Psychological Aspects of Vulnerability Remediation. In my opinion, Remediation is the most difficult part of Vulnerability Management process. If you know the assets in your organization and can assess them, you will sooner or later produce a good enough flow of critical vulnerabilities. But what the point, if the IT team will not fix them?
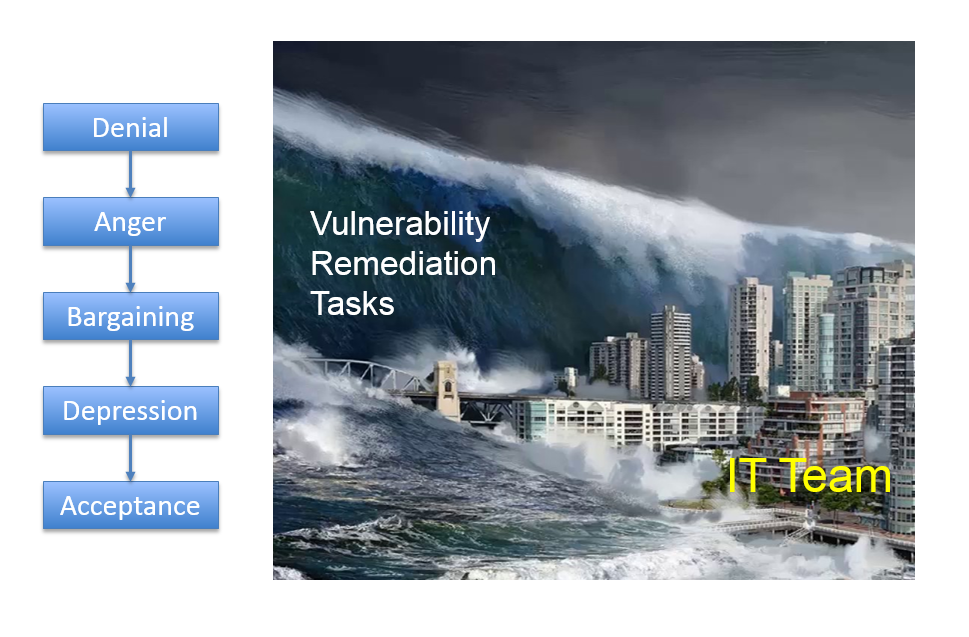
Kübler-Ross model and Tsunami of Vulnerability Remediation Tasks
Just think about it. The only thing that your colleagues from IT team see is an unexpected tsunami of the patching tasks. They most likely don’t understand WHY they should do it. They most likely don’t know about the concepts of Attack Surface minimization and Attack Cost maximization. From their point of view it’s just some stupid requirements from InfoSec team imposed with only one goal – to make their life miserable.
So, they may think that denial and pushing back can solve all their problems. And, frankly, this may work. There are countless ways to sabotage Vulnerability Remediation. Most main and common are the following:
- I don’t understand how to patch this.
- I already patched this, there should be a false positive in the scanner.
- Why should we patch this? The vulnerability is not exploitable. Or it is exploitable in theory, but not exploitable in our particular infrastructure. Or this server is not critical and, even if it will be compromised, there won’t be a huge impact. So, we will not patch it.
In each individual case Vulnerability Analyst can describe and proof his point, but doing this for each vulnerability will require insane amount of time and efforts and will paralyze the work. It is basically the Italian strike or work-to-rule.
