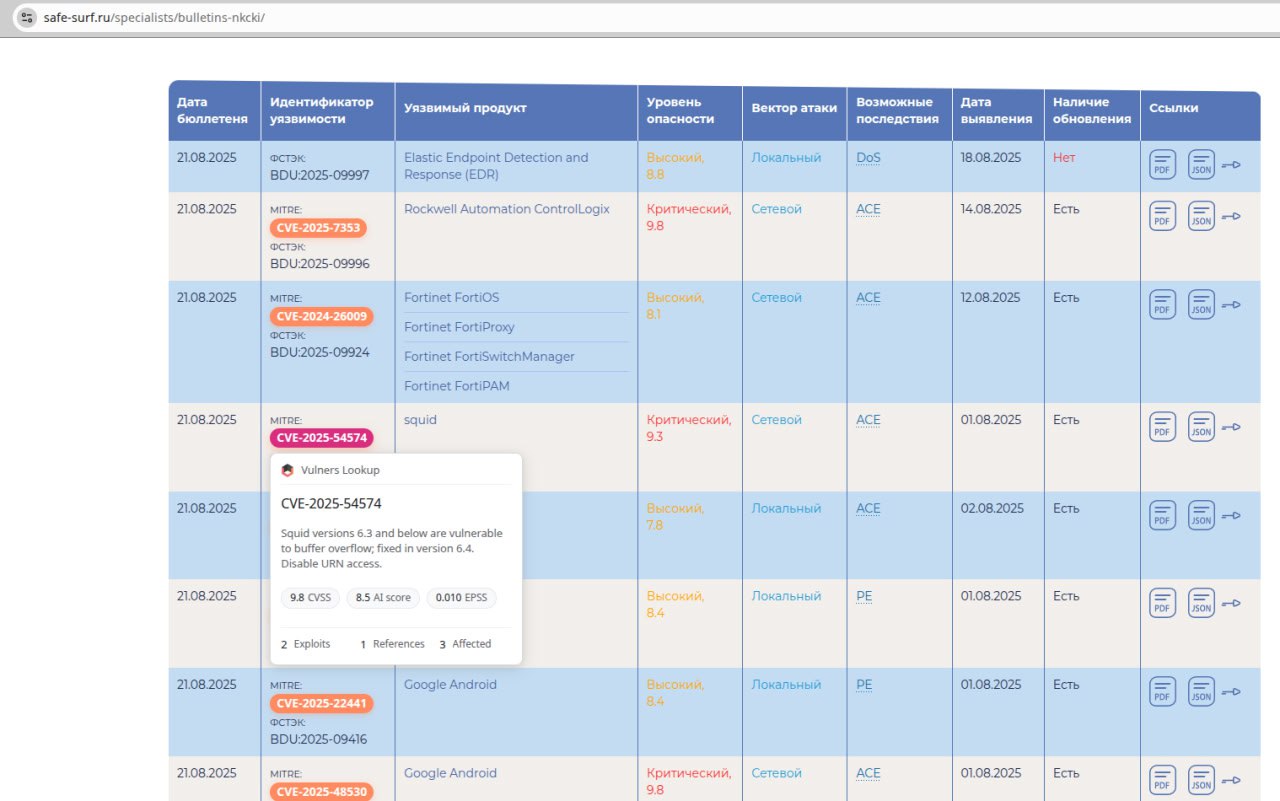
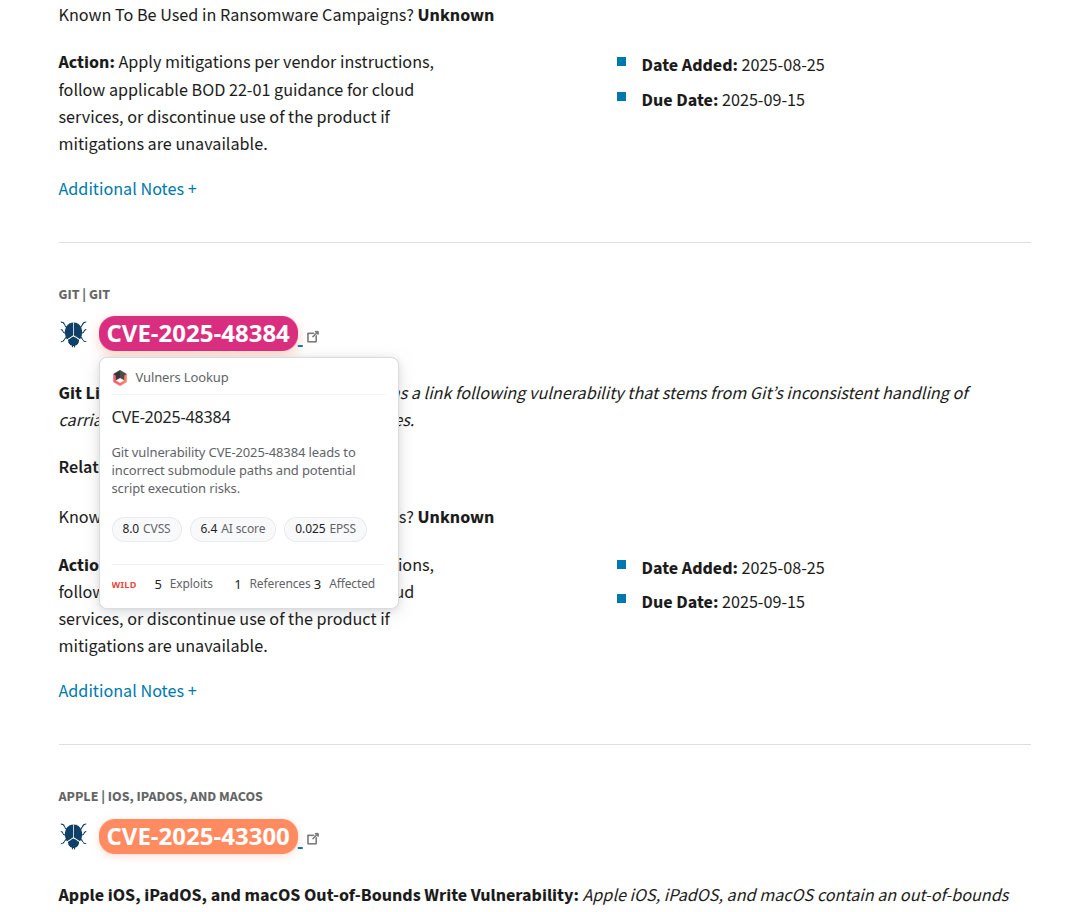
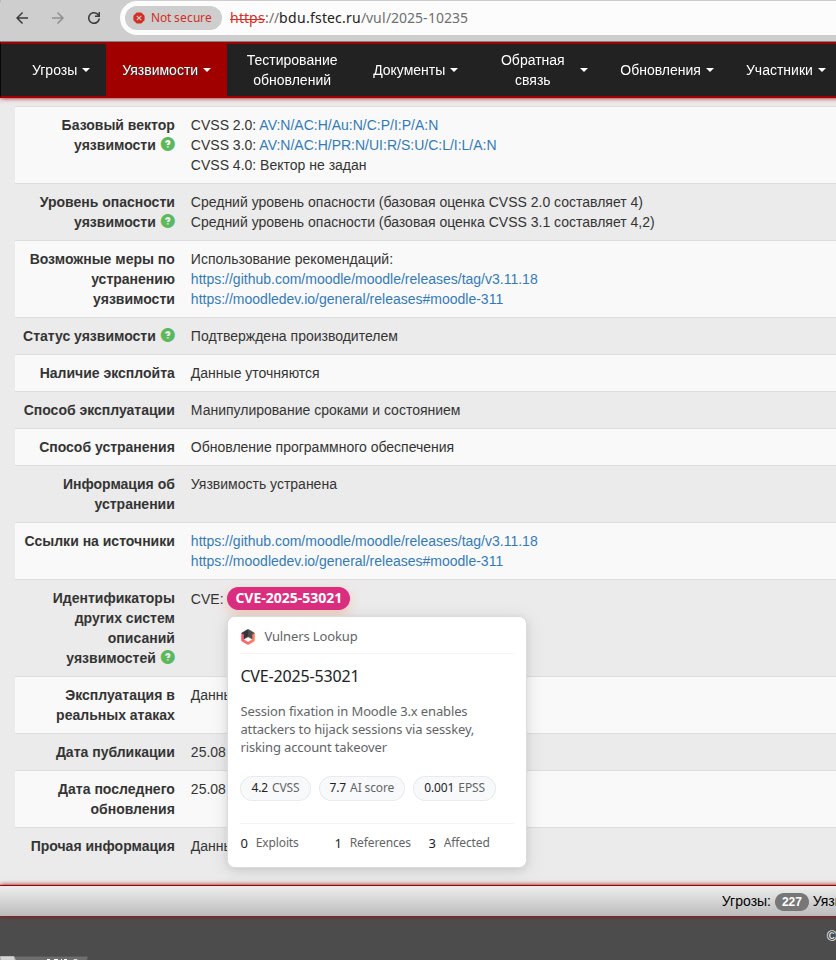
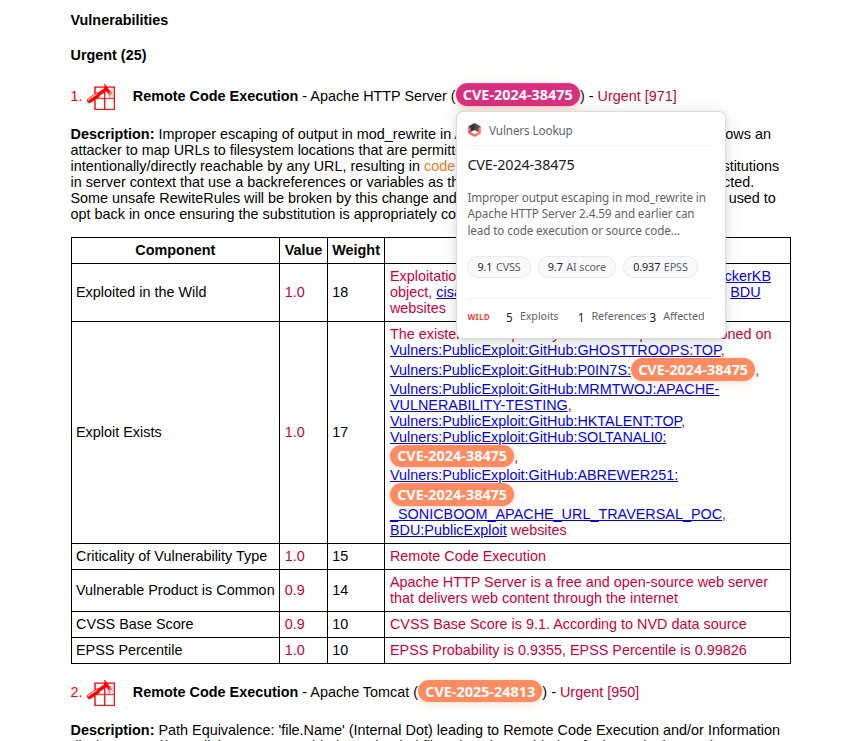
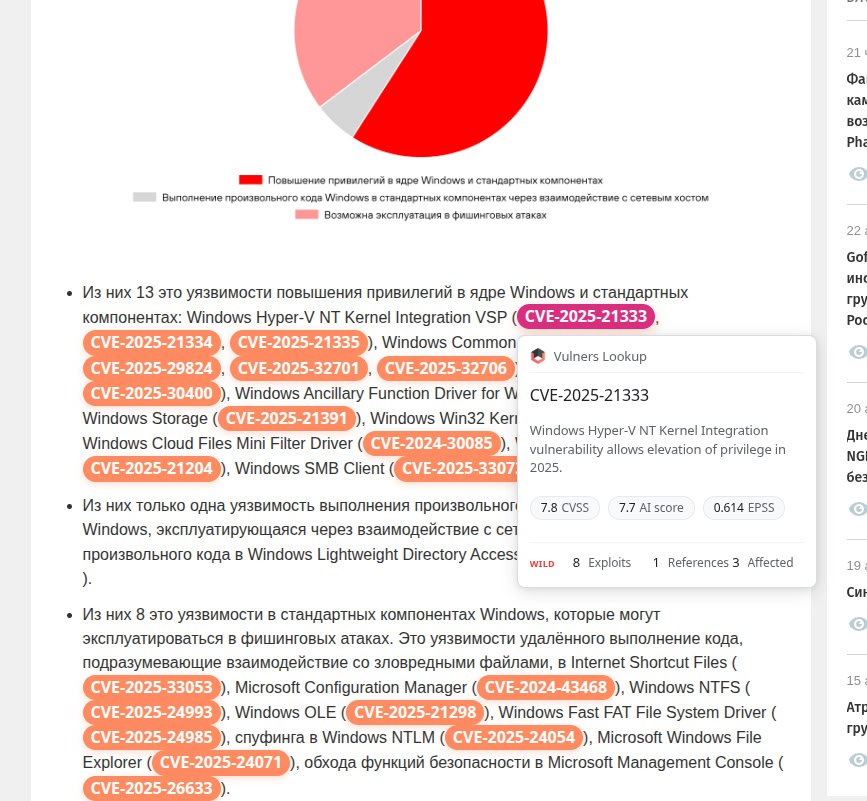
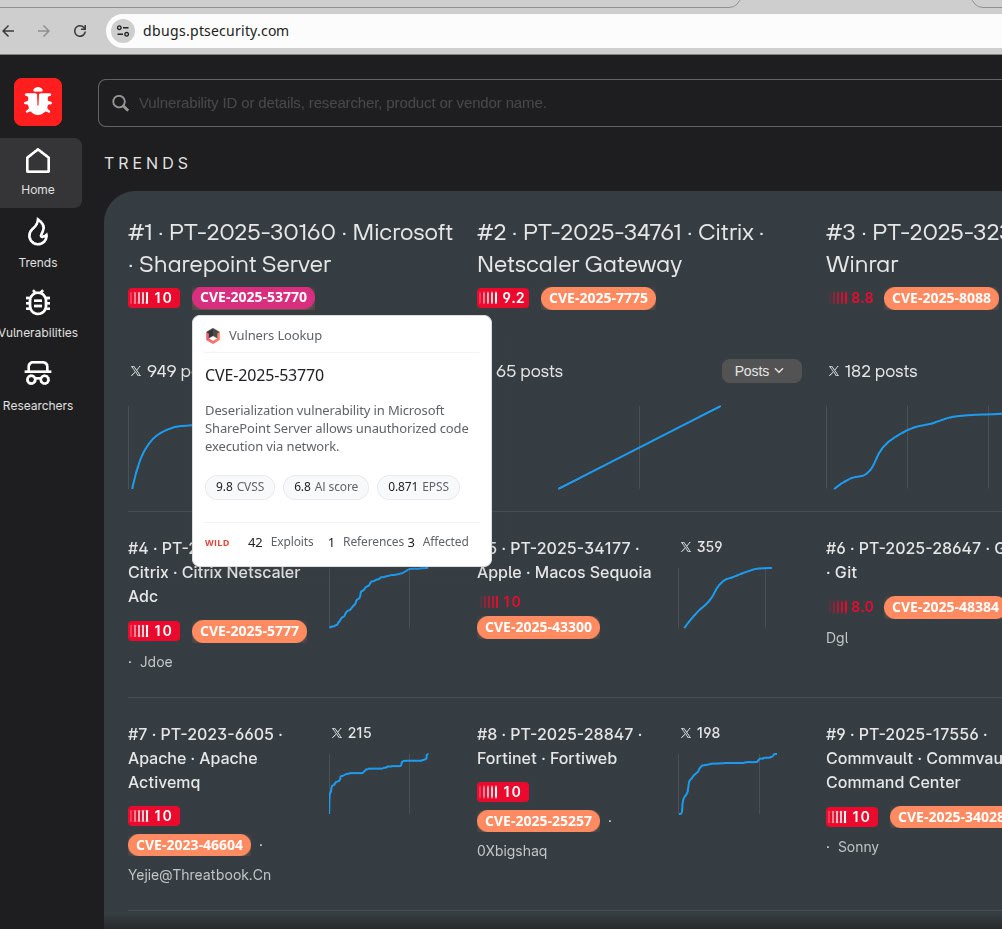
About Remote Code Execution – SAP NetWeaver (CVE-2025-31324, CVE-2025-42999) vulnerability. SAP NetWeaver is the core SAP platform for running applications and integrating systems. Vulnerabilities were found in its Visual Composer component – a web tool for business app modeling. A lack of authorization checks (CVE-2025-31324) and insecure deserialization (CVE-2025-42999) allows unauthenticated attackers to perform remote code execution and compromise SAP systems, data, and processes.
🩹 The vulnerabilities were fixed by SAP in April and May 2025.
👾 On May 13, Onapsis researchers reported that CVE-2025-31324 had been exploited since February 10. The CVEs were added to CISA KEV on April 29 and May 15.
🛠 PoCs for CVE-2025-31324 began appearing on GitHub in late April. A public exploit combining CVE-2025-31324 and CVE-2025-42999 was reported by Onapsis on August 15.
📊 According to estimates, SAP products are still used by around 2,000 Russian organizations.