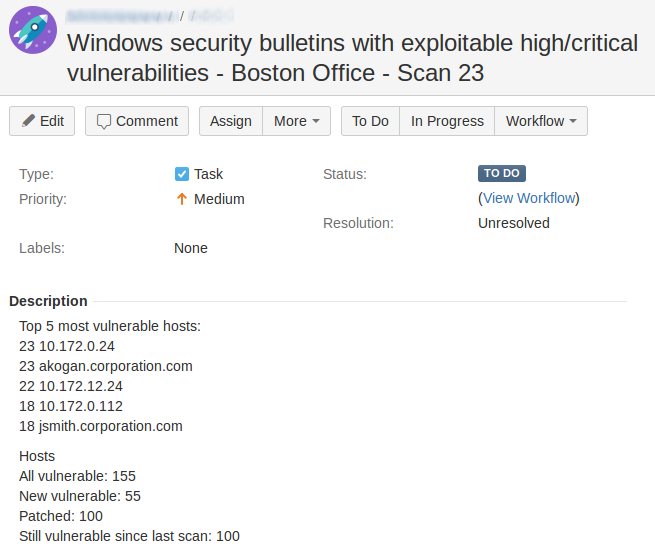
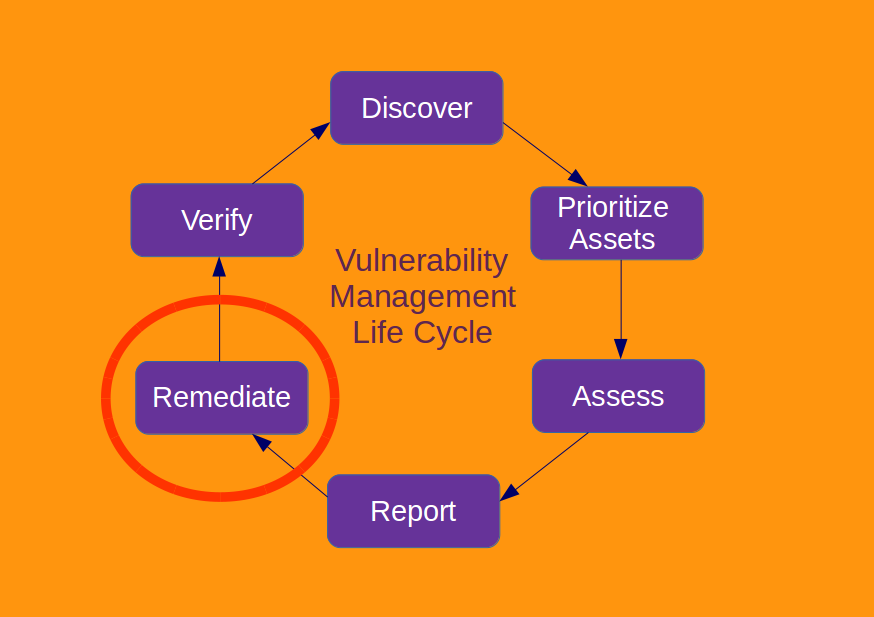
Vulnerability Assessment without Vulnerability Scanner. This will be a practical confirmation of my thesis from “Vulnerability scanners: a view from the vendor and end user side“: the scanner for one operating system is easy to make. I also want to demonstrate that data collection and data analysis for Vulnerability Assessment may be successfully performed separately. There is no need to take the data directly from the vulnerable hosts, when it is already stored somewhere else, for example in IT monitoring systems.

The opacity of data collection and the need to have a privileged account on the remote host, traditionally causes conflicts between IS and IT departments and complicates implementation of VM process.
So, to detect vulnerabilities on our Linux host we need to know what version of the packages contain vulnerabilities, which versions of packages are installed on our hosts, and learn how to compare versions.
How do I know which versions of packages are vulnerable?
Vulnerable versions of packages are listed in official security bulletins:
RHEL – https://access.redhat.com/errata/RHSA-2016:0304
CentOS – https://lists.centos.org/pipermail/centos-announce/2015-April/021064.html
Debian – http://www.debian.org/security/2015/dsa-3197
Ubuntu – http://www.ubuntu.com/usn/usn-2537-1/
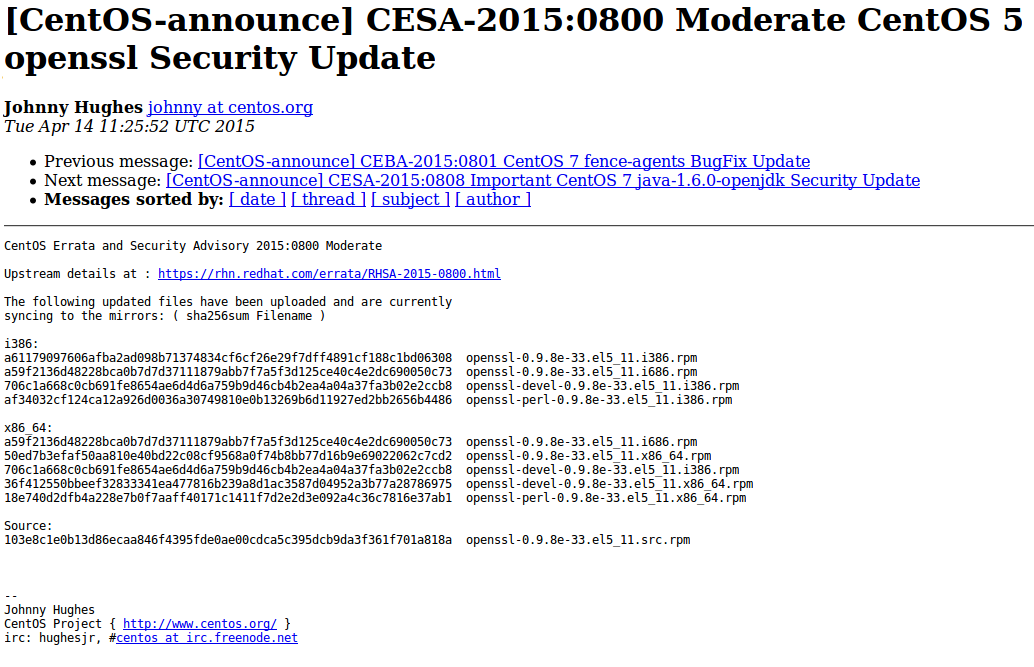
Of course, you will need to parse them first. Or you can just download the same content already parsed and presented in JSON format with Vulners.

Continue reading