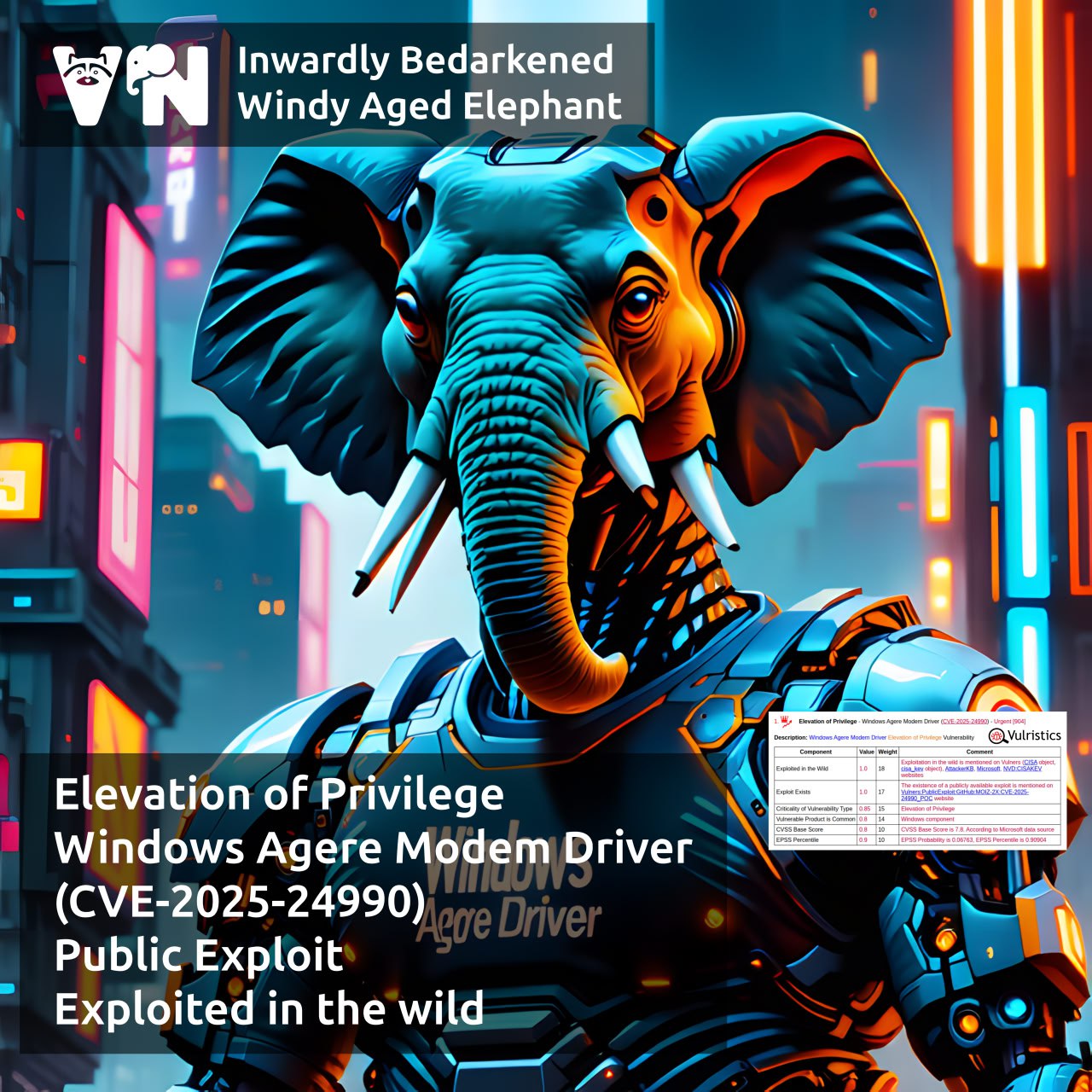
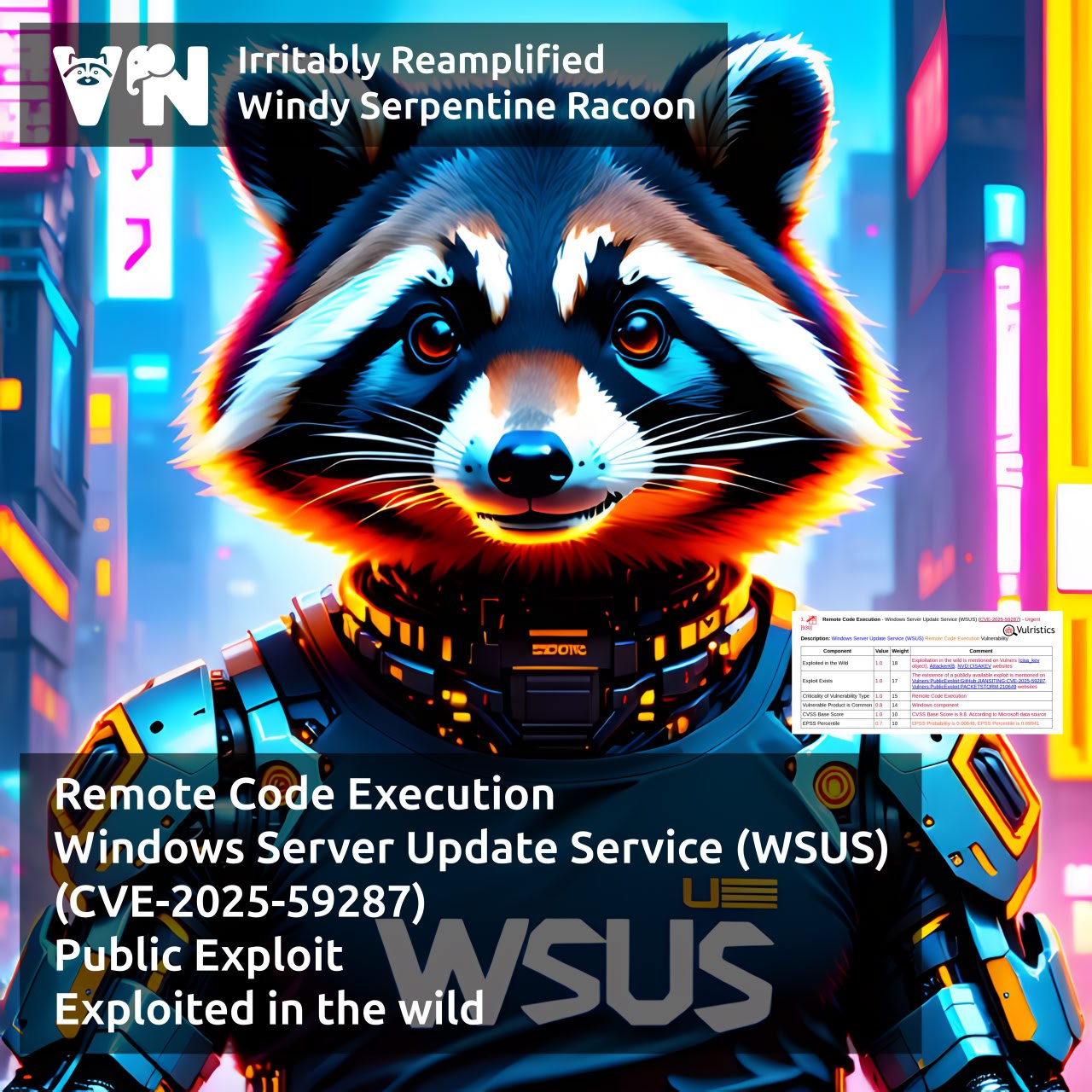
About Remote Code Execution – XWiki Platform (CVE-2025-24893) vulnerability. XWiki is a free and open-source wiki platform written in Java, with a strong focus on extensibility. It supports WYSIWYG visual editing, importing and exporting documents in OpenDocument format, adding annotations and tags, as well as flexible access rights management. The vulnerability allows an attacker with guest-level privileges to execute arbitrary code on the server by sending a crafted SolrSearch request.
⚙️ The vulnerability was fixed in versions 15.10.11, 16.4.1 and 16.5.0RC1, released in July 2024.
🛠 A proof-of-concept (POC) exploit was available in the original task to fix ZDI-CAN-23994, as well as in the security bulletin published on February 20, 2025. There are now more than 30 exploit variants on GitHub.
👾 On October 28, VulnCheck reported that the vulnerability was being exploited in the wild to deploy cryptominers. On October 30, it was added to the CISA KEV catalog.