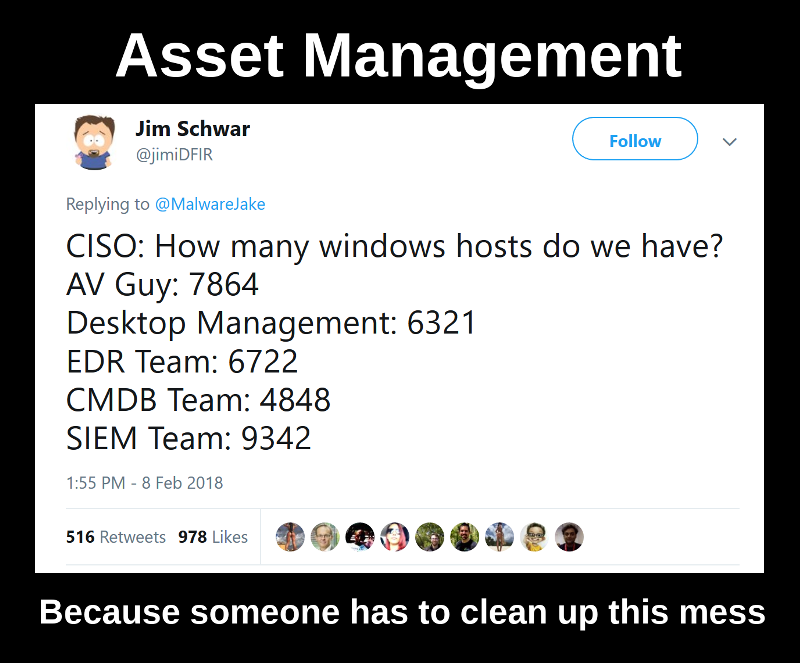
AM Live Vulnerability Management Conference 2022: my impressions and position. Hello everyone! This episode will be about the AM Live Vulnerability Management online conference. I participated in it on May 17th.
Alternative video link (for Russia): https://vk.com/video-149273431_456239090
The event lasted 2 hours. Repeating everything that has been said is difficult and makes little sense. Those who want can watch the full video or read the article about the event (both in Russian). Here I would like to share my impressions, compare this event with last year’s and express my position.