Microsoft Patch Tuesday January 2023: ALPC EoP, Win Backup EoP, LocalPotato, Exchange, Remote RCEs. Hello everyone! This episode will be about Microsoft Patch Tuesday for January 2023, including vulnerabilities that were added between December and January Patch Tuesdays.
Alternative video link (for Russia): https://vk.com/video-149273431_456239115
As usual, I use my open source Vulristics project to analyse and prioritize vulnerabilities. I took the comments about the vulnerabilities from the Qualys, Nessus, Rapid7 and ZDI Patch Tuesday reviews.
$ cat comments_links.txt
Qualys|The January 2023 Patch Tuesday Security Update Review|https://blog.qualys.com/vulnerabilities-threat-research/patch-tuesday/2023/01/10/the-january-2023-patch-tuesday-security-update-review
ZDI|THE JANUARY 2023 SECURITY UPDATE REVIEW|https://www.zerodayinitiative.com/blog/2023/1/10/the-january-2023-security-update-review
$ python3.8 process_classify_ms_products.py # Automated classifier for Microsoft products
$ python3.8 vulristics.py --report-type "ms_patch_tuesday_extended" --mspt-year 2023 --mspt-month "January" --mspt-comments-links-path "comments_links.txt" --rewrite-flag "True"
...
Creating Patch Tuesday profile...
MS PT Year: 2023
MS PT Month: January
MS PT Date: 2023-01-10
MS PT CVEs found: 98
Ext MS PT Date from: 2022-12-14
Ext MS PT Date to: 2023-01-09
Ext MS PT CVEs found: 5
ALL MS PT CVEs: 103
Qualys query: January 2023 Patch Tuesday
...- All vulnerabilities: 103
- Urgent: 0
- Critical: 1
- High: 44
- Medium: 58
- Low: 0
This time there was one vulnerability with a sign of exploitation in the wild:
Elevation of Privilege – Windows Advanced Local Procedure Call (ALPC) (CVE-2023-21674). The vulnerability exists in the Advanced Local Procedure Call (ALPC) functionality. ALPC is a message passing utility in Windows operating systems. When exploited, an attacker can leverage the vulnerability to break out of the sandbox in Chromium and gain kernel-level execution privileges. Exploitation in the wild is mentioned on Vulners (cisa_kev object), AttackerKB, Microsoft websites. The existence of the exploit is mentioned in Microsoft CVSS Temporal Score (Functional Exploit).
For one more vulnerability, there is a public exploit on GitHub:
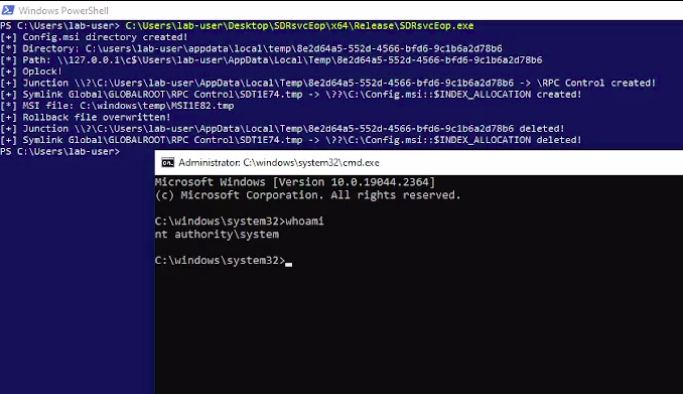
Elevation of Privilege – Windows Backup Service (CVE-2023-21752). Not much is known about this vulnerability. According to Microsoft’s description, an attacker who successfully exploited this vulnerability could gain SYSTEM privileges. This vulnerability does not allow disclosure of any confidential information, but could allow an attacker to delete data that could include data that results in the service being unavailable. This vulnerability was not highlighted in any of the reviews released by VM vendors. However, on January 11, a well-known researcher Filip Dragovic Wh04m1001 released two public PoCs on GitHub. The first PoC can delete any file, the second one launches a shell with elevated privileges.
For one more vulnerability, there is no public exploit yet, but the researchers promise to publish it within 30 days:
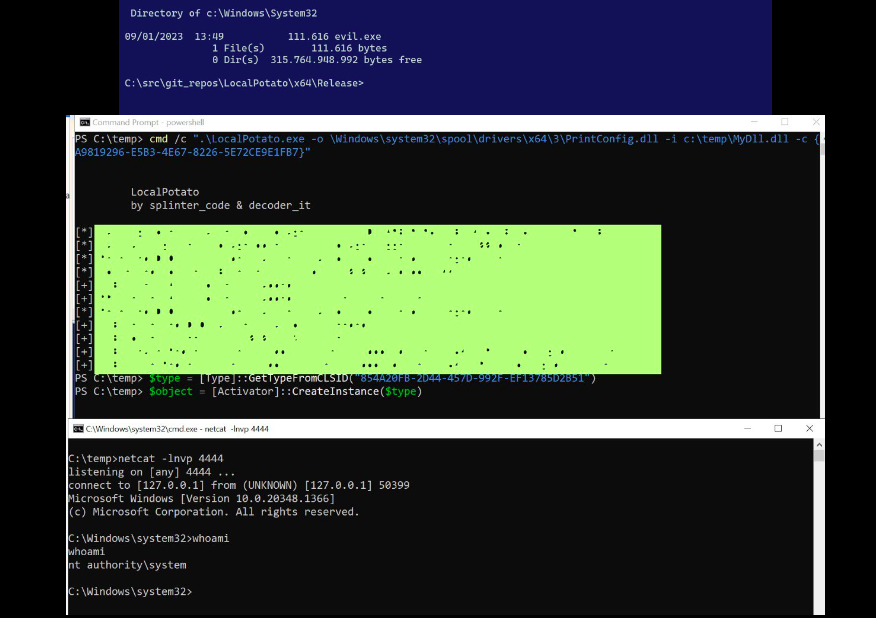
Elevation of Privilege – Windows NTLM (CVE-2023-21746). Successful exploitation would allow an attacker to gain SYSTEM privileges. The vulnerability was disclosed by Andrea Pierini with Semperis and Antonio Cocomazzi with Sentinel One. They named it LocalPotato and created site for it. So it is likely that the PoC will be publicly available pretty soon.
Now let’s talk about other vulnerabilities for which there are no public exploits and signs of exploitation in the wild. It makes sense to pay attention to the following:
- Elevation of Privilege – Microsoft Exchange (CVE-2023-21763, CVE-2023-21764). This vulnerability arises from failing to patch a previously identified issue, designated as CVE-2022-41123 (November Patch Tuesday). Thanks to the use of a hard-coded path, a local attacker could load their own DLL and execute code at the level of SYSTEM. With Exchange, you can never say that a vulnerability will not be used in a dangerous attack (like ProxyShell or ProxyNotShell), it is better to carefully fix all Exchange vulnerabilities This also applies to Information Disclosure – Microsoft Exchange (CVE-2023-21761) and Spoofing – Microsoft Exchange (CVE-2023-21745).
- Remote Code Execution in various protocols Windows Lightweight Directory Access Protocol (LDAP) (CVE-2023-21676), Windows Authentication (CVE-2023-21539), Windows Layer 2 Tunneling Protocol (L2TP) ( 5 CVEs: CVE-2023-21679, CVE-2023-21546, CVE-2023-21555, CVE-2023-21556, CVE-2023-21543), Windows Secure Socket Tunneling Protocol (SSTP) (CVE-2023-21535, CVE-2023-21548). All vulnerabilities with network access vector. Little is known about these vulnerabilities. But if any of these vulnerabilities turn out to be exploitable, it could be very serious.
Also I would like to mention that Windows 8.1 reached end of support on January 10, 2023, at which point technical assistance and software updates will no longer be provided. Also after 10 years of support and 3 additional years extended support, Windows Server 2008/2008R2 Extended Security Updates (ESUs) program has ended. As well as Windows 7 Extended Security Updates program. A good reason to check your infrastructure for such legacy hosts and try to get rid of them.
Full Vulristics report: ms_patch_tuesday_january2023

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
