Big Microsoft day: EOL for Win7, Win2008 and crypt32.dll. Big Microsoft day. End-of-life for Windows 7 desktops and Windows 2008 servers (strictly speaking Windows Server 2008 R2). I think that today many security guys had a fun task to count how many host hosts with win7 and win2008 they still have in the organization. So, Asset Management is a necessity! ?
Now an interesting time should begin, when critical unpatched vulnerabilities may appear for these operation systems. At the same time, the number of hosts with Windows 7 and Windows 2008 will be still big enough for massive attacks. ? Although I think that Microsoft will continue to release patches for the most critical vulnerabilities, like they did it for WinXP. Upd. Also note, that for Windows Server 2008/2008r2 it’s also possible to purchase an extended three years security update subscription.
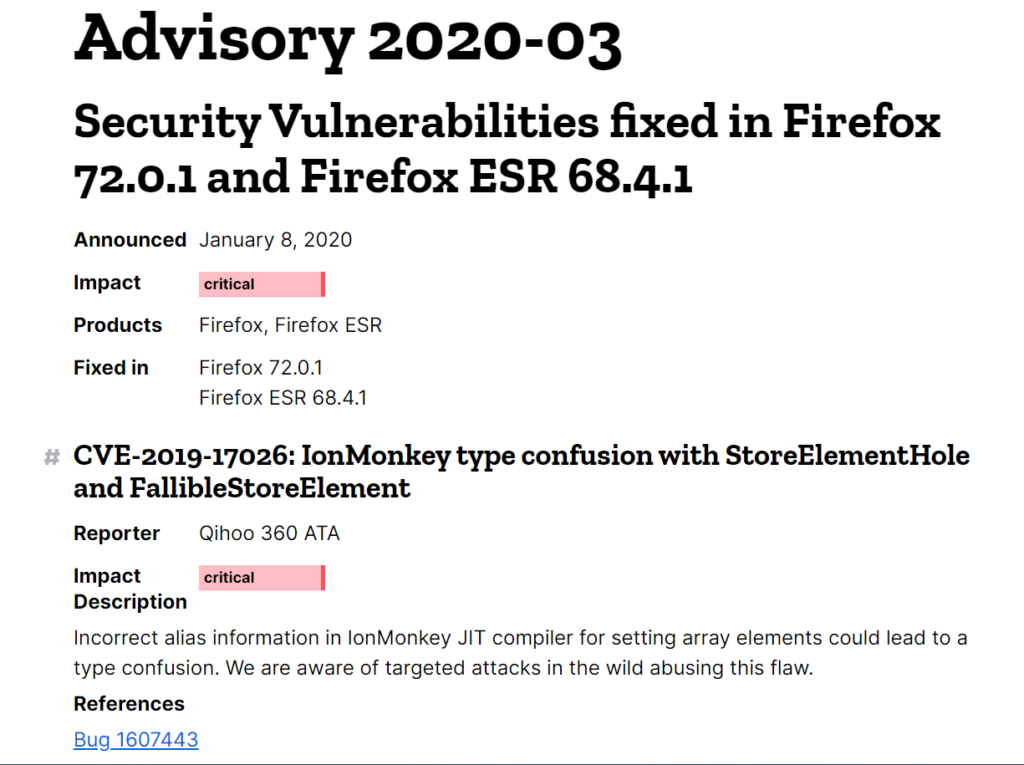
The second interesting topic is the mysterious vulnerability in crypt32.dll (this dll appeared in Windows more than 20 years ago), which might somehow affect authentication and digital signatures in Windows.
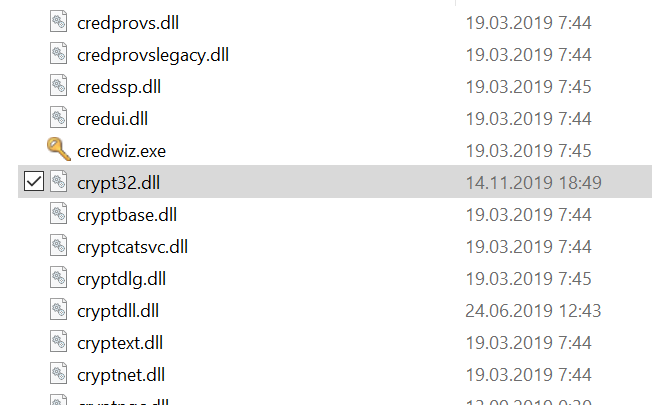
Far now it has been only a rumor, but soon it will become clear how dangerous it is and how it can be used.
upd. 15.01. So, what about this vulnerability in crypt32.dll. Now it has the name NSACrypt (because NSA reported it) and the id CVE-2020-0601. It’s not for all versions of Windows, only for Windows 10, Windows Server 2016 and Windows Server 2019.