openvas_commander for OpenVAS installation and management. upd. 29.09.2018 Unfortunately, the script does not work after Greenbone moved the sources from their internal repository to GitHub. It’s necessary to edit the script. Stay tuned.
If you will search articles about OpenVAS most of them will be about installation: installation in Kali (in 3 lines) and various bash scripts for installing it from the sources.
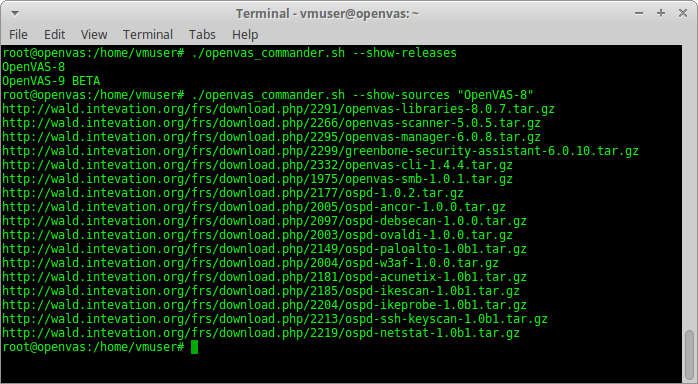
Pros of using installation the sources:
- It is the the fastest way to obtain current stable and beta version OpenVAS for every day use and testing.
- Security reasons. As soon as there are no official OpenVAS packages you need to rely on some individuals who provide packages for popular distributions and in some cases it is not the option.
- Some scripting for updating OpenVAS database and managing OpenVAS services will be required anyway. Starting the OpenVAS is still a quest: you need to check the statuses of database, start the services in a right order.
- This is the first step towards the full automation of OpenVAS scanning and testing.
Cons:
- You will need to install lot’s of additional packages to build OpenVAS binaries. More than 2Gb of files should be downloaded. It may take hours to install configure all this packages on a slow machine (especially all those TeX packages).
- Building all packages also takes time. It takes as much time as knowledge base update.
I wrote a small bash script to simplify OpenVAS installation and management of – openvas_commander.sh. Tested on Debian 8.5, should work on Ubuntu and Kali.
Upd 10.04.2017 Read how to use this script to install OpenVAS 9 on Debian in the post “Installing OpenVAS 9 from the sources“.
wget https://raw.githubusercontent.com/leonov-av/openvas-commander/master/openvas_commander.sh
chmod +x openvas_commander.sh
What are its advantages over other similar scripts?