When people ask me how should they start building Vulnerability Management process in their organization (well, sometimes it happens), I advice them to create an effective Asset Management process first. Because it’s the foundation of the whole Infrastructure Security.
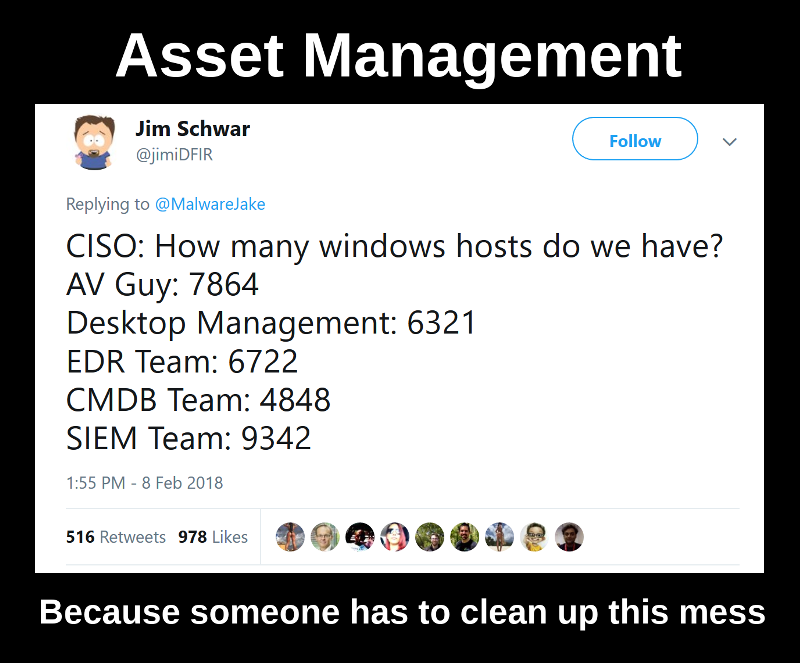
The term “Asset Management” has different meanings and if you start to google it, you will get some results related mainly to finance sphere. I use this term as Qualys and Tenable. For me Asset Management is the process of dealing with network hosts.
So, what should you do in situation described in the tweet above, when you don’t know exactly how many Windows hosts you have in your corporate IT environment? And, more importantly, why do you need to know?
Continue reading

