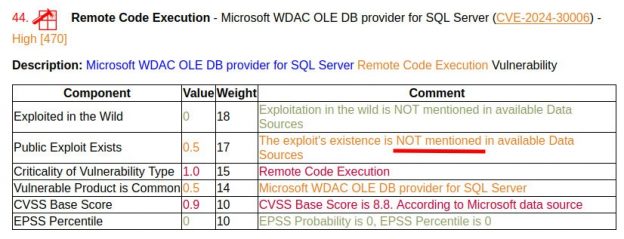
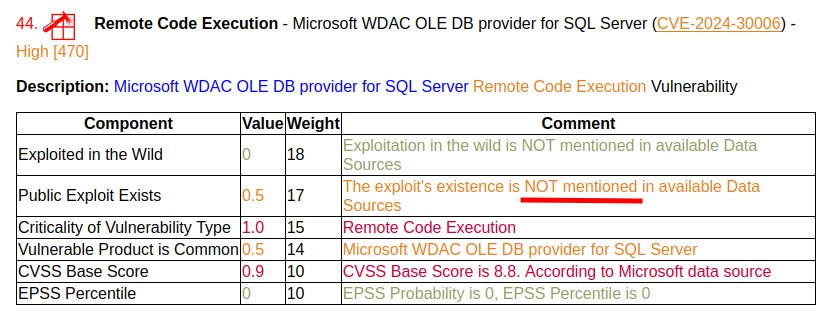
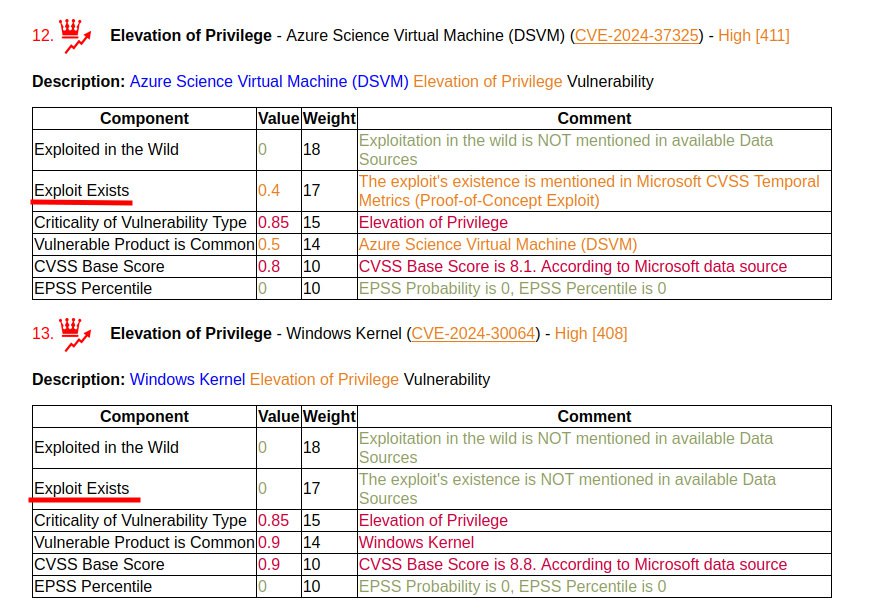
June Microsoft Patch Tuesday. There are 69 vulnerabilities in total, 18 of which were added between May and June Patch Tuesday. Among these added were 2 vulnerabilities with signs of exploitation in the wild:
🔻 Remote Code Execution – Chromium (CVE-2024-5274, CVE-2024-4947). Both vulnerabilities are in CISA KEV; there are no exploits for them yet.
For the remaining vulnerabilities, there are no formal signs of exploitation in the wild or public exploits yet.
The specialized InfoSec media pay attention to these 2:
🔸 Remote Code Execution – Microsoft Message Queuing (MSMQ) (CVE-2024-30080). This vulnerability has a high CVSS Score of 9.8. To get RCE, the attacker sends a specially crafted malicious packet to the MSMQ server. The vulnerability may well become wormable for Windows servers with MSMQ enabled. It is very similar to last year’s QueueJumper (CVE-2023-21554).
🔸 Denial of Service – DNSSEC (CVE-2023-50868). Vulnerability in DNSSEC validation. An attacker can cause DoS using standard DNS integrity protocols. 🤷♂️ I don’t see any super criticality, but this is rare for MS Patch Tuesday, which is probably why everyone is writing about it.
What else you can pay attention to:
🔸 Elevation of Privilege – Windows Win32k (CVE-2024-30091), Windows Kernel (CVE-2024-30088, CVE-2024-30099) and Windows Cloud Files Mini Filter Driver (CVE-2024-30085). Why these? Microsoft’s CVSS states that there are private Proof-of-Concept exploits for them.
🔸 Remote Code Execution – Microsoft Office (CVE-2024-30101). This is a Microsoft Outlook vulnerability. To successfully exploit this vulnerability, a user must open a malicious email in an affected version of Microsoft Outlook and then perform certain actions to trigger the vulnerability. It’s enough to open the email in the Preview Pane. However, to successfully exploit this vulnerability, an attacker needs to win the race condition.
🔸 Remote Code Execution – Microsoft Outlook (CVE-2024-30103). Preview Pane is a vector. Authentication required. The vulnerability is somehow related to the creation of malicious DLL files. 🤷♂️
🔸 Remote Code Execution – Windows Wi-Fi Driver (CVE-2024-30078). An attacker can execute code on a vulnerable system by sending a specially crafted network packet. The victim must be within the attacker’s Wi-Fi range and use a Wi-Fi adapter. Sounds interesting, let’s wait for details. 😈
🔸 Remote Code Execution – Microsoft Office (CVE-2024-30104). An attacker must send the user a malicious file and convince the user to open the file. The Preview Pane is NOT an attack vector.