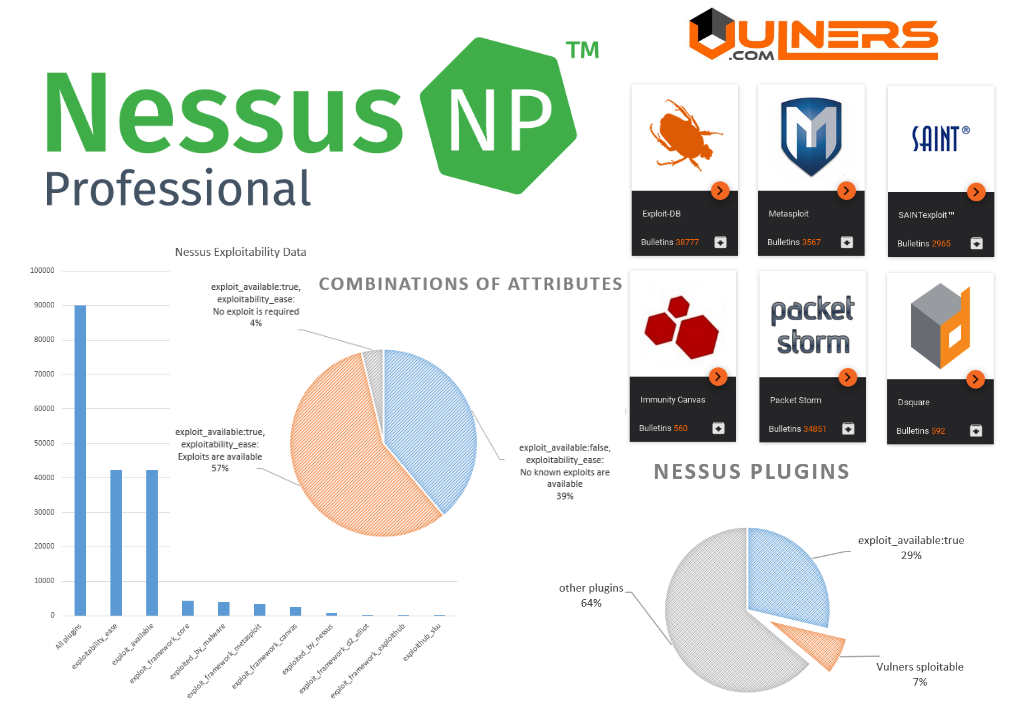
getsploit from Vulners.com. Kirill Isox Ermakov, the founder of Vulners, has recently presented a new open-source tool for searching and downloading exploits – getsploit.
Let’s say we want to pentest some WordPress blog. For example, this website avleonov.com. We can get WordPress version simply using curl:
$ curl -s https://avleonov.com | grep "generator"
<meta name="generator" content="WordPress 4.7.1" />
Ok, let’s get some sploits using this version:
$ sudo apt-get install git
$ git clone https://github.com/vulnersCom/getsploit
Cloning into 'getsploit'...
remote: Counting objects: 32, done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 32 (delta 13), reused 30 (delta 11), pack-reused 0
Unpacking objects: 100% (32/32), done.
Checking connectivity... done.
$ cd getsploit/
$ ./getsploit.py "title:WordPress AND title:4.7.1"
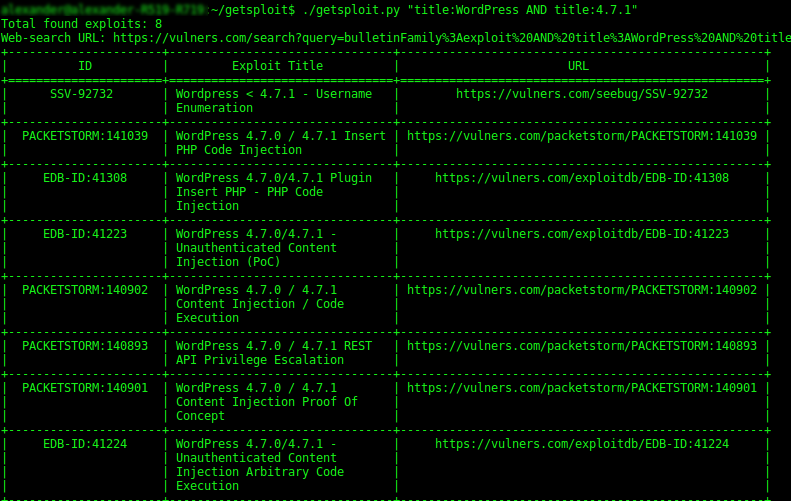
As you can see on the screen shot, getsploit makes a search request to vulners.com: bulletinFamily:exploit AND title:WordPress AND title:4.7.1 and matches objects in Immunity Canvas, DSquare Exploit Pack, Exploit-DB, Metasploit, Packet Storm, Malware exploit database, SAINTexploit™, seebug.org, Vulnerability Lab, 0day.today and Zero Science Lab.
Continue reading →