Exploitability attributes of Nessus plugins: good, bad and Vulners. Exploitability is one of the most important criteria for prioritizing vulnerabilities. Let’s see how good is the exploit-related data of Tenable Nessus NASL plugins and whether we can do it better.
What are the attributes related to exploits? To understand this, I parsed all nasl plugins and got the following results.
script_set_attribute(attribute:"cpe", value:"cpe:/a:malwarebytes:malwarebytes_anti-exploit"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"exploit_framework_exploithub", value:"true"); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"exploited_by_nessus", value:"true"); script_set_attribute(attribute:"exploithub_sku", value:"EH-10-031"); script_set_attribute(attribute:"exploithub_sku", value:"EH-11-053"); ... script_set_attribute(attribute:"exploithub_sku", value:"EH-14-757");
This is what you can expect to see in the scan results.
Some attributes indicate the existence of exploit:
- exploit_available
- exploitability_ease
Some attributes indicate the possibility of practical use of the exploit (only available value is “yes”):
- exploited_by_malware
- exploited_by_nessus
Some attributes indicate that there is an exploit in some well-known exploit framework (only available value is “yes”):
- exploit_framework_canvas
- exploit_framework_core
- exploit_framework_exploithub
- exploit_framework_metasploit
And some specific references to exploits (exploithub is already a closed project, so it’s not so interesting):
- exploithub_sku
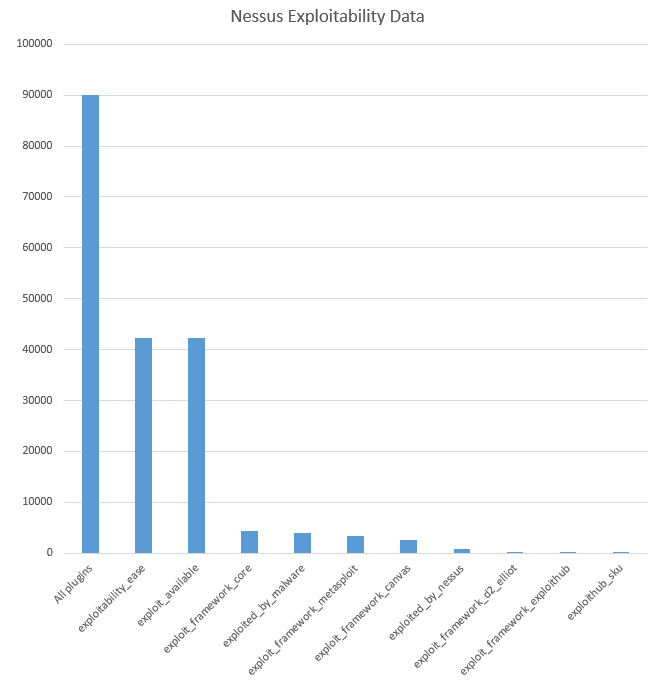
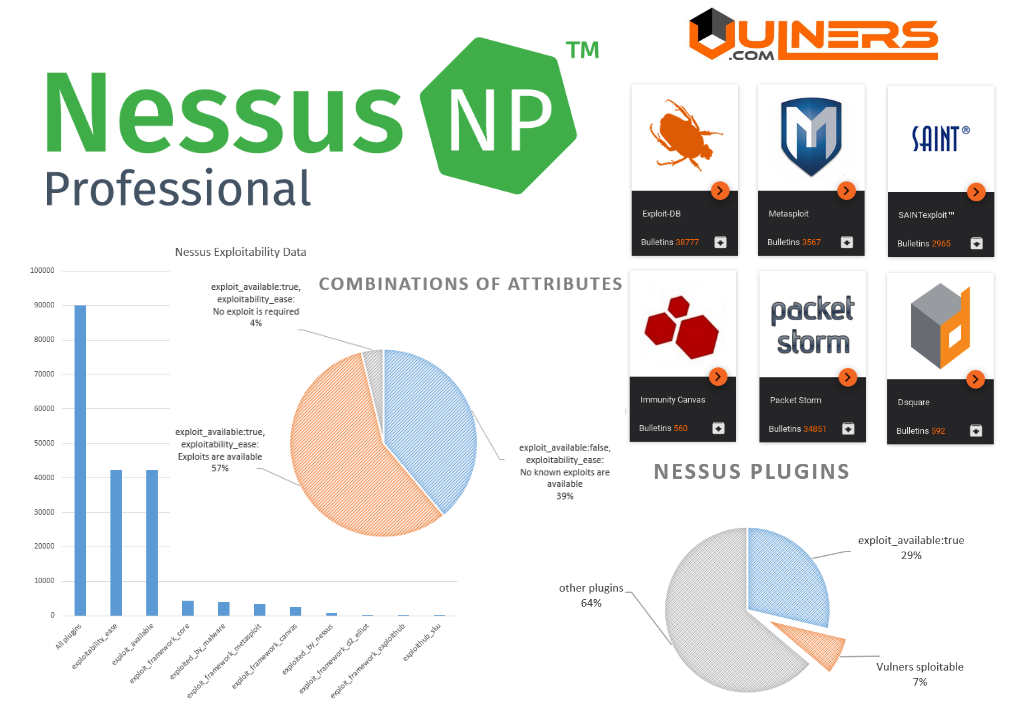
| All plugins | 90115 |
| exploitability_ease | 42267 |
| exploit_available | 42267 |
| exploit_framework_core | 4360 |
| exploited_by_malware | 4072 |
| exploit_framework_metasploit | 3469 |
| exploit_framework_canvas | 2544 |
| exploited_by_nessus | 873 |
| exploit_framework_d2_elliot | 327 |
| exploit_framework_exploithub | 166 |
| exploithub_sku | 166 |
Good
Wherever there is an exploitability_ease attribute, there will also be an exploit_available attribute. It is awesome. Let’s see what combinations of exploitability_ease and exploit_available can be.
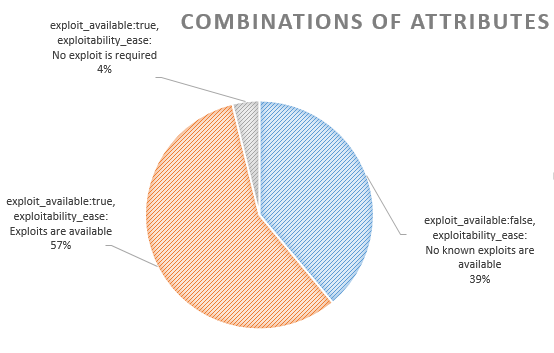
| exploit_available:false, exploitability_ease: No known exploits are available |
16453 |
| exploit_available:true, exploitability_ease: Exploits are available |
24205 |
| exploit_available:true, exploitability_ease: No exploit is required |
1609 |
So, if you want to get vulnerabilities with exploits, you can search for exploit_available == true and exploitability_ease attribute is not really necessary.
Bad
Now let’s see if exploitability_ease/exploit_available attributes are set in every plugin where additional exploitability attribute (exploit_framework_core, exploited_by_malware, exploit_framework_metasploit, etc.) set.
This is true for all attributes except exploited_by_nessus. There are 63 plug-ins (!) in which there is only exploited_by_nessus and no exploitability_ease/exploit_available.
Examples of such plugins:
BOOTPARAMD_GET_NIS_DOMAIN.NASL
SVN_IN_WWW.NASL
ORION_EXAMPLES_XSS.NASL
PHP_EXPOSE_PHP.NASL
GRANDSTREAM_GET_PASSWORD.NASL
TRAPEZE_ADMIN_ACCESSIBLE.NASL
PLIGG_REG_USERNAME_XSS.NASL
JRUN.NASL
OSCOMMERCE_ADMIN_ACCESS.NASL
MONGODB_AUTHENTICATION_DISABLED.NASL
…
Among them there are quite interesting this year plugins, for example “Belkin N750 Router Command Injection (BELKIN_TWONKY_PROXY_CMD_INJECTION.NASL)”
So, be careful while filtering vulnerabilities. Don’t miss this “exploited_by_nessus” plugins.
Vulners
And finally the most interesting part, let’s look at Nessus plugins for which there are no attribute exploit_available at all, or exploit_available == false and try to find exploits for them. I’ve used this exploit data collections from vulners.com (“canvas”, “dsquare”, “metasploit”, “packetstorm”, “saint”, “exploitdb”):

If some particularTenable Nessus plugin and some Exploit have a link to the same CVE, that mean that they are somehow related, right? It’s not a rocket science, however this method gives pretty good results. I have found exploits for around 6000 Nessus plugins, for which Tenable gives no information on exploitability. That means more critical vulnerabilities will pass prioritization filter.
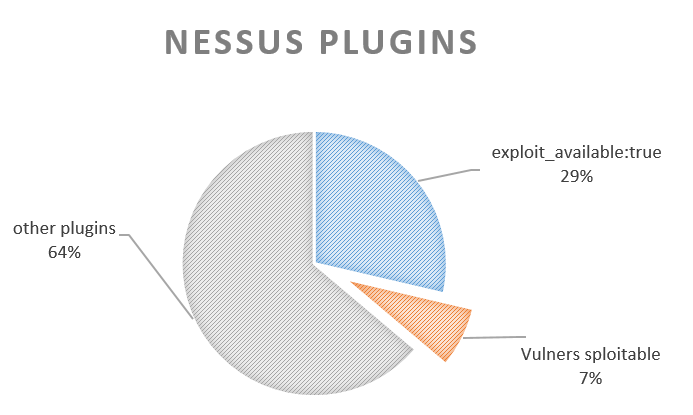
| exploit_available:true | 25814 |
| Vulners sploitable | 6764 |
| other plugins | 57537 |
Some examples:
…
—
UBUNTU_USN-618-1.NASL
set([u’EDB-ID:30605′])
—
MANDRAKE_MDKSA-2006-053.NASL
set([u’EDB-ID:1557′])
—
MOZILLA_THUNDERBIRD_20023.NASL
set([u’EDB-ID:33128′])
—
DEBIAN_DLA-982.NASL
set([u’PACKETSTORM:143369′])
—
MANDRIVA_MDVSA-2014-056.NASL
set([u’EDB-ID:31615′, u’MSF:AUXILIARY/DOS/HTTP/APACHE_COMMONS_FILEUPLOAD_DOS’])
—
FEDORA_2012-9442.NASL
set([u’EDB-ID:37306′])
—
FREEBSD_PKG_B2A6FC0E070F11E0A6E900215C6A37BB.NASL
set([u’EDB-ID:15431′, u’PACKETSTORM:95574′])
—
SUSE_11_KERNEL-120418.NASL
set([u’EDB-ID:35403′])
—
CISCO-SA-20140605-OPENSSL-IOS.NASL
set([u’MSF:AUXILIARY/SCANNER/SSL/OPENSSL_CCS’])
—
CISCO-SA-20140605-OPENSSL-IOS.NASL
set([u’MSF:AUXILIARY/DOS/SSL/DTLS_FRAGMENT_OVERFLOW’])
—
SUSE_11_NTP-140721.NASL
set([u’MSF:AUXILIARY/SCANNER/NTP/NTP_READVAR’, u’MSF:AUXILIARY/SCANNER/NTP/NTP_PEER_LIST_SUM_DOS’, u’MSF:AUXILIARY/SCANNER/PORTMAP/PORTMAP_AMP’, u’MSF:AUXILIARY/SCANNER/NTP/NTP_UNSETTRAP_DOS’, u’MSF:AUXILIARY/SCANNER/NTP/NTP_MONLIST’, u’MSF:AUXILIARY/SCANNER/UDP/UDP_AMPLIFICATION’, u’MSF:AUXILIARY/SCANNER/UPNP/SSDP_AMP’, u’EDB-ID:33073′, u’PACKETSTORM:127492′, u’MSF:AUXILIARY/SCANNER/NTP/NTP_REQ_NONCE_DOS’, u’MSF:AUXILIARY/SCANNER/NTP/NTP_PEER_LIST_DOS’, u’MSF:AUXILIARY/SCANNER/NTP/NTP_RESLIST_DOS’])
—…
Let’s see an example that there are no exploitability attributes in Nessus plugin for vulnerability that pretty sure is exploitable.
Cisco IOS Cluster Management Protocol Telnet Option Handling RCE (cisco-sa-20170317-cmp)
Note that there is a link to RCE exploit in Packet Storm:
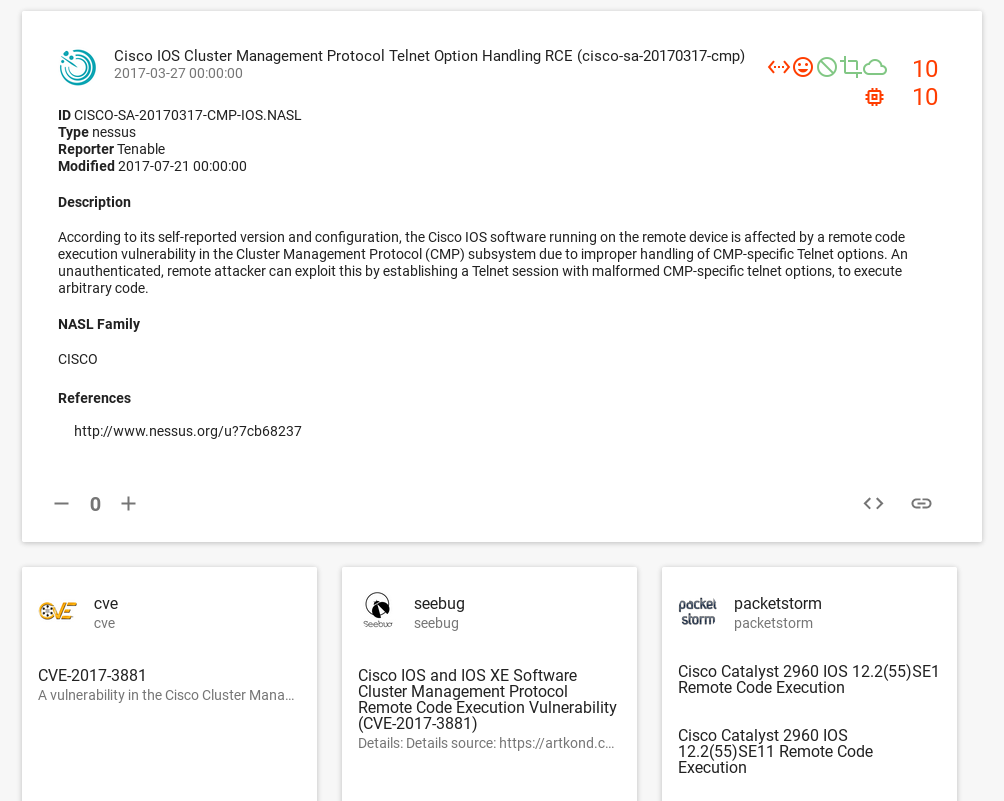
And here is a part of Nessus plugin code:
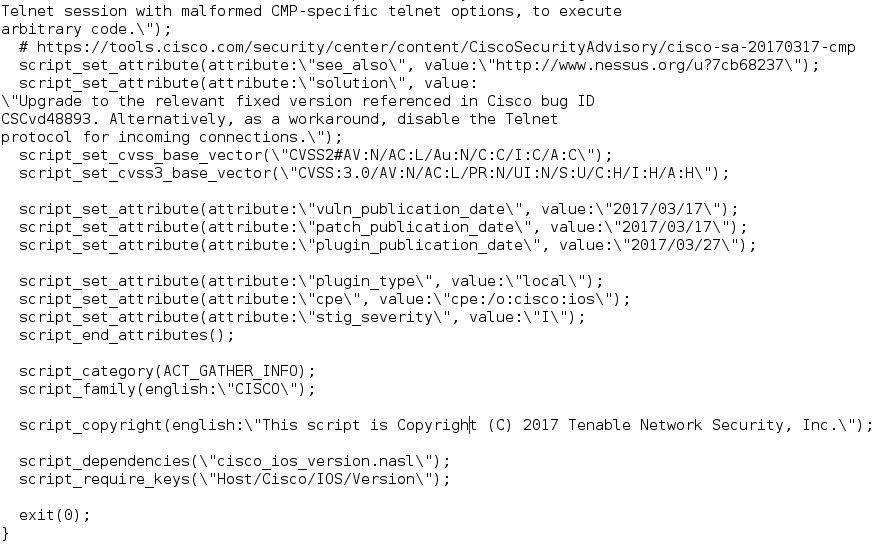
As you can see, no exploitability_ease/exploit_available attributes. And this is pretty strange.
Thus, the use of external exploit databases can greatly help with the search of exploitable vulnerabilities detected by Nessus.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Kenna Security: Analyzing Vulnerability Scan data | Alexander V. Leonov
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov
Pingback: CISO Forum and the problems of Vulnerability Databases | Alexander V. Leonov
Pingback: What’s wrong with patch-based Vulnerability Management checks? | Alexander V. Leonov
Pingback: PHDays 9: new methods of Vulnerability Prioritization in Vulnerability Management products | Alexander V. Leonov