
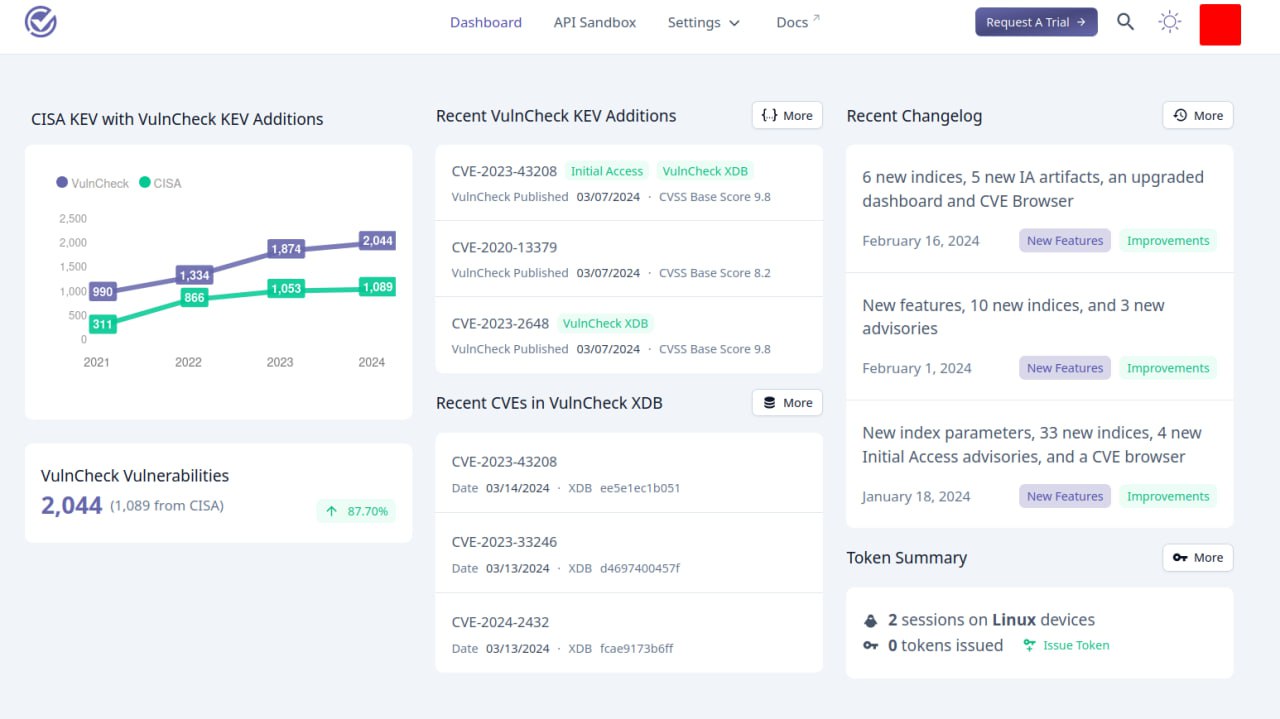
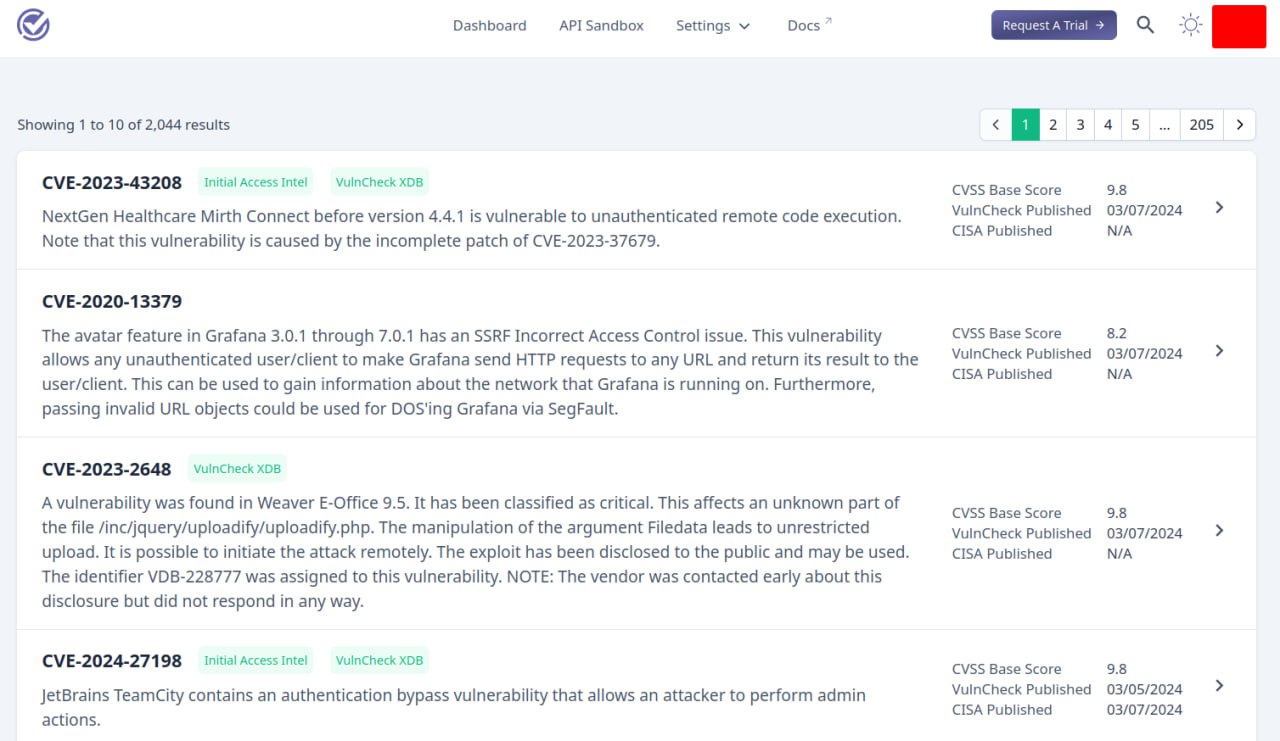
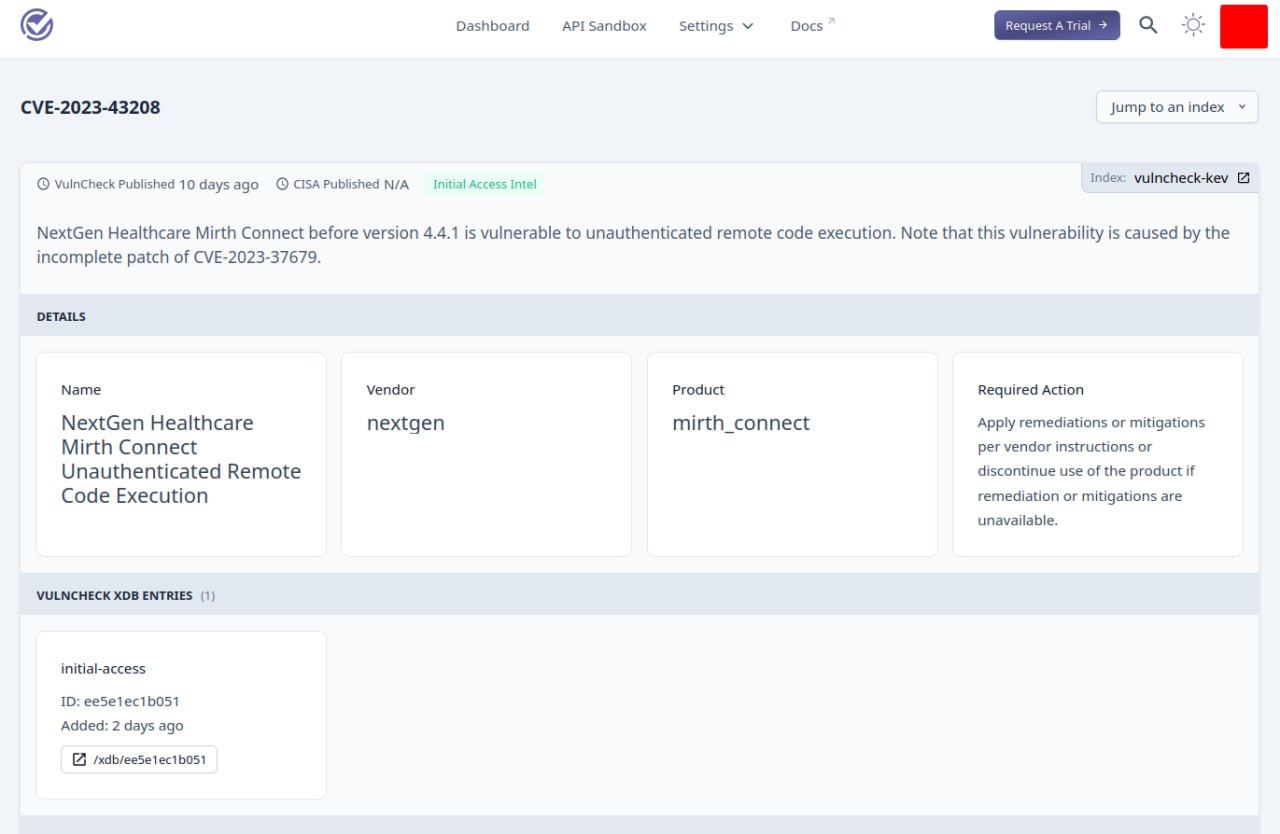
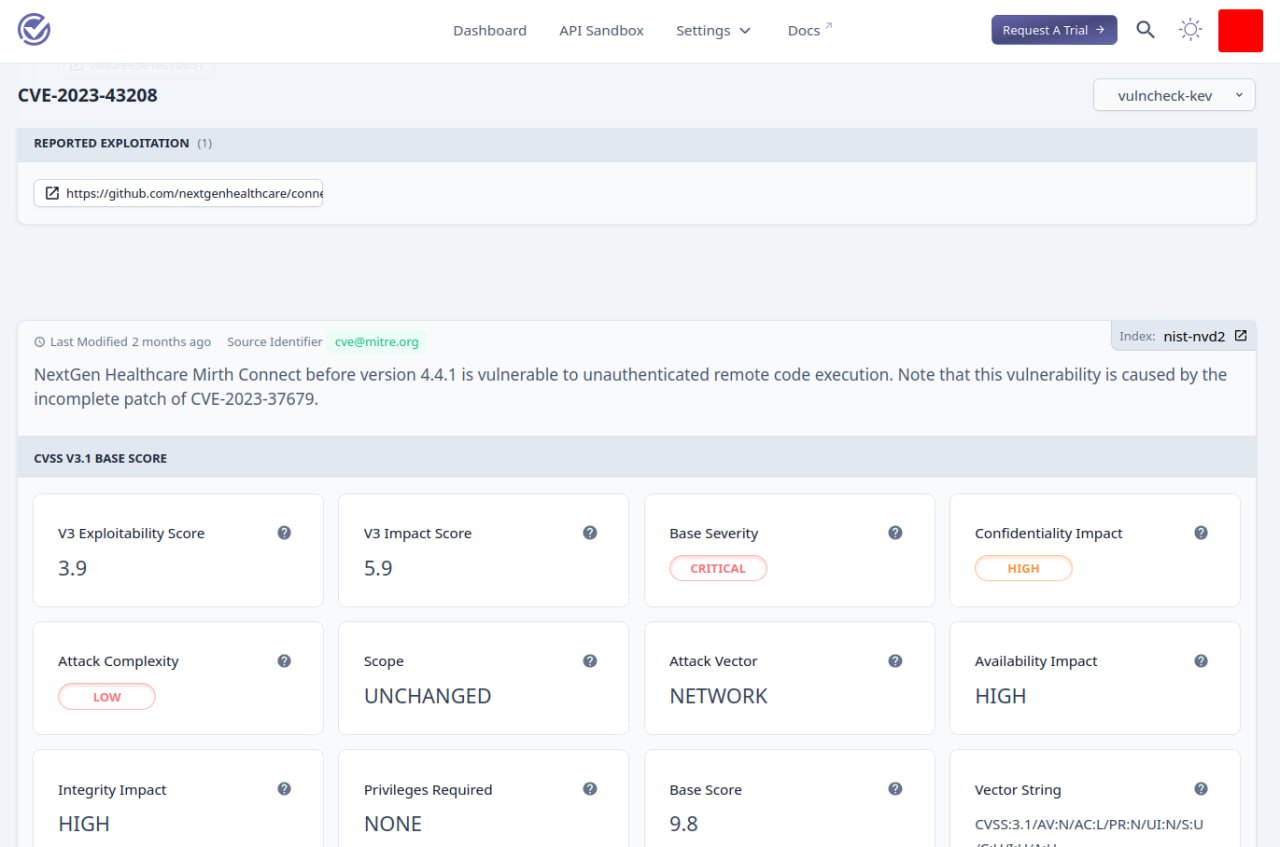
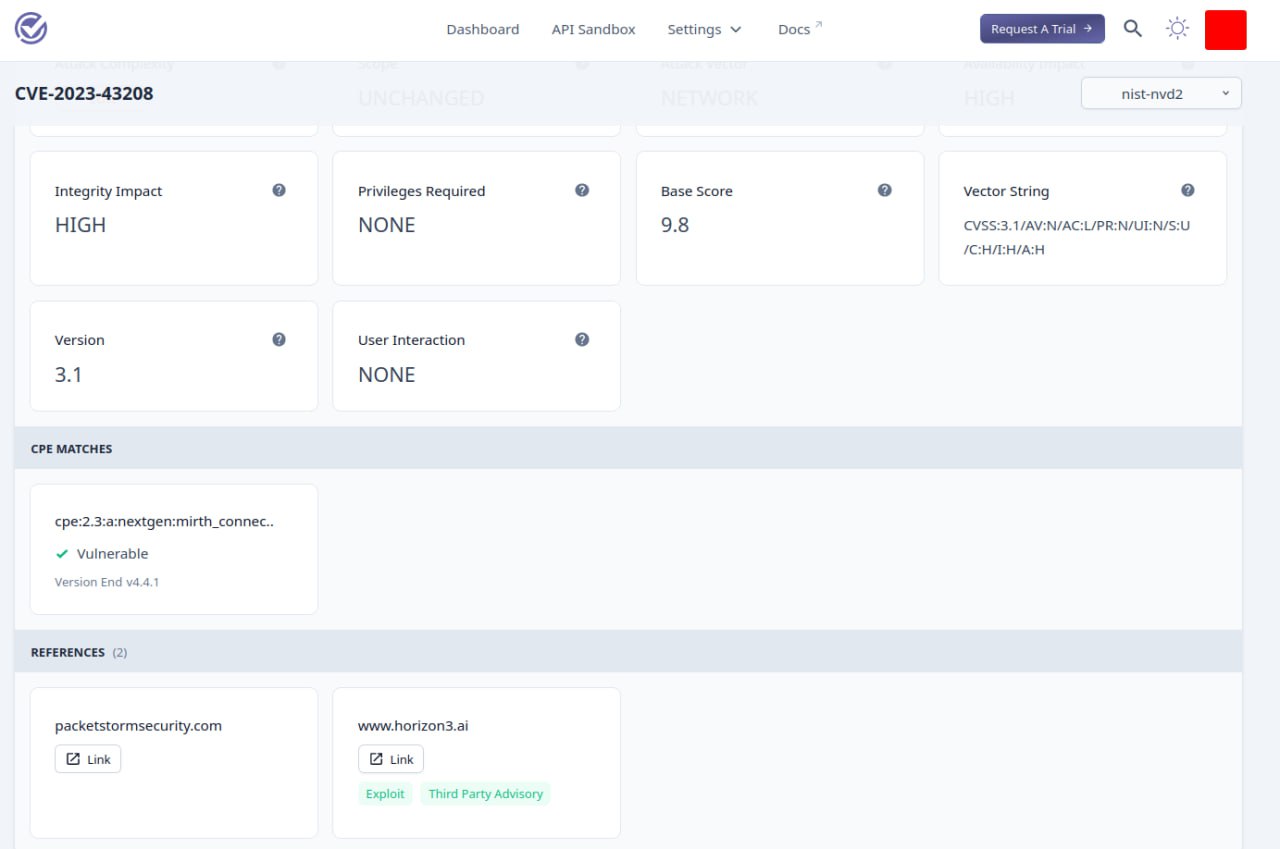
I looked at VulnCheck KEV. This is an analogue of CISA KEV (Know Exploited Vulnerabilities) by VulnCheck.
🔹 Unlike the public CISA KEV, only registered users have access to VulnCheck KEV. The VulnCheck website is accessible from Russian IPs 🇷🇺, but when registering they write that “account is currently under review” (in fact requests are simply blocked 🥸). Requests from non-Russian IPs are registered automatically. 🌝
🔹 There are ~2 times more CVEs in the database than in CISA KEV.
🔹 There are no standard tools for downloading all these CVEs via web-gui. 🤷♂️
🔹 There are links to exploits for CVEs that look good. 👌
🔹 There are signs of exploitation in the wild. Sometimes it’s clear, like “Outbreak Alerts 2023” pdf report. Sometimes it’s strange, like a link to a Shadowserver dashboard or a non-related blog post. 🤷♂️
The selection of CVEs is quite interesting, but the rationale for exploitation in the wild needs to be improved. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

