Qualys SSL Labs console client. Qualys SSL Labs is a free online service, which performs a deep analysis of web server SSL configuration and detects some common OpenSSL vulnerabilities either (e.g. Heartbleed).
This service has an API and official console client, that could be used to automate security assessment.
Client was written in Go. To build it in Ubuntu you need to install golang package first.
$ sudo apt-get install golang
The project of Qualys SSL Labs client is hosted on https://github.com/ssllabs/ssllabs-scan. Getting the sources…
$ wget https://github.com/ssllabs/ssllabs-scan/archive/stable.zip
$ unzip stable.zip
$ cd ssllabs-scan-stable/$ ls
AUTHORS LICENSE Makefile pulse.sql README.md ssllabs-api-docs.md ssllabs-scan.go TODO
Building ssllabs-scan binary:
$ go build ssllabs-scan.go
$ ls
AUTHORS LICENSE Makefile pulse.sql README.md ssllabs-api-docs.md ssllabs-scan ssllabs-scan.go TODO
The tool is easy to use. You just need to specify hostname or name of file with hosts.
Here is extract from README.md file:
SYNOPSIS
“`
ssllabs-scan [options] hostname
ssllabs-scan [options] –hostfile file
“`
[…]OPTIONS
| Option | Default value | Description |
| ———– | ————- | ———– |
| –api | BUILTIN | API entry point, for example https://www.example.com/api/ |
| –verbosity | info | Configure log verbosity: error, info, debug, or trace |
| –quiet | false | Disable status messages (logging) |
| –ignore-mismatch | false | Proceed with assessments on certificate mismatch |
| –json-flat | false | Output results in flattened JSON format |
| –hostfile | none | File containing hosts to scan (one per line) |
| –usecache | false | If true, accept cached results (if available), else force live scan |
| –grade | false | Output only the hostname: grade |
| –hostcheck | false | If true, host resolution failure will result in a fatal error |
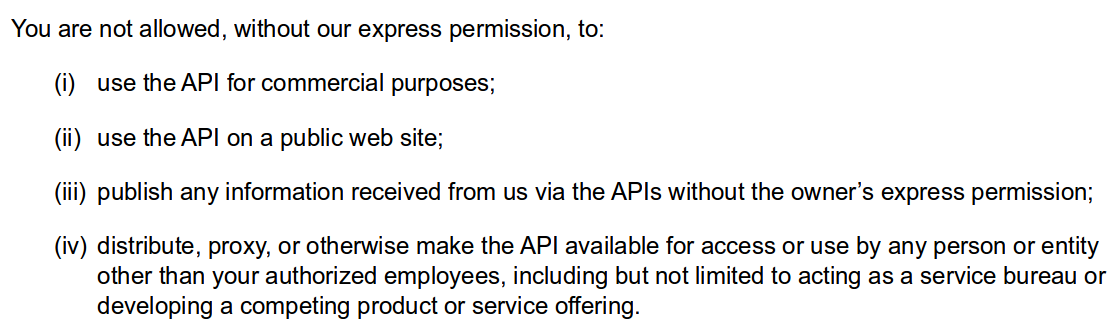
Before using the tool, read terms and conditions: https://www.ssllabs.com/about/terms.html. Especially this part:
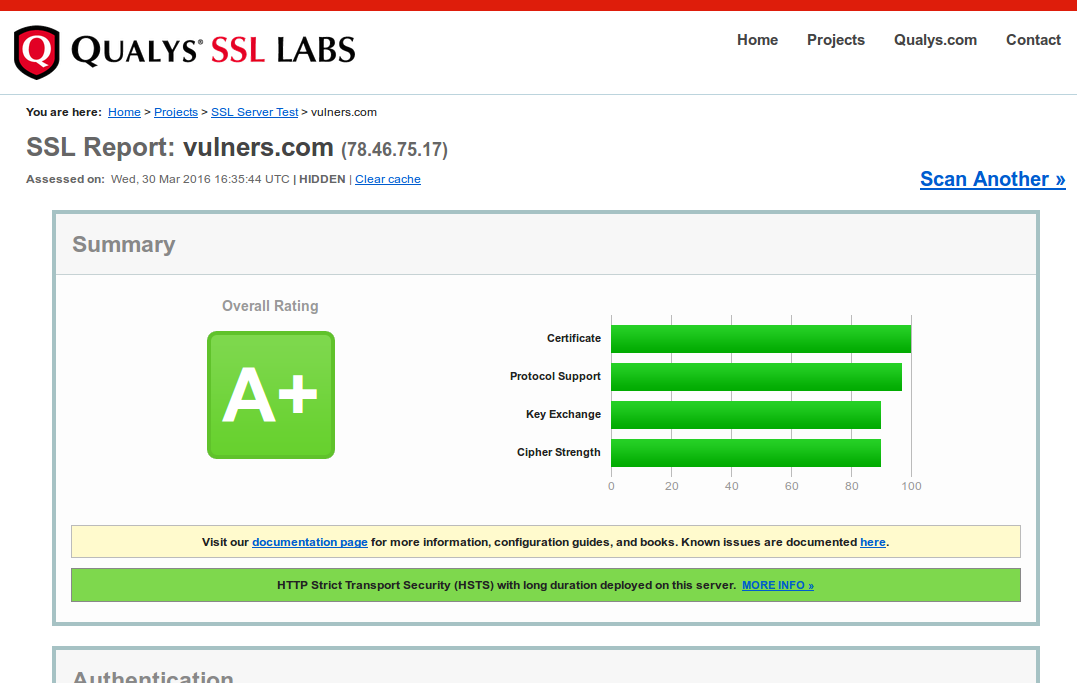
Website assessment takes approximately 1-2 minutes. Scan results are in json format. The most interesting parameters you could use are Overall Rating (grade) and timestamp when certificate will be expired.
[
{
“host”: “https://vulners.com”,
“port”: 443,
“protocol”: “HTTP”,
“isPublic”: false,
“status”: “READY”,
“startTime”: 1459356671987,
“testTime”: 1459356784609,
“engineVersion”: “1.22.37”,
“criteriaVersion”: “2009l”,
“endpoints”: [
{
“ipAddress”: “78.46.75.17”,
“serverName”: “static.17.75.46.78.clients.your-server.de”,
“statusMessage”: “Ready”,
“grade”: “A+”,
“gradeTrustIgnored”: “A+”,
“hasWarnings”: false,
“isExceptional”: true,
“progress”: 100,
“duration”: 112176,
“eta”: 1,
“delegation”: 1,
“details”: {
“hostStartTime”: 1459356671987,
“key”: {
“size”: 2048,
“alg”: “RSA”,
“debianFlaw”: false,
“strength”: 2048
},
“cert”: {
“subject”: “CN\u003d*.vulners.com,OU\u003dEssentialSSL Wildcard,OU\u003dDomain Control Validated”,
“commonNames”: [
“*.vulners.com”
],
“altNames”: [
“*.vulners.com”,
“vulners.com”
],
“notBefore”: 1437004800000,
“notAfter”: 1468627199000,[…]
As you see, a very simple and effective tool. And it’s free. You can also read my review of competing service — High-Tech Bridge SSL Server Test (with Free API).

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: High-Tech Bridge service and API for SSL/TLS server testing | Alexander V. Leonov
Pingback: When a free scanning service detects vulnerabilities better | Alexander V. Leonov
Pingback: Qualys Vulnerability Management GUI and API | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Qualys new look and new products | Alexander V. Leonov