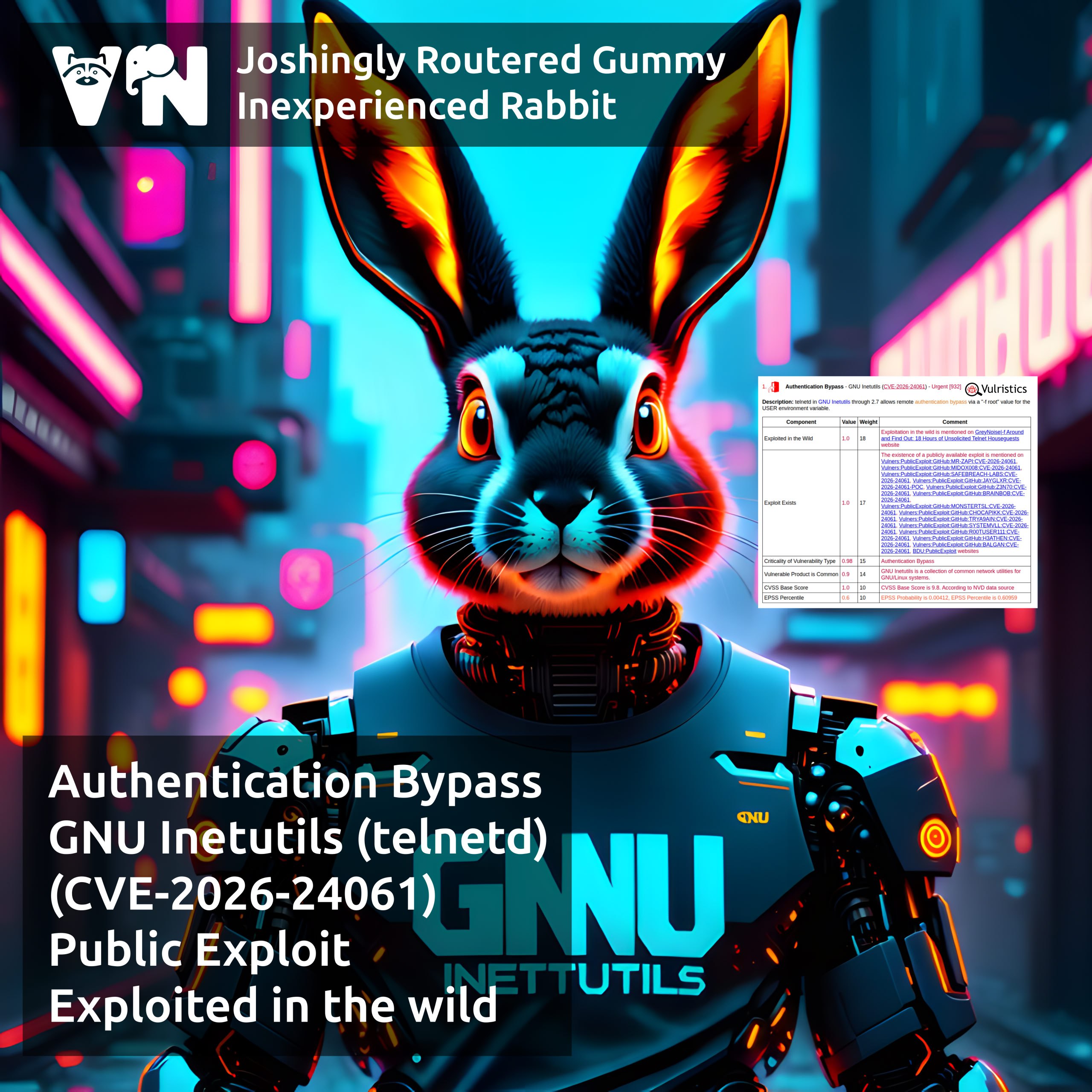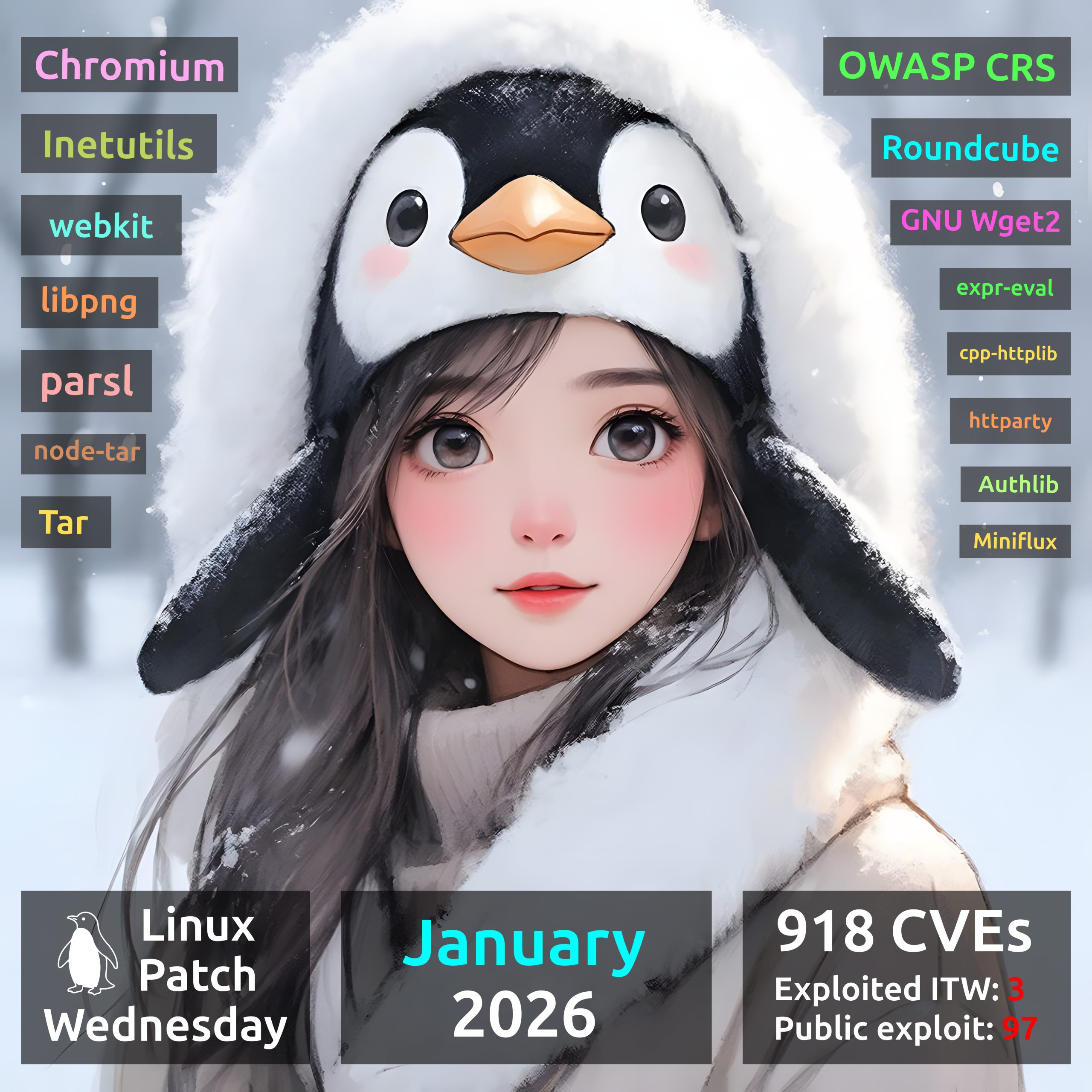
January Linux Patch Wednesday. In January, Linux vendors started fixing 918 vulnerabilities, one and a half times more than in December. Of these, 616 are in the Linux Kernel. Three show signs of exploitation in the wild:
🔻 AuthBypass – GNU Inetutils (telnetd) (CVE-2026-24061)
🔻 RCE – Safari (CVE-2025-43529); fixed in Linux distributions in webkit packages
🔻 MemCor – Chromium (CVE-2025-14174)
Another 97 vulnerabilities have public exploits or signs of their existence. Key examples:
🔸 MemCor – libpng (CVE-2026-22695)
🔸 XSS – Roundcube (CVE-2025-68461)
🔸 RCE – expr-eval (CVE-2025-13204)
🔸 ComInj – cpp-httplib (CVE-2026-21428), httparty (CVE-2025-68696), Miniflux (CVE-2026-21885)
🔸 SQLi – parsl (CVE-2026-21892)
🔸 SFB – OWASP CRS (CVE-2026-21876), Authlib (CVE-2025-68158)
🔸 AFW – node-tar (CVE-2026-23745)
🔸 PathTrav – GNU Wget2 (CVE-2025-69194), Tar (CVE-2025-45582)