Vulchain scan workflow and search queries. This post will be about my Vulnerability Scanner project – Vulchain. Recently I’ve spent couple of my weekends almost exclusively on coding: refactoring the scan engine, creating API and GUI.
I was doing it because of the conferences, where I will be speaking soon:
- April 11-13 CyberCentral in Prague. upd. Read about it at “CyberCentral Summit 2018 in Prague“
- April 23–24 CISO Forum. upd. Read about it at “CISO Forum and the problems of Vulnerability Databases”
- May 15–16 PHDays in Moscow. upd. Read about it at “PHDays8: Digital Bet and thousands tons of verbal ore“
Pretty intense schedule for a guy who spends most of his time in PyCharm and Linux console. 😉 Very excited! So, it seemed right to add a couple of slides about my project and show that something is already working.
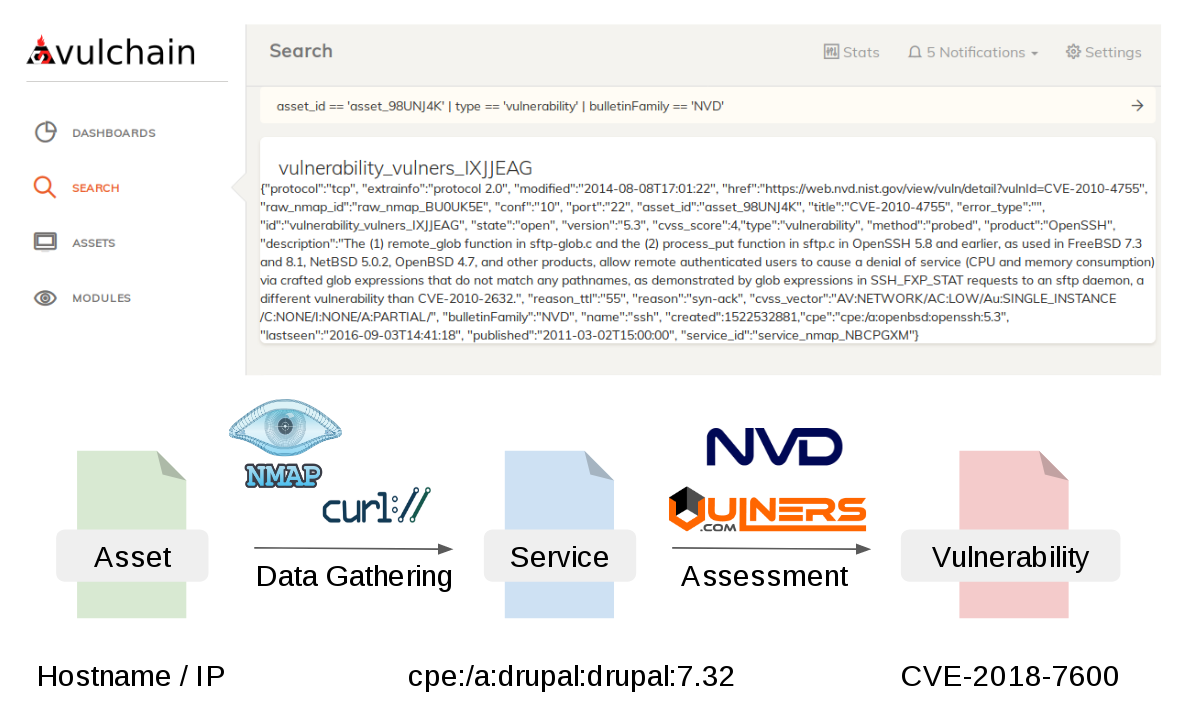
The 5 main principles are still the same. I presented security objects as an independent structures (now it is technically just json files) that are linked hierarchically using some common IDs. Types of security objects that I use right now:
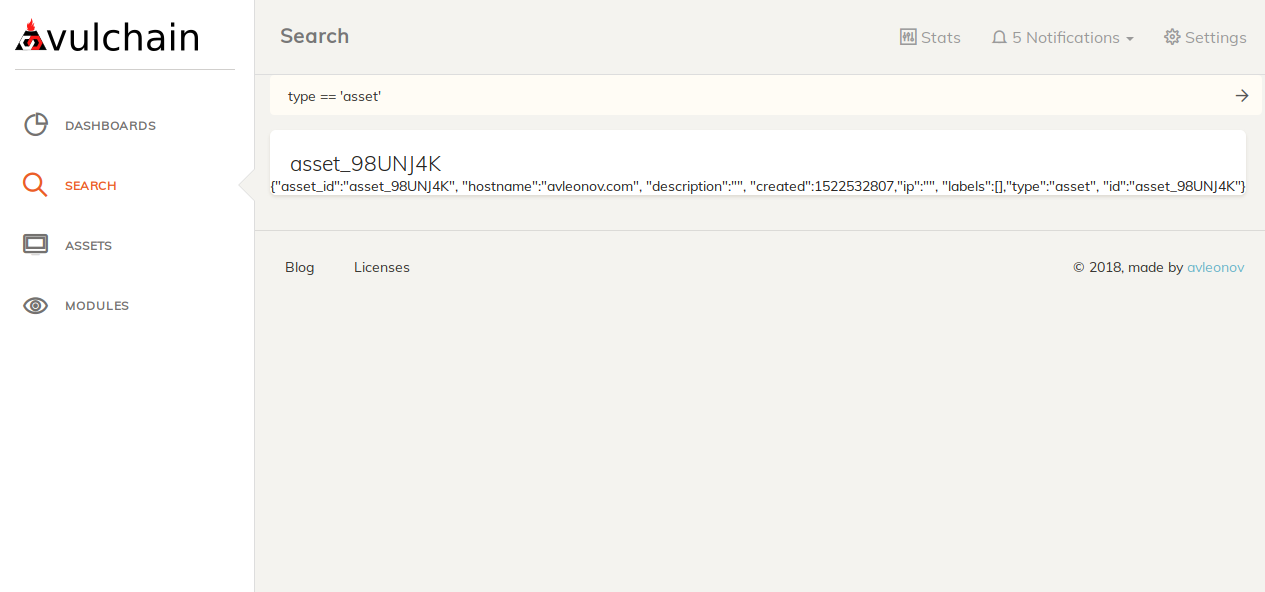
- asset – initial host data ip/hostname
- raw_nmap – result of nmap service detection in json
- raw_http – collected http content and headers if http service_nmap was detected
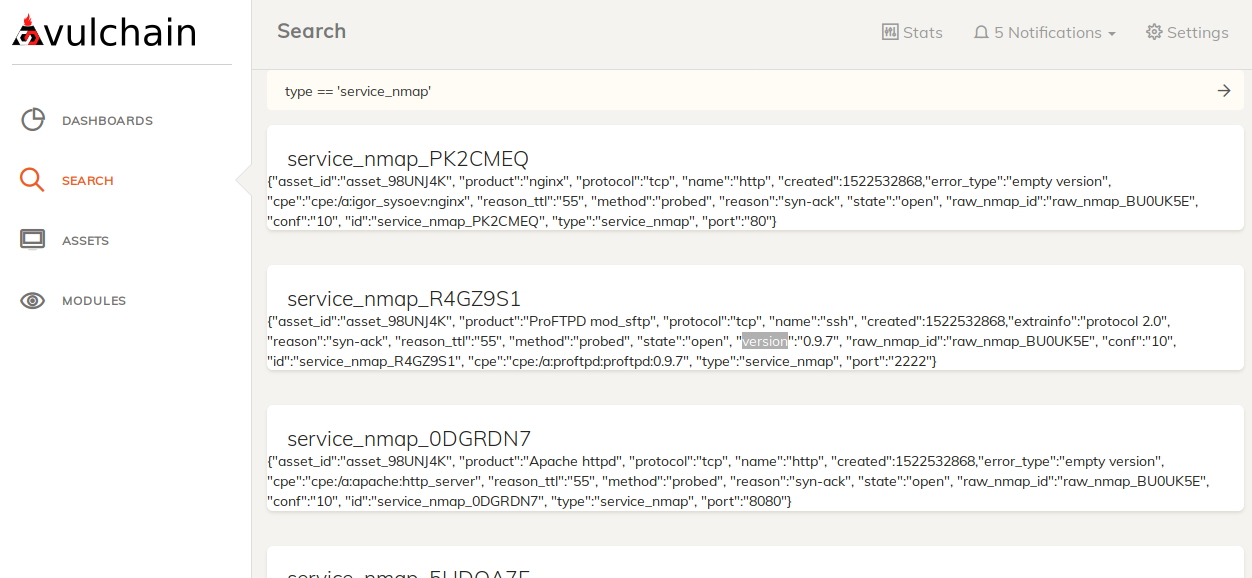
- service_nmap – service detected from raw_nmap data
- service_http – service detected from raw_http data using Vulners detection rules and custom rules
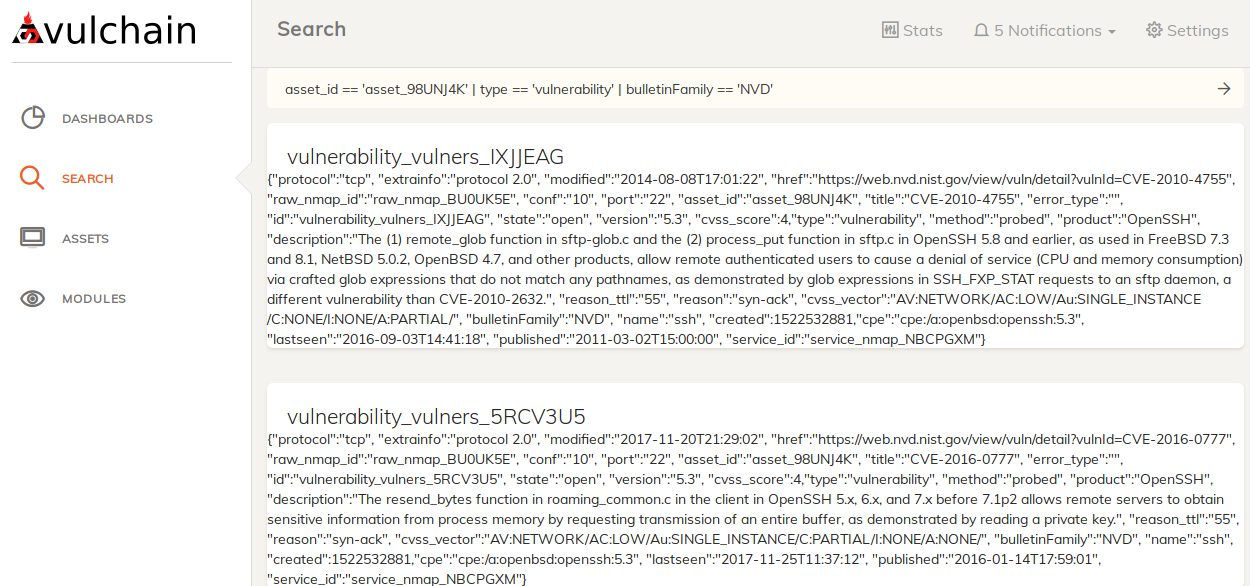
- vulnerability – vulnerability detected from service cpe id using using Vulners Burp API
Each of this objects was created by a separate module, using date of some existing object. There is also a launcher that decides which object can be processed and launches necessary module.
If there is only one Asset object exist, launcher will see that there are no raw_nmap objects related to this Asset. So, it will launch nmap and create such object. On next cycle launcher will see that there are no nmap_service objects related to the raw_nmap object and will create them. In the same manner launcher will create all other objects, including vulnerabilities.
We have this scheme for unauthenticated scan:

And in similar manner we can get vulnerabilities during authenticated Linux scan:

You can read about vulnerability detection using analysis of Linux package versions at “Vulnerability Assessment without Vulnerability Scanner“. There is also Vulners Linux Security Audit API for this.
And all these objects will be collected automatically in a natural way. You can delete some objects and Vulchain will collect all necessary objects once again.
But how the launcher will describe the criteria for necessary objects? I could use requests in something like Apache Lucene syntax, that Vulners uses. But I don’t like it. I decided to make search mechanism that can be used in scripts, API and GUI. With the pipes ^ _ ^ Almost like Splunk or bash, lol.
So, I can list all assets with `type == 'asset'`:
Or list all nmap services with `type == 'service_nmap'`:
And here are vulnerabilities for asset `asset_id == 'asset_98UNJ4K' | type == 'vulnerability' | bulletinFamily == 'NVD'`:
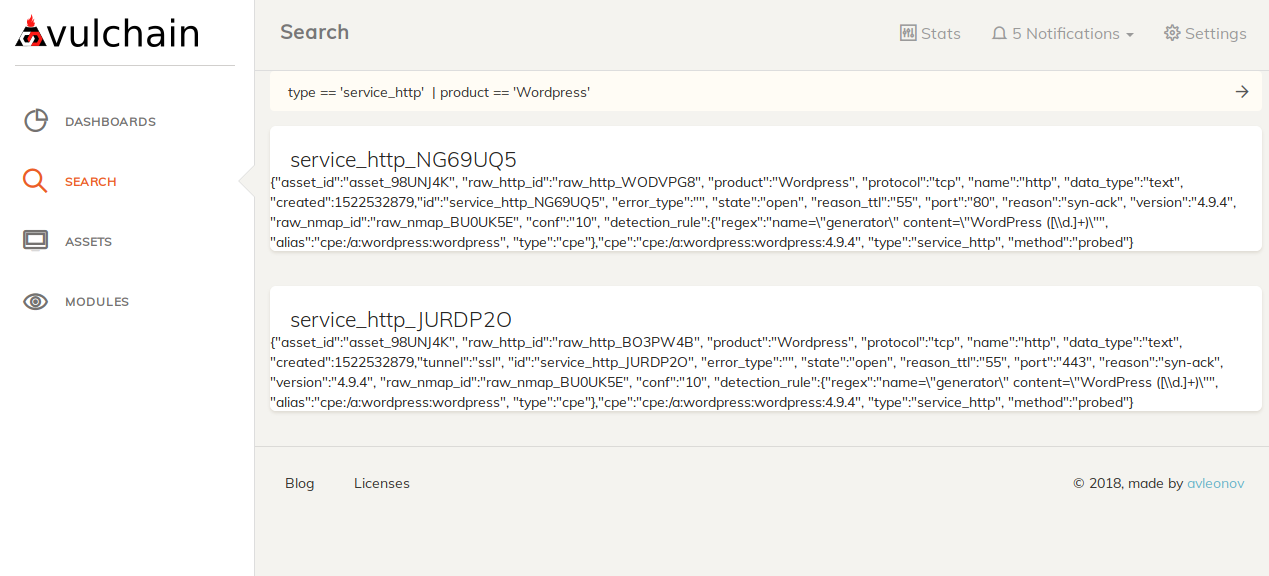
Here are all detected WordPress sites `type == 'service_http' | product == 'Wordpress'`
Right now the output looks ugly, but I plan to do a beautiful rendering for each type of object. And I also make widgets for assets based on the same search engine. Stay tuned.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: PHDays8: Digital Bet and thousands tons of verbal ore | Alexander V. Leonov