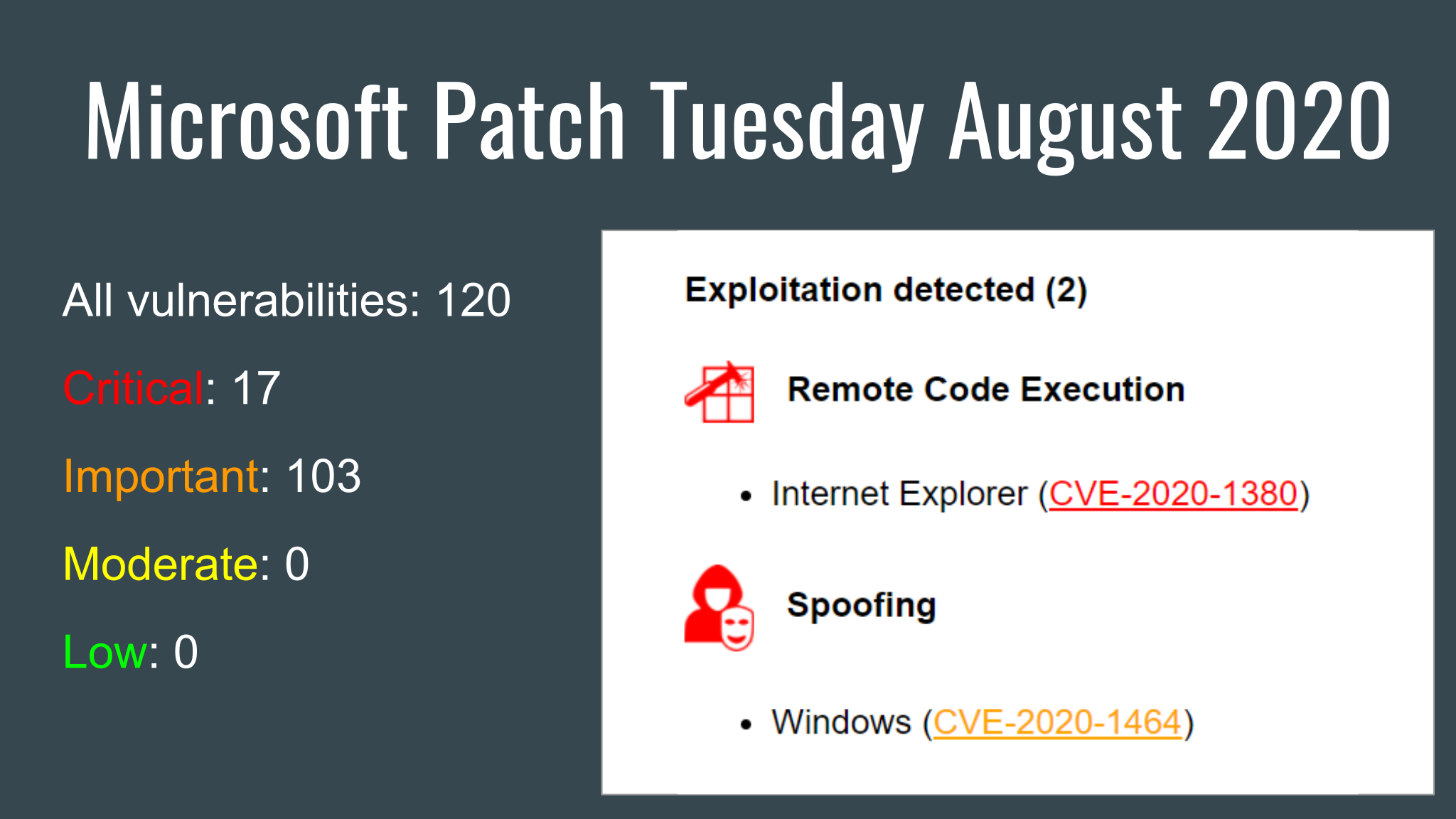
Microsoft Patch Tuesday March 2022. Hello everyone! I am glad to greet you from the most sanctioned country in the world. Despite all the difficulties, we carry on. I even have some time to release new episodes. This time it will be about Microsoft Patch Tuesday for March 2022.
Alternative video link (for Russia): https://vk.com/video-149273431_456239076
I do the analysis as usual with my open source tool Vulristics. You can still download it on github. I hope that github won’t block Russian repositories and accounts, but for now it looks possible. Most likely, I will just start hosting the sources of my projects on avleonov.com in this case. Or on another domain, if it gets even tougher. Stay tuned.