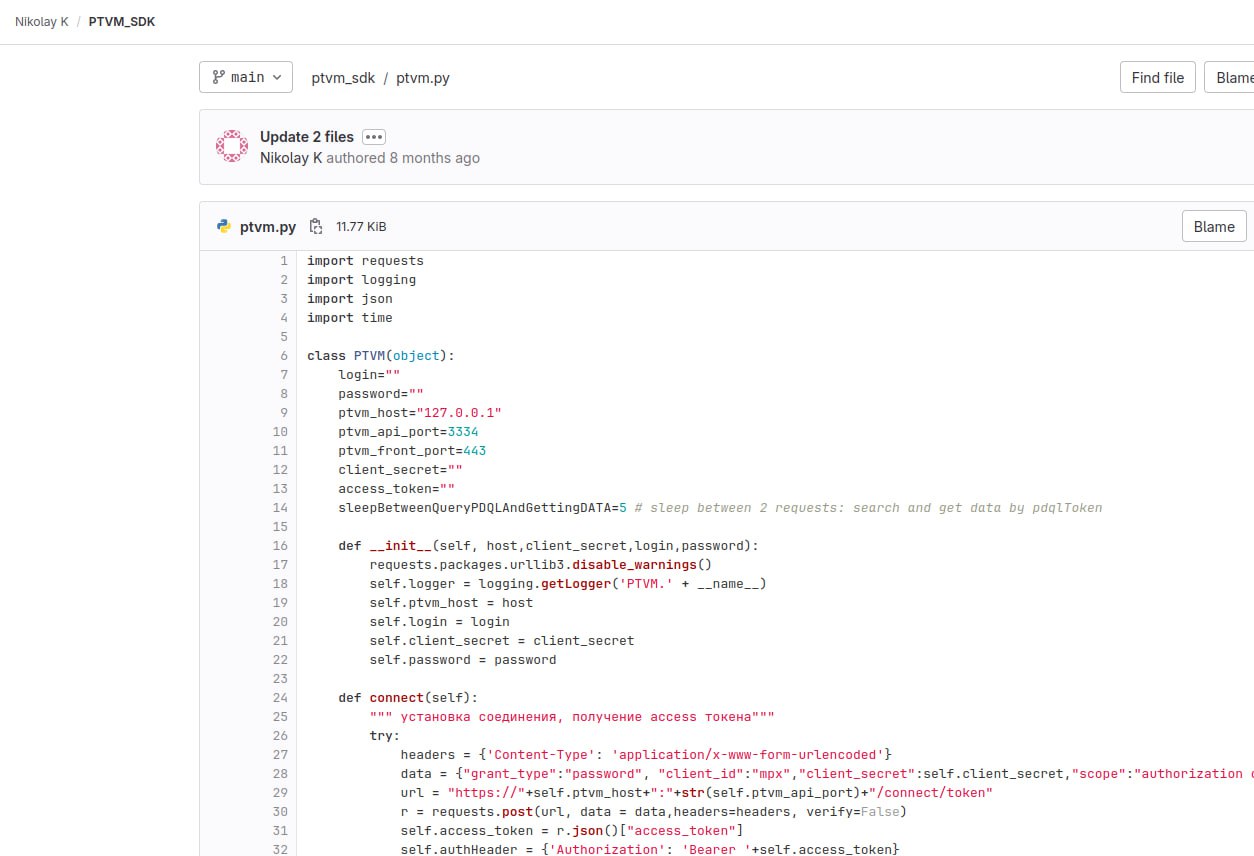
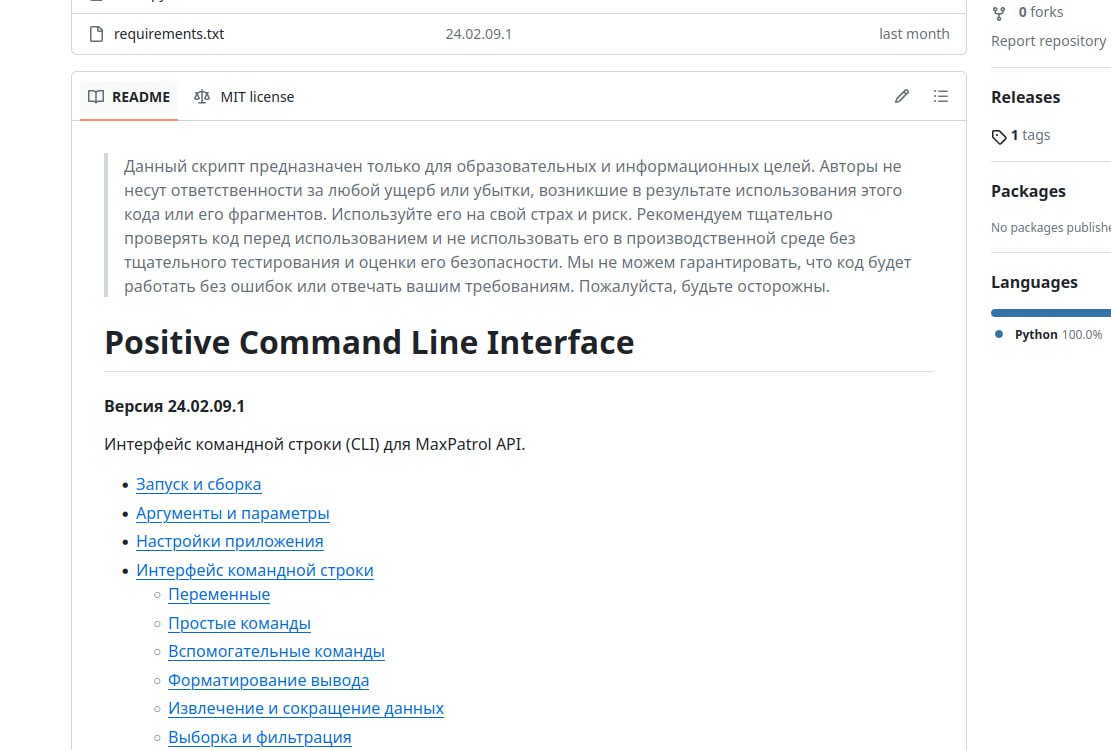
I watched the recording of the Positive Technologies webinar “How to use MaxPatrol VM API: theory and practice“. On the theoretical part, everything is clear: there is a documented API; it is the same for integrations and Web GUI. 🙂
On the practical side they showed:
🔻 How to use the MaxPatrol API in the Nightingale REST client (examples on GitHub).
🔻 Unofficial PTVM SDK. A small Python script with one class for working with the MaxPatrol API.
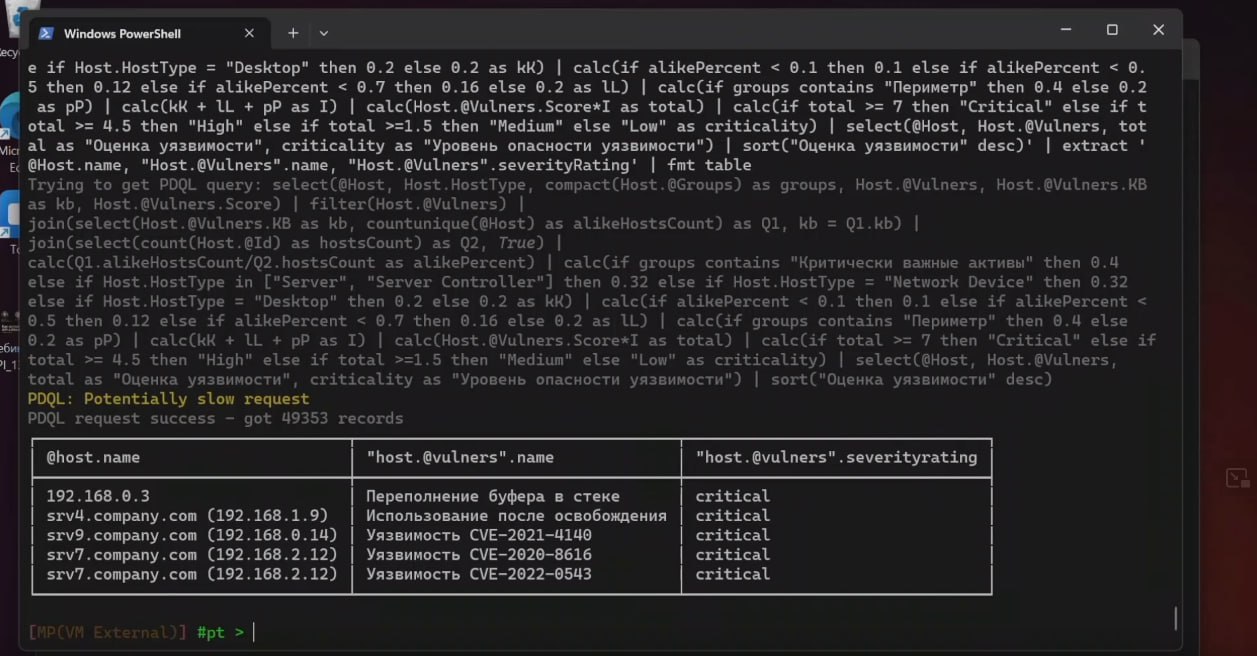
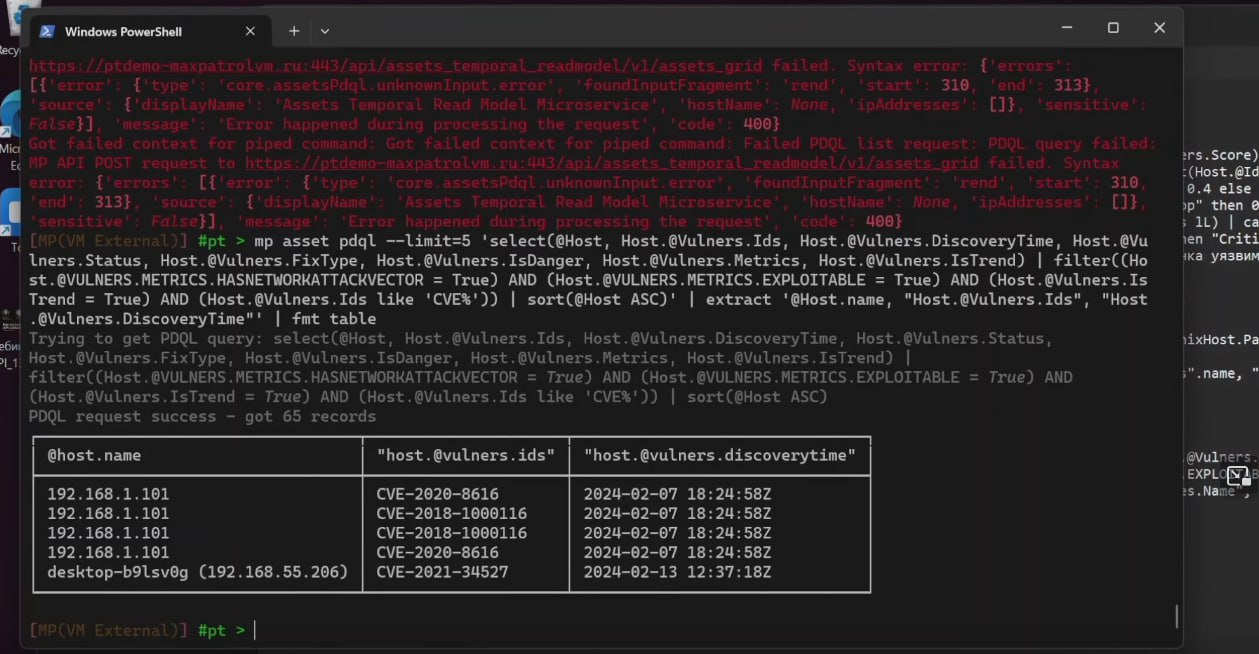
🔻 Positive CLI for MaxPatrol API. So, automation can be done simply with shell scripts! 😇 A much more functional project than the SDK, also in Python. The screenshots show the vulnerabilities with criticality calculated using FSTEC methodology and trending vulnerabilities with an exploit.
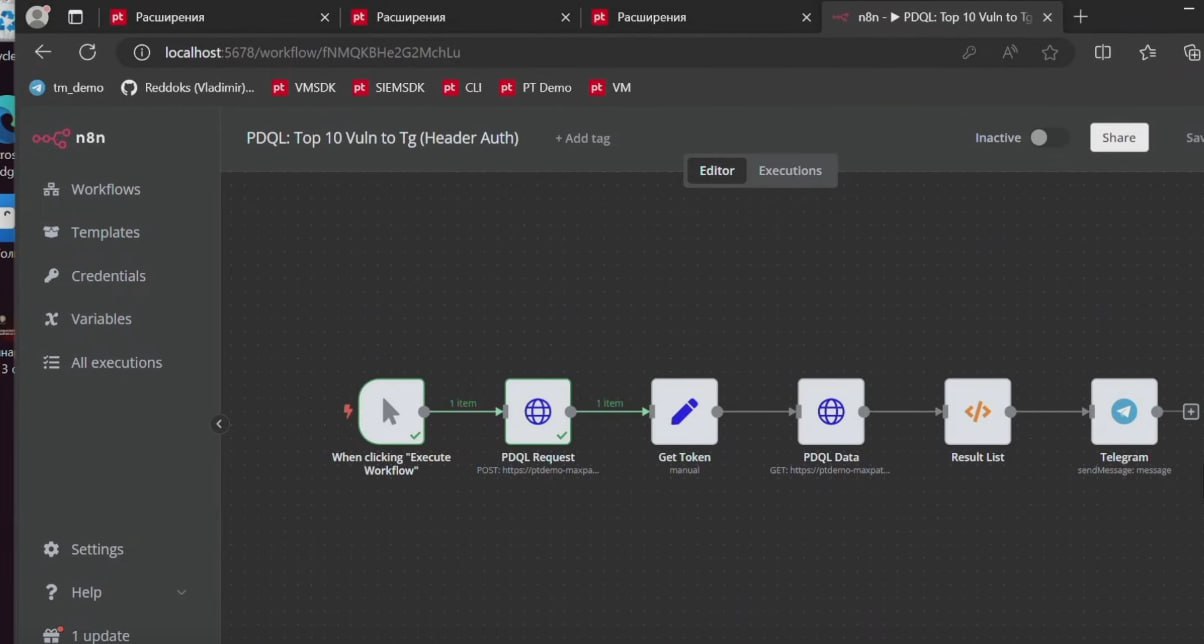
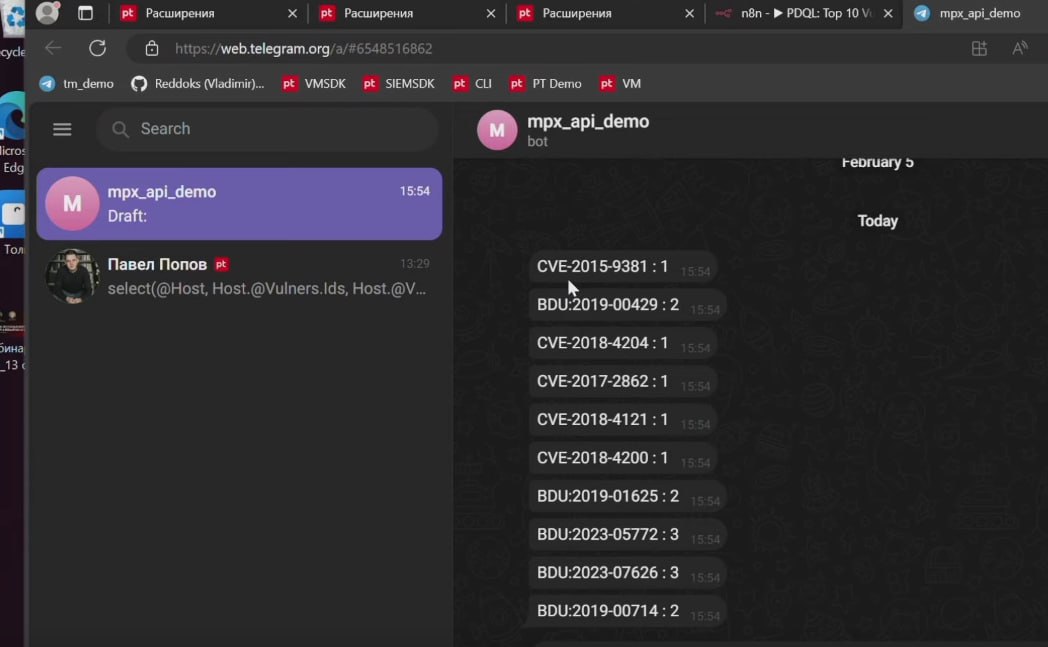
🔻 How to use the MaxPatrol API in the low-code tool n8n (e.g. sending query results to Telegram).
Links to projects are on the addons page.
Show it to your colleagues who work with MaxPatrol VM. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.