First look at Tenable.io Web Application Scanner (WAS). When Tenable firstly announced Web Application Security scanner as a part of their new Tenable.io platform, it was quite intriguing. Certainly, they already had some WAS functionality before in Nessus. For example, path traversal check was pretty good. But this functionality was quite fragmental and barely manageable. How Tenable now write in their docs: “Nessus is incompatible with modern web applications that rely on Javascript and are built on HTML5”.

That’s why Nessus couldn’t be called fully functioning Web Application Scanning solution. However, Tenable.io WAS is a completely new story. The full description is available on official site. Here I will make a very fast review and give some comments.
Trial Request
I used a trial version. You can use it for free for 60 days. Trial registration is fully automatic, just fill the form and choose “Try Tenable.io Web Application Scanning”. You can create trial in various locations: US, UK, Germany, Singapore and Australia. Than check your inbox to verify your email address and set the password.
The evaluation version contains three products:
- Container Security
- Vulnerability Management
- Web Application Scanning
Next you will need to accept Tenable.io License Agreement and GDPR alignment. And that’s it.
Tenable.io GUI
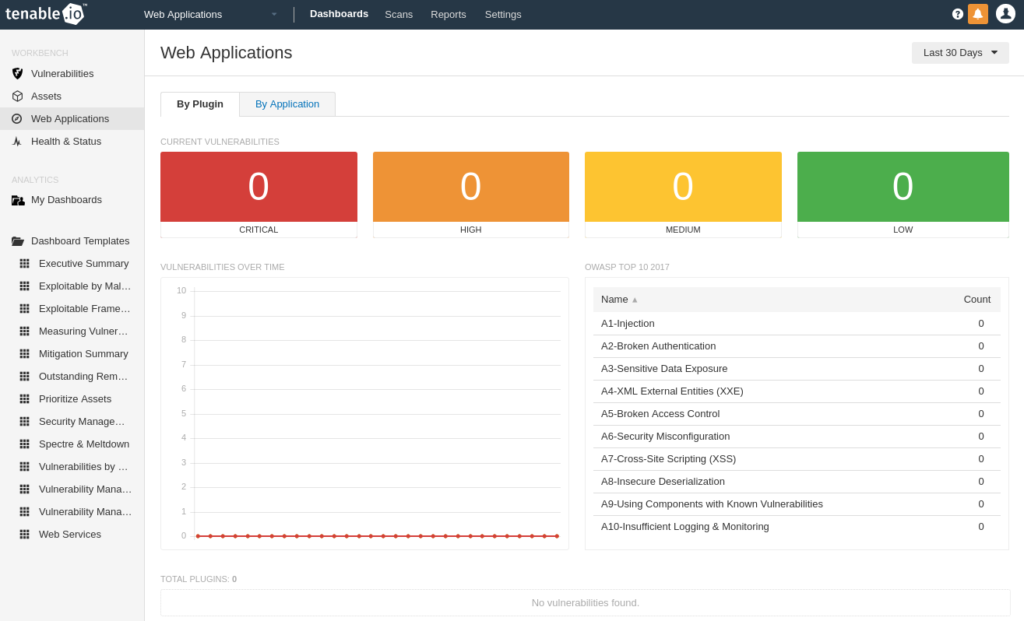
Just like in Tenable.io VM, the main page in Tenable.io WAS contains a dashboard with statistics on vulnerability severity, types of vulnerabilities and vulnerability dynamics.
Web App Scan policy
The WAS is now integrated in familiar Nessus-like interface of Tenable.io. Basically, it’s no more than a specific scan profile.
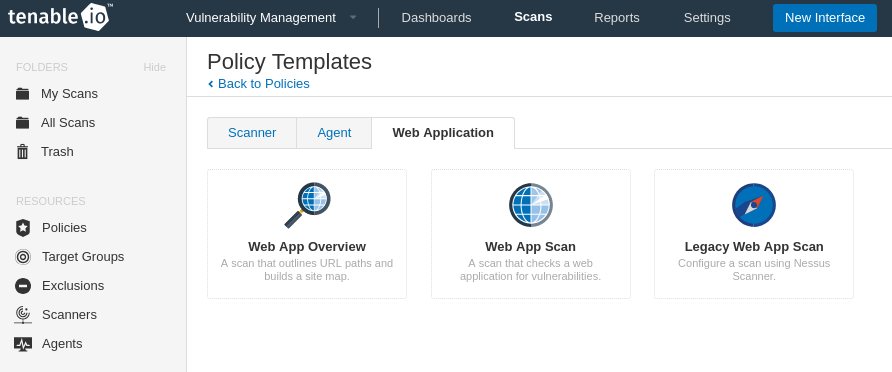
It seems like custom profiles are now the main way for adding new functionality in Tenable scanning products. Check this profile with dynamic plugin sets. I really like this, it creates great and holistic user experience.
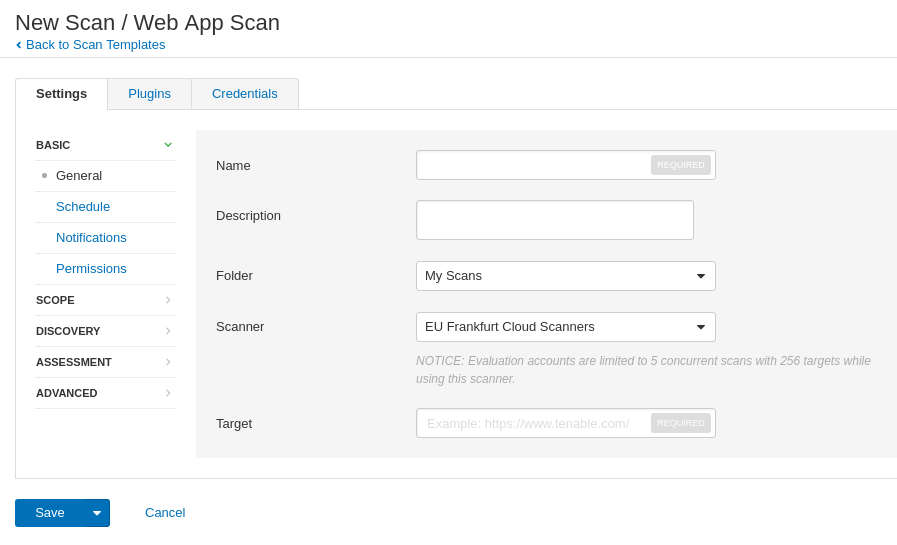
New Web App Scan
Here is how Web App Scan looks like. You can choose name, target, folder for the scan an Scanner location (Frankfurt, Singapore and US).
Plugins
It’s awesome, that Tenable IO WAS allows to see the plugins that will be executed during the scan and enable/disable them. Just like Nessus. Most of the plugins (528) are version-based checks. You can search them by id on the Tenable plugins site, for example AngularJS 1.3.0 < 1.5.0-rc.2 Cross-site Scripting.
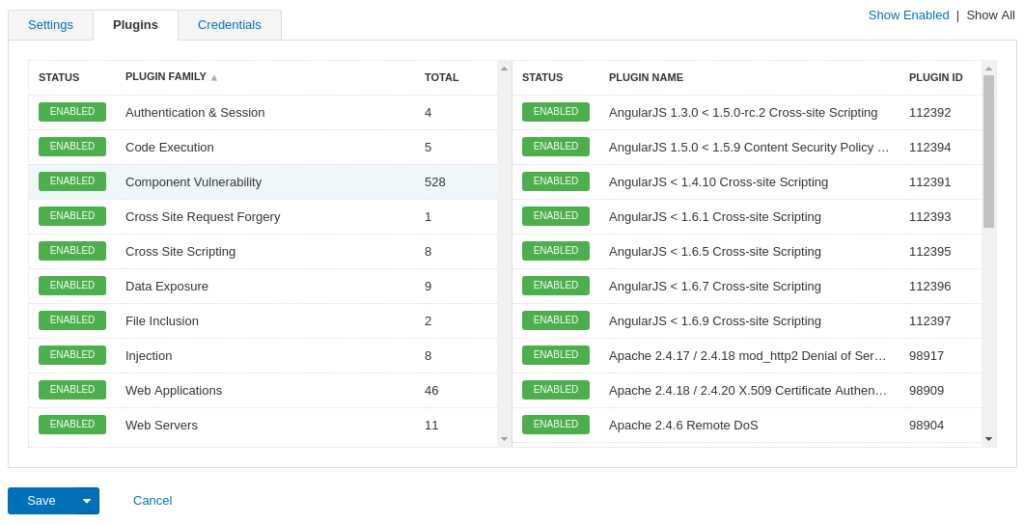
Credentials
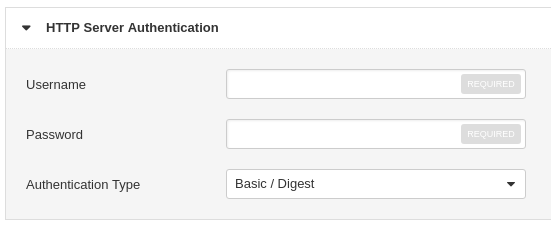
For HTTP Server you can set Basic/Digest or NTLM authentication:
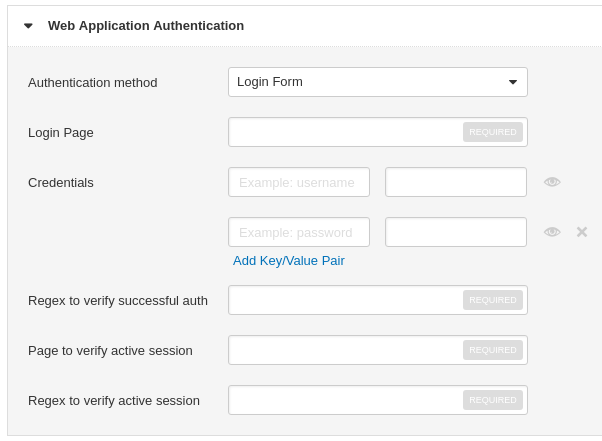
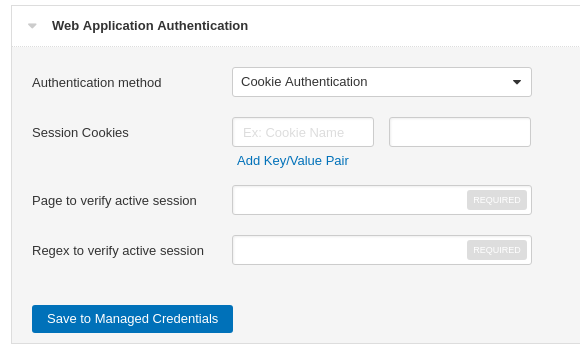
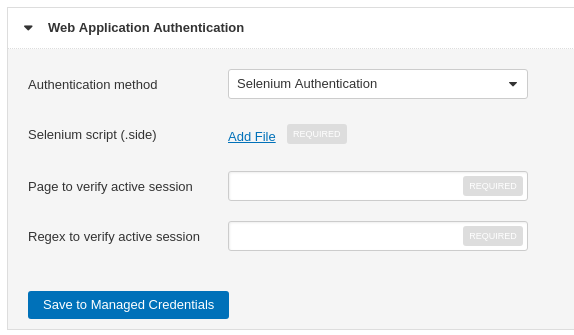
For Web Application it’s trickier. Tenable.io WAS now supports 3 authentication methods: Login Form, Cookie and Selenium. All of them have mandatory fields “Page to verify active session” and “Regex to verify active session”. It’s the way how Tenable IO WAS understand that the session is still active. Pretty simple and reliable. For the Login Form there is also a regex to verify that the authentication operation was successful.
Login Form:
Cookie:
Selenium:
Other Settings
What else can we edit in Settings? Like with the Nessus scan, there is the ability to schedule scan, set notifications and permissions. Besides that:
- In Scope you can set URLs that should be included and excluded from the scan. You can exclude them by regex or file extension. Here you can also limit crawling: only specified URLs or specified URLs with child paths.
- In Discovery you can set Crawl Selenium Scripts.
- In Assessment you can choose elements that you want to Assess (cookies, forms, headers, links, parameter names, parameter values, JSON, XML, UI Forms, UI Inputs) or preset from this elements (Quick or Extensive).
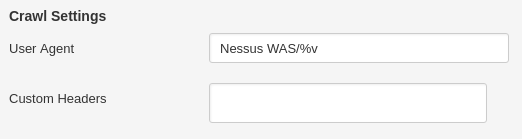
- In Advanced you can set various time limits (Overall Scan time, various timeouts) and limits on number of operations (number of request, connections, URLs, depth etc.). Note that in Discovery sub-tab you can set custom User Agent and Header, that could be used for giving access to the application and filtering scanner activity.
Scan Results
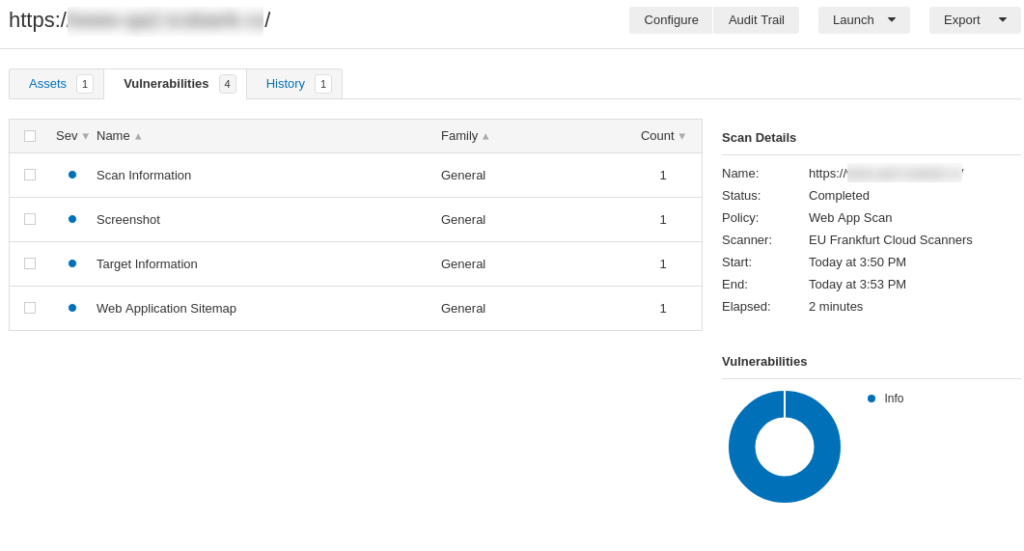
Result of the scan looks pretty much like in Nessus:
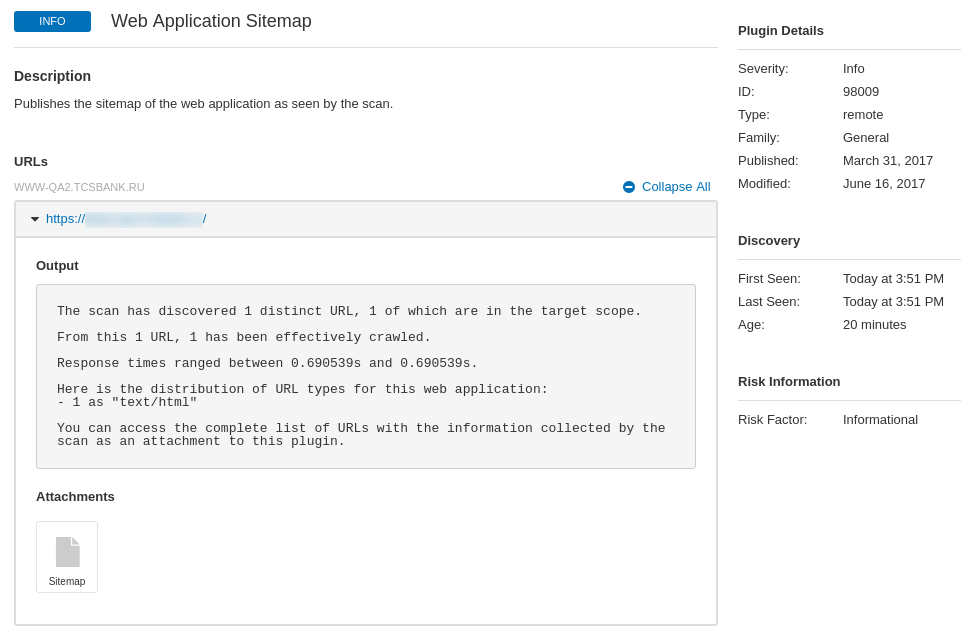
Plugin output is combined by URLs and contains text output and attached files with the details:
In conclusion
The scanner looks great. I liked that they use Selenium for authentication and crawling. The only thing that I found confusing is authentication management in Credentials. It requires specifying URLs & regexs or script. It would be nice to debug these settings directly in the application settings interface, like in Nexpose VM. I’ll not write anything about the scan quality yet, it takes more time for testing.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Hi Alexander,
Just to make you aware, last month we released our chrome extension to make the selenium authentication process easier for our customers.
You can try it out from the Chrome Web Store here: https://chrome.google.com/webstore/detail/tenableio-web-application/nkmmlnphajhildmnjkjkgkjnggpnhkhk
Kind Regards,
Fergus Cooney
Pingback: Tenable IO WAS Chrome Extension | Alexander V. Leonov
Thank you for this valuable write-up. Look forward to reading your scan quality findings!
Hello Alexander,
Did you complete the Tenable WAS testing – it would be interesting to hear your thoughts an findings.
Thanks!
I have a web application in which I have Login Parameteres -> CSRF token + username +password
How do I pass the csrf token in nessus while doing web app scan?
Because the tool is implementing a dynamic testing method, it cannot cover 100% of the source code of the application and then, the application itself. The penetration tester should look at the coverage of the web application or of its attack surface to know if the tool was configured correctly or was able to understand the web application.